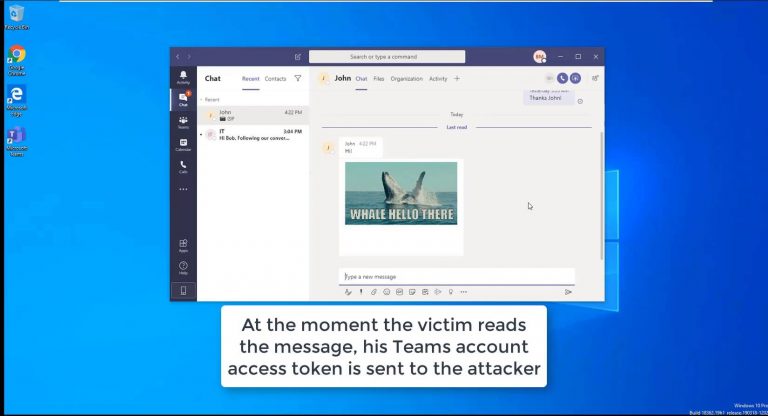
Experts discovered how to take over Microsoft Teams accounts by just sending recipients a regular GIF, it works for both desktop and web Teams versions. Microsoft has addressed a vulnerability in Teams workplace video chat and collaboration platform that could have allowed attackers to take Team accounts by sending participants […]
Online credit card skimming increased by 26 percent in March
Crisis events such as the current COVID-19 pandemic often lead to a change in habits that captures the attention of cybercriminals. With the confinement measures imposed in many countries, for example, online shopping has soared and along with it, credit card skimming. According to our data, web skimming increased by 26 percent in […]
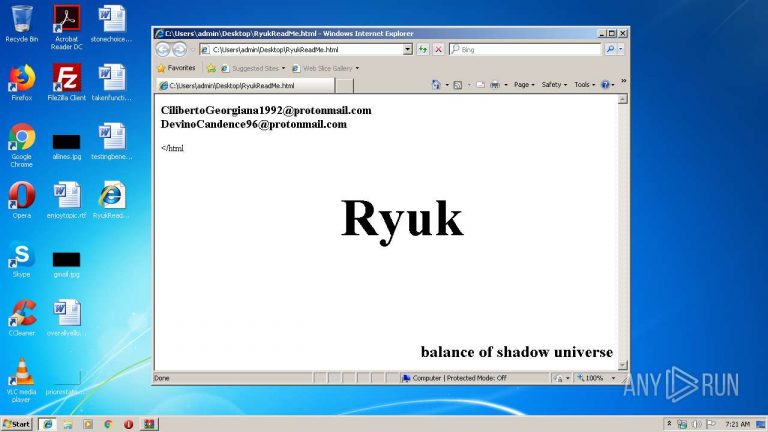
Ryuk Ransomware Keeps Targeting Hospitals During the Pandemic
The Ryuk Ransomware operators to continue to target hospitals even as these organizations are overwhelmed during the Coronavirus pandemic. Last week BleepingComputer contacted various ransomware groups and asked if they would target hospitals and other healthcare organizations during the pandemic. With the amount of strain healthcare organizations are under during this pandemic, […]
Exploitation massive d’une faille Zero-Day au niveau de Windows 7
Microsoft a récemment publié une alerte pour tous les utilisateurs de Windows concernant une vulnérabilité grave qui est train d’être exploitée pour lancer des attaques. Cette vulnérabilité zero-day menace principalement les utilisateurs de Windows 7. NB : Une faille zero-day, est une faille qui est présente dans un système, mais […]
Microsoft Leaks Info on Wormable Windows SMBv3 CVE-2020-0796 Flaw
Critical bug in Microsoft’s SMBv3 implementation published under mysterious circumstances. Word leaked out on Tuesday of a new vulnerability in recent versions of Windows that has the potential to unleash the kind of self-replicating attacks that allowed the WannaCry and NotPetya worms to cripple business networks around the world. The […]
L’ANSI lève le niveau d’alerte national à “Critique” en cybersécurité
L’Agence Nationale de Sécurité Informatique (ANSI) a levé son niveau d’alerte national pour la sécurité des réseaux de très élevée à critique et ce, suite à une recrudescence des attaques sur le réseau national. Le dernier en date : une attaque d’une très grande envergure d’un Ransomware sur le réseau […]
En savoir plus sur Snake Ransomware
Le Ransomware ou rançonnage informatique sera probablement le plus grand danger qui menacera les réseaux informatiques de nombreux organismes dans le monde cette année 2020. Le virus Snake Ransomxare, très sophistiqué est l’arme de prédilection des hackers. Municez-vous de logiciels aussi performants comme Audemail ou Altospam pour protéger vos e-mails […]
Install Latest Chrome Update to Patch 0-Day Bug Under Active Attacks
Google yesterday released a new critical software update for its Chrome web browser for desktops that will be rolled out to Windows, Mac, and Linux users over the next few days. The latest Chrome 80.0.3987.122 includes security fixes for three new vulnerabilities, all of which have been marked ‘HIGH’ in severity, […]
Croatia’s largest petrol station chain impacted by cyber-attack
A security incident described as « a cyber-attack » has crippled some business operations at INA Group, Croatia’s biggest oil company, and its largest petrol station chain. The attack took place last Friday, on February 14, at 22:00, local time, the company said. Multiple sources have told ZDNet the cyber-attack is a […]
Google removes 600 Android apps in Play Store adware crackdown
Google laid out today a plan to crack down on abusive Android developers who break app store rules by showing out-of-app ads. The term of out-of-app ads refers to ads that originate from one app but appear on top of other apps, or the device’s home screen, being unclear to […]