Les pirates informatiques ont inventé une méthode qui est très efficace pour piéger leurs victimes. Il s’agit d’un nouveau phishing qui consiste à diriger leurs proies vers de sites imaginaires via leurs recherches sur Google. Le géant Microsoft a reconnu que c’est la dernière technique favorite des hackers qui ne […]
Des distributeurs automatiques de billets en Europe attaqués par des virus
Actuellement, un nouveau virus a été détecté dans les distributeurs automatiques de billets en Europe. Selon les chiffres reçus, des centaines de distributeurs ont été touchés par cette attaque. Il s’avère qu’un logiciel injecté dans l’appareil peut forcer celui-ci à expulser des dizaines de billets. Ces derniers jours, les banques […]
le Nigéria et autres pays africains sous la menace d’une cyberattaque bancaire
La plus grande économie d’Afrique, le Nigeria, aux côtés d’autres pays d’Afrique subsaharienne, est désormais la cible d’attaques d’un groupe de piratage russe, ont révélé des enquêtes menées par des chercheurs de Kaspersky Lab, un fournisseur multinational de cybersécurité et d’antivirus, mais aussi ont signalé des milliers de notifications alarmantes d’attaques contre les principales banques d’Afrique subsaharienne.
Android : le Bluetooth est victime d’une énorme faille de sécurité, mettez votre smartphone à jour !
Une énorme faille de sécurité a été découverte dans la fonctionnalité Bluetooth d’Android. Cette faille peut permettre à des pirates à proximité de voler des données personnelles et propager des malwares sans qu’aucune action de l’utilisateur ne soit requise. Google a corrigé cette faille dans son patch cumulatif de février […]
ONU piraté due à une vulnérabilité dans SharePoint
L’ONU n’a pas divulgué publiquement une attaque de piratage majeure dans ses systèmes informatiques en Europe – une décision qui pourrait mettre le personnel, d’autres organisations et des individus en danger, selon les défenseurs de la protection des données. Le 30 août 2019, des responsables informatiques travaillant dans les bureaux […]
le ransomware Sodinokibi frappe encore, Travelex ammené à payer 3 M$
Le spécialiste en échanges de devises internationales Travelex a été touché par le ransomware Sodinokibi. Depuis le 31 décembre 2019 tous ses services en ligne sont inaccessibles. Le paiement d’une rançon de 3 millions de dollars aurait été demandée.
La grande compétition « Capture The Flag » de TT
La grande compétition « Capture The Flag » de TT TT et Keystone vous invitent à participer au grand challenge CTF qui aura lieu du 15 au 16 Janvier , 24 heures non-stop. Il s’agit d’une opportunité pour valoriser votre talent en matière de cyber-sécurité, s’affronter aux meilleures équipes tunisiennes et gagner […]
Citrix NetScaler/ADC Critical Flaw (CVE-2019-19781)
Vulnerability Description Citrix has indicated that an unauthenticated attacker can exploit this flaw to perform arbitrary code execution. Although details from Citrix are minimal, VERT’s research has identified three vulnerable behaviors which combine to enable code execution attacks on the NetScaler/ADC appliance. These flaws ultimately allow the attacker to bypass […]
Android’s January 2020 Update Patches 40 Vulnerabilities
Google on Monday published the first Android security bulletin for 2020, with patches for 40 vulnerabilities, including a critical flaw in the Media framework. The Android Security Bulletin for January 2020 was split into two parts: the first addresses 7 vulnerabilities in Framework, Media framework, and System, while the second includes fixes […]
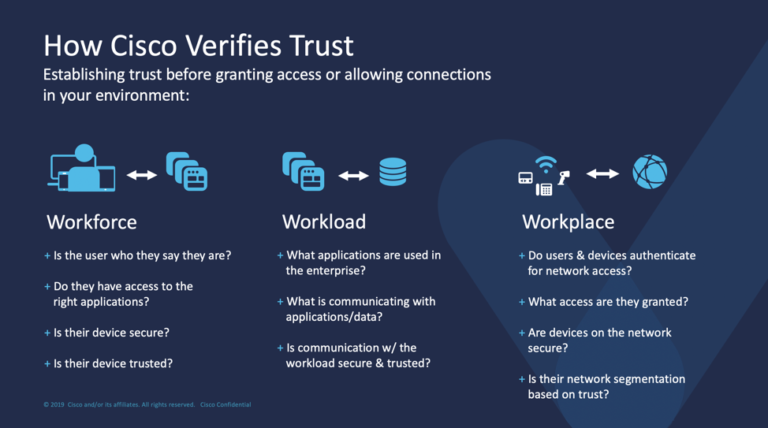
An Overview of Zero Trust Architecture, According to NIST
NIST recently released a draft publication, SP 800-207: Zero Trust Architecture (ZTA), an overview of a new approach to network security. While ZTA is already present in many cybersecurity policies and programs that sought to restrict access to data and resources, this document is intended to both “abstractly define” ZTA and […]