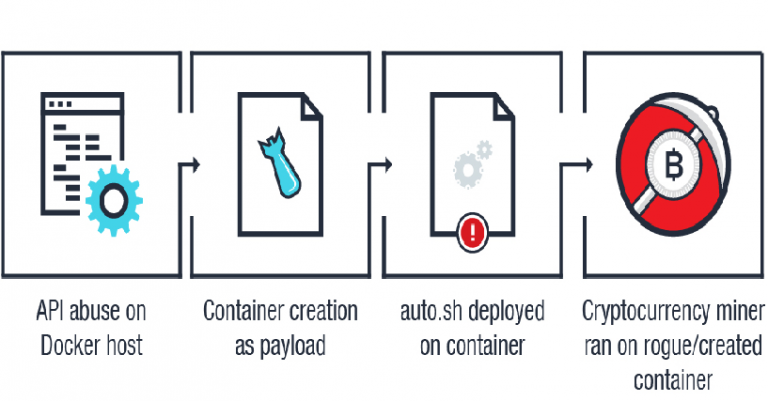
Cybercriminals continue to abuse unprotected Docker APIs to create new containers used for cryptojacking, Trend Micro warns. Crooks continue to abuse unprotected Docker APIs to create new containers used for cryptojacking. Earlier this year Sysdig and Aqua Security researchers started observing cyber attacks targeting Kubernets and Docker instances aimed at mining Monero cryptocurrency. A […]
Hacking
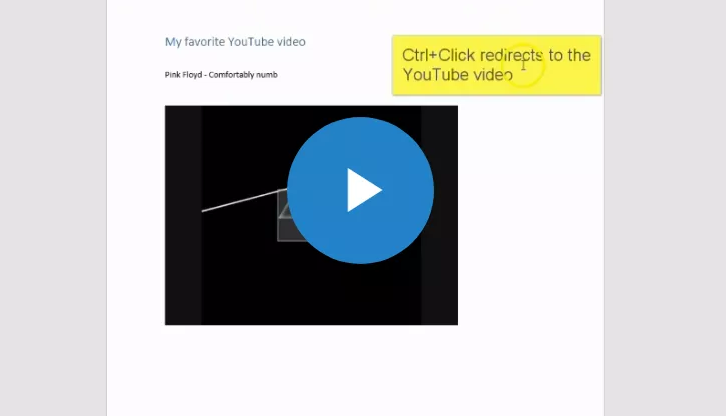
How to deliver malware using weaponized Microsoft Office docs embedding YouTube video
Researchers at Cymulate security firm devised a new stealthy technique to deliver malware leveraging videos embedded into weaponized Microsoft Office Documents. The technique could be used to execute JavaScript code when a user clicks on a weaponized YouTube video thumbnail embedded in a Weaponized Office document. Experts pointed out that […]
Cybercriminals stole 2.8 million dollars from Russians with the help of fake websites
Since the beginning of this year, hackers stolen 3.8 million dollars from Russians using web phishing. This is 6% more than last year. Experts believe that web phishing is the easiest and most effective way to steal money, as people are increasingly using Bank cards. Scammers create fake websites that […]
New FilesLocker Ransomware Offered as a Ransomware as a Service
A new ransomware called FilesLocker is being distributed as a Ransomware as a Service, or RaaS, that targets Chinese and English speaking victims. This ransomware was first spotted by MalwareHunterTeam who posted about it on Twitter. At the time, it looked like your standard small little C# ransomware with little or no distribution. It turns […]
Malware Distributors Adopt DKIM to Bypass Mail Filters
In July 2018, US-CERT raised an alert regarding the Emotet banking trojan, which is also being used to distribute a secondary malware known as “Trickbot”. This alert provided recommendations on how businesses can mitigate their exposure to the Trojan. Unfortunately, it looks like criminals are also reading the US-CERT’s warnings as […]
Banking Trojans continue to surface on Google Play
The malicious apps have all been removed from the official Android store but not before the apps were installed by almost 30,000 users Malware authors keep testing the vigilance of Android users by sneaking disguised mobile banking Trojans into the Google Play store. We’ve recently analyzed a set of 29 […]
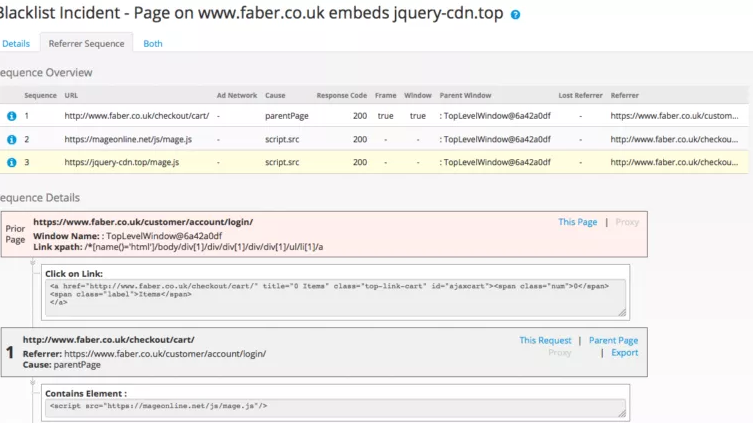
Magecart hackers change tactic and target vulnerable Magento extensions
Magecart cybercrime gang made the headlines again, the cyber criminal gang is now targeting vulnerable Magento Extensions. Magecart cybercrime gang switches tactic, it is now targeting vulnerable Magento extensions. instead of compromising large websites or third-party services to steal credit card data. In previous campaigns, attackers customize the attack for each victim tailoring the code […]
Chalubo, a new IoT botnet emerges in the threat landscape
Security experts from Sophos Labs have spotted a new piece of IoT malware tracked as Chalubo that is attempting to recruit devices into a botnet used to launch DDoS attacks. Security experts from Sophos Labs have spotted a new piece of Linux malware tracked as Chalubo (ChaCha-Lua-bot) that is targeting IoT devices in an […]
Signal Desktop Leaves Message Decryption Key in Plain Sight
A mistake in the process used by the Signal Desktop application to encrypt locally stored messages leaves them wide open to an attacker. When Signal Desktop is installed, it will create an encrypted SQLite database called db.sqlite, which is used to store the user’s messages. The encryption key for this database is automatically generated […]
Firefox Targeting Competing VPN Sites With ProtonVPN Offer in New Test
Mozilla has announced a Shield study where Firefox will promote the ProtonVPN service as a new revenue source. BleepingComputer was able to gain access to the study’s extension and it appears that the ProtonVPN will be recommended when visiting VPN provider sites, streaming services, or when connecting to insecure wireless […]