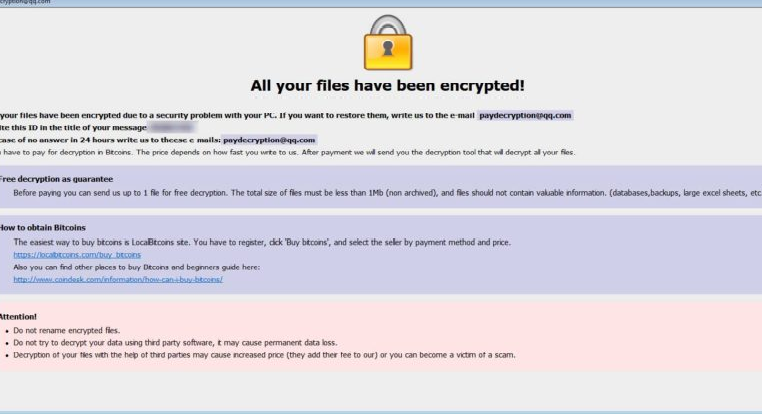
A new variant of the Dharma Ransomware was released this week that appends the .brrr extension to encrypted files. This variant was first discovered by Jakub Kroustek who tweeted a link to the sample on VirusTotal. Below I have outlined how this ransomware infects a computer, what happens when your files […]
Hacking
New XBash malware combines features from ransomware, cryptocurrency miners, botnets, and worms
Palo Alto Network researchers discovered a new malware, tracked as XBash, that combines features from ransomware, cryptocurrency miners, botnets, and worms Security researchers at Palo Alto Networks have discovered a new piece of malware, dubbed XBash piece that is targeting both Linux and Microsoft Windows servers. Xbash was developed using Python, […]
LuckyMouse signs malicious NDISProxy driver with certificate of Chinese IT company
What happened? Since March 2018 we have discovered several infections where a previously unknown Trojan was injected into the lsass.exe system process memory. These implants were injected by the digitally signed 32- and 64-bit network filtering driver NDISProxy. Interestingly, this driver is signed with a digital certificate that belongs to […]
Google Android team found high severity flaw in Honeywell Android-based handheld computers
Experts at the Google Android team have discovered high severity privilege escalation vulnerability in some of Honeywell Android-based handheld computers. Security experts from the Google Android team have discovered a high severity privilege escalation vulnerability in some of Honeywell Android-based handheld computers that could be exploited by an attacker to gain elevated privileges. According […]
MageCart Attackers Compromise Cloud Service Firm Feedify
Hundreds of e-commerce Sites Impacted by MageCart Compromise of Cloud Service Provider Payment card data from customers of hundreds of e-commerce websites may have been stolen after the MageCart threat actors managed to compromise customer engagement service Feedify. Feedify, which claims to have over 4,000 customers, provides customers with various […]
Wannamine Malware Still Penetrate the Unpatched SMB Computers using NSA’s EternalBlue Exploit
Cryptomining based Wannamine malware outbreak still actively attacking the windows users around the globe that using NSA exploit Eternalblue to penetrate the unpatched SMB enabled computers to gain high privileged access. Eternalblue Exploit leaked from NSA last year that made a huge impact around the world by exploiting the SMB flow and that […]
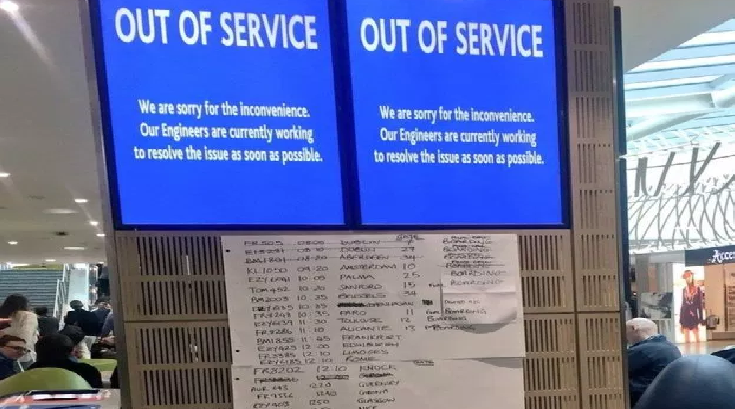
Ransomware Attack Hits Bristol Airport, Flight Display Screens Went Offline
Ransomware attack at the Bristol Airport in UK takes the flight display screens offline. The computers running the flight information display screen’s are affected. The incident likely took place on Friday morning which affected all the flight information display screen and the Airport staffs using Whiteboard to provide flight details. […]
Operator at kayo.moe found a 42M Record Credential Stuffing Data ready to use
Operator at kayo.moe found a 42M Record Credential Stuffing Data containing email addresses, plain text passwords, and partial credit card info. A huge archive containing email addresses, plain text passwords, and partial credit card data has been found on a free anonymous hosting service, Kayo.moe. The operator of the service shared the file with […]
Veeam Publicly Exposed 445 Million Customers Records Of its Marketing Database
Data Management Company’s misconfigured MongoDB server exposed its marketing database that contains around 445 million its customer records. Veeam, a company that develops backup, disaster recovery and intelligent data management software for virtual, physical and cloud-based infrastructures. Exposed data contains more than 200 gigabytes of customer records, mostly names, email addresses, and in […]
Chinese Cyber Espionage Group APT10 Delivers UPPERCUT Backdoor Via Malicious Word Documents
Chinese cyber espionage group APT10 know for targeting construction and engineering, aerospace, and telecom firms, and governments agencies in United States, Europe, and Japan. With the current campaign, the espionage group targeting Japanese entities through spear phishing emails with password-protected Microsoft Word documents that contain malicious VBA macros. Once the […]