La vulnérabilité permet à un attaquant ayant un accès limité à un système, via un terminal ou une session SSH, d’augmenter ses privilèges et d’obtenir un accès root. Les versions et distributions Linux et BSD qui utilisent le paquet X.Org Server – presque toutes le font – sont vulnérables à […]
Haythem Elmir
British Airways: additional 185,000 passengers may have been affected
The data breach suffered by the British Airways airline is worse than initially thought, according to IAG firm that wons the airline further 185,000 customers may have had impacted in the incident. The data breach suffered by the British Airways airline is worse than initially thought, according to IAG firm that owns the airline, further 185,000 […]
Systemd flaw could cause the crash or hijack of vulnerable Linux machines
Systemd is affected by a security vulnerability that can be exploited to crash a vulnerable Linux machine, and in the worst case to execute malicious code. An attacker can trigger the vulnerability using maliciously crafted DHCPv6 packets and modifying portions of memory of the vulnerable systems, potentially causing remote code […]
IBM rachète le leader du logiciel libre Red Hat pour 34 milliards de dollars
Afin de diversifier ses activités et de se faire une place dans le « cloud », la multinationale s’offre le numéro un de l’« open source » IBM a annoncé, dimanche 28 octobre, être parvenu à un accord pour racheter Red Hat, le premier fournisseur mondial de « logiciels libres », dans le cadre d’une transaction […]
Apple and Samsung fined millions for “planned obsolescence” of old smartphones
Italian Competition Authority AGCM fined Apple and Samsung a 5 million Euros and 10 million Euros for “planned obsolescence” of their mobile devices. After a long investigation conducted by the Italian Competition Authority AGCM, the agency has fined Apple and Samsung a 5 million Euros ($5.8 Million) and 10 million Euros ($11.5 Million) for “planned obsolescence” of […]
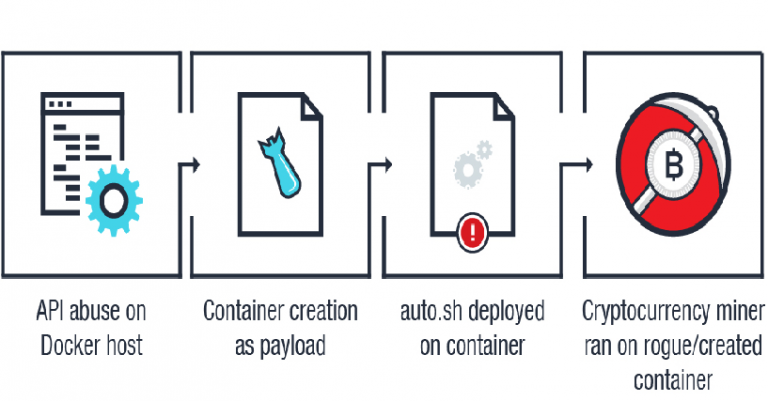
Crooks continue to abuse exposed Docker APIs for Cryptojacking
Cybercriminals continue to abuse unprotected Docker APIs to create new containers used for cryptojacking, Trend Micro warns. Crooks continue to abuse unprotected Docker APIs to create new containers used for cryptojacking. Earlier this year Sysdig and Aqua Security researchers started observing cyber attacks targeting Kubernets and Docker instances aimed at mining Monero cryptocurrency. A […]
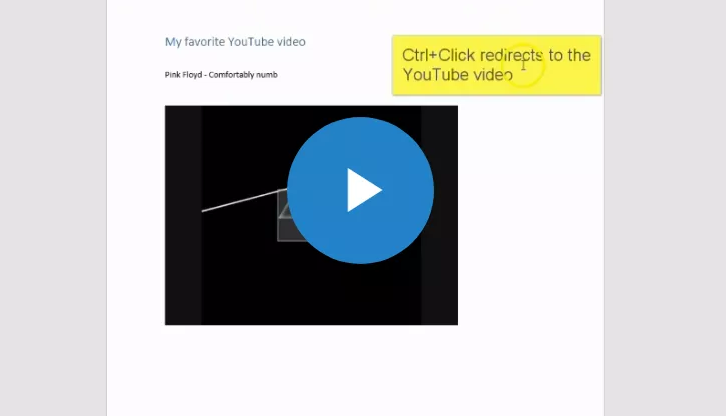
How to deliver malware using weaponized Microsoft Office docs embedding YouTube video
Researchers at Cymulate security firm devised a new stealthy technique to deliver malware leveraging videos embedded into weaponized Microsoft Office Documents. The technique could be used to execute JavaScript code when a user clicks on a weaponized YouTube video thumbnail embedded in a Weaponized Office document. Experts pointed out that […]
Cybercriminals stole 2.8 million dollars from Russians with the help of fake websites
Since the beginning of this year, hackers stolen 3.8 million dollars from Russians using web phishing. This is 6% more than last year. Experts believe that web phishing is the easiest and most effective way to steal money, as people are increasingly using Bank cards. Scammers create fake websites that […]
New FilesLocker Ransomware Offered as a Ransomware as a Service
A new ransomware called FilesLocker is being distributed as a Ransomware as a Service, or RaaS, that targets Chinese and English speaking victims. This ransomware was first spotted by MalwareHunterTeam who posted about it on Twitter. At the time, it looked like your standard small little C# ransomware with little or no distribution. It turns […]
Malware Distributors Adopt DKIM to Bypass Mail Filters
In July 2018, US-CERT raised an alert regarding the Emotet banking trojan, which is also being used to distribute a secondary malware known as “Trickbot”. This alert provided recommendations on how businesses can mitigate their exposure to the Trojan. Unfortunately, it looks like criminals are also reading the US-CERT’s warnings as […]