Two Syrians Accused of Buying Stolen Corporate Card Data to Mask Activities
The EU’s law enforcement intelligence agency Europol, which helped coordinate the raids, says they were launched after a private sector tip-off. Europol’s European Cybercrime Center subsequently helped police identify suspects, leading to the arrest of two individuals last week.
Europol says the investigation was conducted with support from the EU’s Border and Coast Guard Agency, known as Frontex. The crime group had been tracked by the Federal Police of Germany, known as the Bundespolizei. Last October, German police launched Operation Goldring, which led investigators to the crime group « composed of Syrian nationals, which was involved in fraudulently purchasing airline and train tickets, » Europol says.
German police conducted house searches in Aachen, Dortmund and Essen, while Swedish police conducted house searches in Nörrköping, Malmö and Helsingborg. Authorities say they collectively recovered $118,000 worth of cash, in euros and U.S. dollars, during the raids.
German police say the gang has been tied to 493 fraudulent bookings.
 Europol’s headquarters in The Hague, Netherlands (Photo: Europol) »In most cases, the tickets were one-way tickets from Beirut to European member states, » Europol says. « The tech-savvy smugglers avoided detection by making the bookings using compromised corporate credit cards and credentials purchased online from other criminals offering them for sale. »
Europol’s headquarters in The Hague, Netherlands (Photo: Europol) »In most cases, the tickets were one-way tickets from Beirut to European member states, » Europol says. « The tech-savvy smugglers avoided detection by making the bookings using compromised corporate credit cards and credentials purchased online from other criminals offering them for sale. »
Cybercrime-as-a-Service Offerings Proliferate
Stolen payment cards remain easy to procure and relatively inexpensive, security experts say (see Why Cybercrime Remains Impossible to Eradicate).
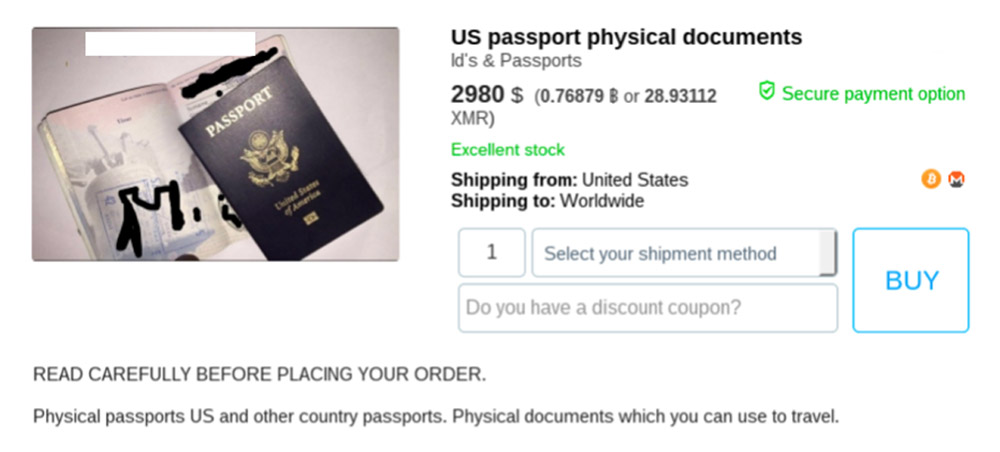
A review of cybercrime-as-a-service offerings published earlier this year by security firm Flashpoint said that payment card data, fake identity documents and access to bank accounts remain easily available and apparently popular products.
Many underground shops, for example, sell stolen payment card data – aka « dumps » – that are « often sourced directly from malware-infected or skimmed point-of-sale terminals, » according to Flashpoint. This information can be illicitly converted into cash using money mules and money-transfer services, or used to help mask fraudulent activity online.
Europol Lauds Private-Public Partnerships
Meanwhile, police continue attempts to crack down on criminals who buy and provide cybercrime-as-a-service offerings. Some of these law enforcement efforts are also sector-specific.
In the case of the Operation Goldring investigation, for example, last week’s arrests represent a continuation of Europol’s Global Airport Action Day, a public-private partnership that brings together the airline industry, payment card companies and law enforcement agencies to target airline fraud (see Airport Raids Target Fraudsters).
« As part of this operation, Europol and Frontex have jointly identified significant crossovers between payment card fraud and irregular migration and trafficking in human beings, leading to a number of arrests in recent years, » Europol says. « The fraudulent bookings were brought to the attention of law enforcement by the private sector, highlighting once again how instrumental public-private partnerships are in fighting this type of fraud. »
To read the original article
