Dans le cadre d’un partenariat stratégique, la Bourse des Valeurs mobilières de Tunis (BVMT) a confié à Ooredoo Tunisie le renforcement de ses interconnexions. Le nouveau dispositif garantira la liaison permanente de la Bourse en très haut débit avec ses différents partenaires, notamment le Conseil du Marché financier (CMF) et […]
India’s central bank issues cryptocurrency ban
The Reserve Bank of India (RBI) has banned regulated banks and its account holders from dealing in cryptocurrencies. The growing bubble around bitcoin and other virtual currencies has unnerved a number of central banks in recent months but the RBI’s blanket ban is the furthest measure so far taken by […]
FBI: IRANIAN FIRM STOLE DATA IN MASSIVE SPEAR PHISHING CAMPAIGN
The United States Department of Justice announced charges against nine Iranians accused of stealing private data from U.S. universities, private companies and U.S. government agencies. FBI Deputy Director David Bowdich said in a statement that the state-sponsored hackers worked for more than four years to steal expensive science and engineering-related research, company […]
Remote Execution Flaw Threatens Apps Built Using Spring Framework — Patch Now
Security researchers have discovered three vulnerabilities in the Spring Development Framework, one of which is a critical remote code execution flaw that could allow remote attackers to execute arbitrary code against applications built with it. Spring Framework is a popular, lightweight and an open source framework for developing Java-based enterprise […]
Meltdown et Spectre : Intel abandonne le développement des mises à jour de microcodes pour certains processeurs
Intel a publié une nouvelle version de sa feuille de route de mise à jour de microcodes depuis peu. Le fondeur annonce l’abandon du développement des mises à jour de microcodes pour certains processeurs ; la publication des correctifs pour le reste de sa flotte se poursuit néanmoins. En substance, plusieurs […]
QUICKLY PWNED, QUICKLY PATCHED: DETAILS OF THE MOZILLA PWN2OWN EXPLOIT
At our recent Pwn2Own 2018 competition, Richard Zhu (fluorescence) targeted and successfully exploited Mozilla Firefox with only one bug. After handing over the bug to Mozilla at the contest, they have promptly coordinated an update in less than 24 hours. The response was certainly impressive, but I wanted to take a closer […]
Five year old vulnerability used for Monero mining on Linux servers
A security vulnerability that is nearly 5 years old has now become the favorite tool of hackers as they are using it to infect Linux servers with crypto mining malware. The vulnerability that is being exploited in this cryptojacking campaign is classified as CVE-2013-2618. The miner is an altered XMRig tool, which is […]
Best Buy Hit by [24]7.ai Payment Card Breach
After Delta Air Lines and Sears Holdings, Best Buy has also come forward to warn customers that their payment card information may have been compromised as a result of a breach suffered by online services provider [24]7.ai. Similar to Delta and Sears, Best Buy contracted [24]7.ai for online chat/support services. The retailer […]
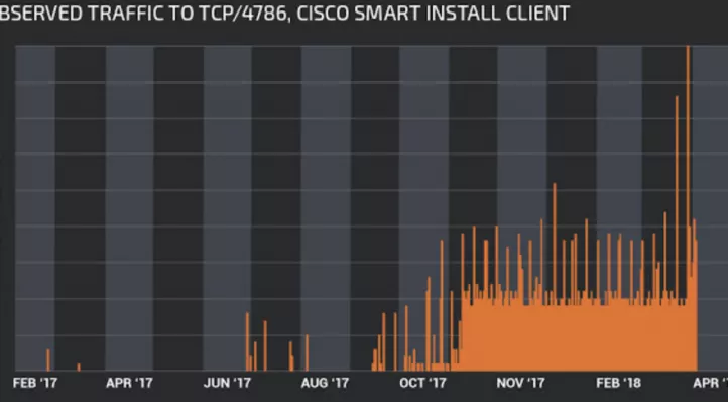
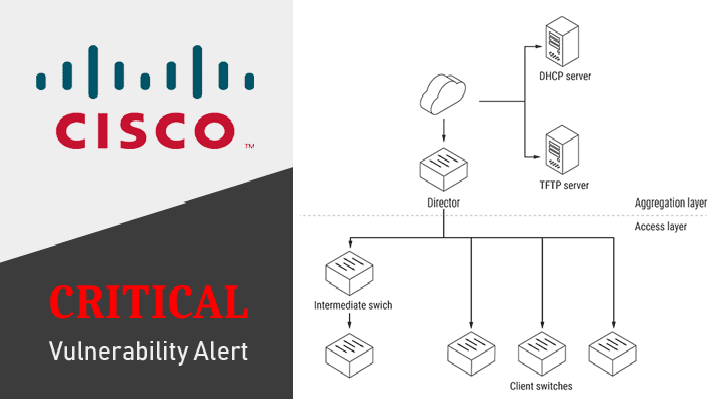
Cisco Smart Install Protocol misuse could expose critical infrastructure to attacks
Cisco PSIRT has published a new security advisory for abuse of the Smart Install protocol, the IT giant has identified hundreds of thousands of exposed devices online. Cisco is advising organizations that hackers could target its switches via the Smart Install protocol. The IT giant has identified hundreds of thousands of exposed […]
Critical flaw leaves thousands of Cisco Switches vulnerable to remote hacking
Security researchers at Embedi have disclosed a critical vulnerability in Cisco IOS Software and Cisco IOS XE Software that could allow an unauthenticated, remote attacker to execute arbitrary code, take full control over the vulnerable network equipment and intercept traffic. The stack-based buffer overflow vulnerability (CVE-2018-0171) resides due to improper […]






![Best Buy Hit by [24]7.ai Payment Card Breach](https://cyber.tn/wp-content/uploads/2018/04/best-buy.png)