Intel said Tuesday it was putting the kibosh on a popular Android and iOS app called Intel Remote Keyboard after researchers discovered that local attackers can inject keystrokes into a remote keyboard session when in use. The Intel Remote Keyboard product is an Android and iOS app that works in […]
New macOS Backdoor Linked to Cyber-espionage Group
A recently discovered macOS backdoor is believed to be a new version of malware previously associated with the OceanLotus cyber-espionage group, Trend Micro says. Also known as APT 32, APT-C-00, SeaLotus, and Cobalt Kitty, OceanLotus is believed to be operating out of Vietnam and has been targeting high-profile corporate and government […]
RAROG TROJAN ‘EASY ENTRY’ FOR NEW CRYPTOMINING CROOKS, REPORT WARNS
A malware family called Rarog is becoming an appealing and affordable tool for hackers to launch cryptocurrency mining attacks, researchers say. They say the Trojan is low priced, easily configurable and supports multiple cyrptocurrencies, making it an appealing option for hackers. Palo Alto Networks’ Unit 42 research team, which posted a blog on […]
Un satellite et un système de GPS 100% tunisiens
Dans le cadre de sa lutte contre le terrorisme, l’Armée Nationale compte miser sur les nouvelles technologies, selon le militaire Nizar Tabia, qui a affirmé, ce mercredi 4 avril 2018 sur Mosaïque FM, que l’Armée est en train de travailler sur un projet de géolocalisation basé sur la technologie GPS. […]
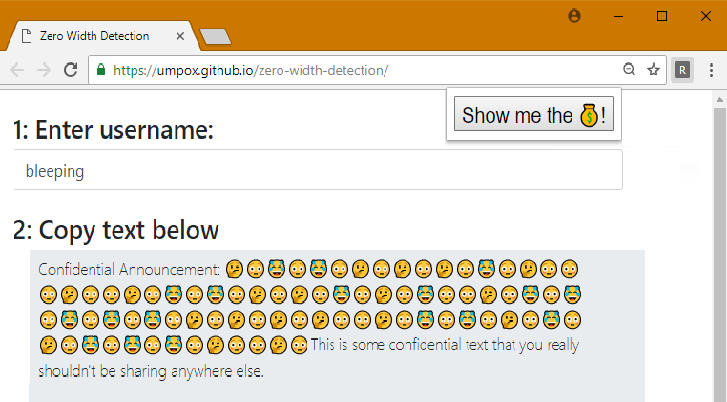
Google Chrome Extension Detects « Zero-Width Character » Fingerprinting Attacks
Google Chrome Extension Detects « Zero-Width Character » Fingerprinting Attacks Software developer Marco Chiappetta has built a Google Chrome extension that can detect attempts to fingerprint text using the « zero-width character » technique. The extension, named « Replace zero-width characters with emojis » is available on the official Google Chrome Web Store and on GitHub. Zero-width characters can […]
INSECURE SCADA SYSTEMS BLAMED IN RASH OF PIPELINE DATA NETWORK ATTACKS
After a cyberattack shut down numerous pipeline communication networks this week, experts are stressing the importance of securing third-party systems in supervisory control and data acquisition (SCADA) environments. Over the past two days, various major U.S. pipelines across the country reported data system blackouts after a third-party electronic communication system […]
Bank card fraud fears: Cloning can be carried out by STANDING CLOSE
Bank card fraud fears: Cloning can be carried out by STANDING CLOSE A WARNING has been issued over contactless bank cards with details being “skimmed” while the card is still in your pocket. And criminals can gain access to the equipment by purchasing it legally for just £20 online. One […]
Russian Hacker Who Allegedly Hacked LinkedIn and Dropbox Extradited to US
A Russian man accused of hacking LinkedIn, Dropbox, and Formspring in 2012 and possibly compromising personal details of over 100 million users, has pleaded not guilty in a U.S. federal court after being extradited from the Czech Republic. Yevgeniy Aleksandrovich Nikulin, 30, of Moscow was arrested in Prague on October 5, 2016, by Interpol […]
Project Kalamata – Apple will replace Intel processors in Macs with its custom designed chips
In the wake of the discovery of severe flaws in Intel chips, so-called Meltdown and Spectre vulnerabilities, Apple announced it plans to use custom-designed ARM chips in Mac computers starting as early as 2020. The move aims to replace the Intel processors running on its desktop and laptop systems like done for its own […]
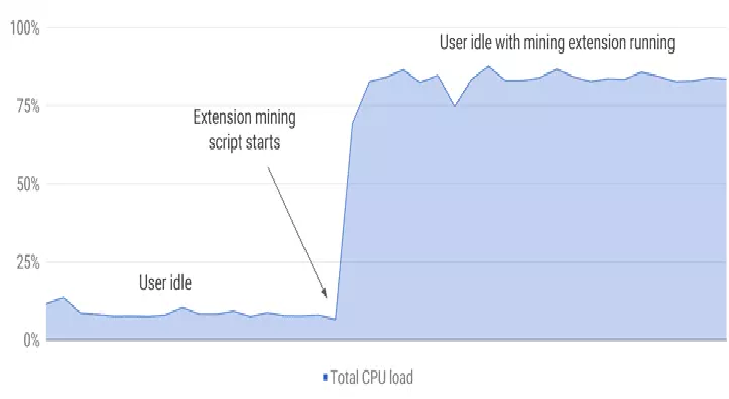
Google to banish cryptocurrency mining extensions from official Chrome Web Store
Google will ban cryptocurrency mining extensions from the official Chrome Web Store after finding many of them abusing users’ resources without consent. The number of malicious extensions is rapidly increased over the past few months, especially those related to mining activities. The company has introduced a new Web Store policy that bans […]