TrueMove H, the biggest 4G mobile operator in Thailand suffered a data leak, 46000 people’s data store on an AWS bucked were left on accessible online, including driving licenses and passports. Let’s speak about a new data breach, this time the victim is TrueMove H, the biggest 4G mobile operator in […]
Experts warn threat actors are scanning the web for Drupal installs vulnerable to Drupalgeddon2
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes,” experts started observing bad actors attempting to exploit the flaw. At the end of March, the Drupal Security Team confirmed that a “highly critical” vulnerability (dubbed Drupalgeddon2), tracked as CVE-2018-7600, was affecting Drupal 7 and 8 core and announced the […]
UK GCHQ director confirmed major cyberattack on Islamic State
GCHQ director Jeremy Fleming announced this week that the U.K. has launched a major cyberattack on the Islamic State (IS) terrorist organization. According to the spy chief, the GCHQ the attack was launched in collaboration with the U.K. Ministry of Defence and has distributed operations of the Islamic State. The UK intelligence […]
Microsoft engineer charged with money laundering linked to Reveton ransomware
The Microsoft network engineer Raymond Uadiale (41) is facing federal charges in Florida for the alleged involvement in Reveton Ransomware case. The man is suspected to have had a role in helping launder money obtained from victims of the Reventon ransomware. Uadiale currently works at Microsoft site in Seattle since 2014, […]
Attackers exfiltrated a casino’s high-roller list through a connected fish tank
Attackers exfiltrated a casino’s high-roller list through a connected fish tank Nicole Eagan, the CEO of cybersecurity company Darktrace, revealed that is company investigated that hack of an unnamed casino that was breached via a thermometer in a lobby fish tank. Internet of things devices are enlarging our attack surface, smart devices […]
Mozilla doing Google to block FTP sub resources
Mozilla will do a Goggle Chrome to block the loading of FTP sub-resources in HTTP-HTTPS pages introducing a new flag in Firefox 60 to disable the current FTP support in the browser as scheduled on June 26. But the move, even if executed, never would block direct FTP links on […]
Researchers Create Malware That Steals Data via Power Lines
A team of academics has successfully developed and tested malware that can exfiltrate data from air-gapped computers via power lines. The team —from the Ben-Gurion University of the Negev in Israel— named their data exfiltration technique PowerHammer. PowerHammer works by infecting an air-gapped computer with malware that intentionally alters CPU utilization […]
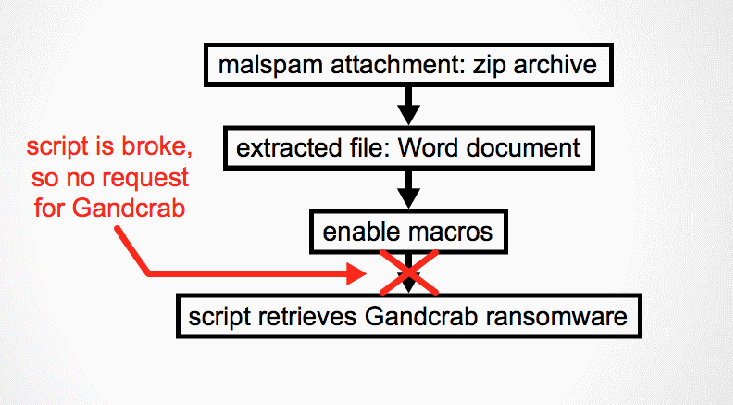
Compile Error Halts Some GandCrab Ransomware Infections
A script compile error has temporarily stopped the infection chain of a malspam campaign trying to infect users with the GandCrab ransomware. Not all GandCrab versions are affected, but only a GandCrab operation that tries to infect victims via malicious Word files users receive via spam emails. These Word documents contain […]
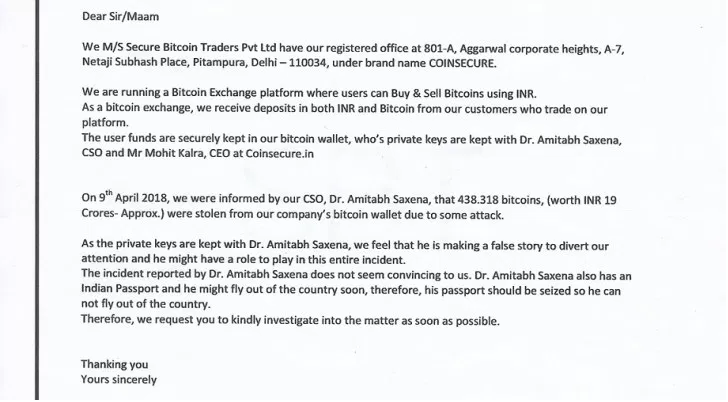
$3.3 Million stolen from main Coinsecure Bitcoin wallet
Cryptocurrency exchange Coinsecure, India’s second exchange, announced that it has suffered a severe issue, 438 bitcoin, $3,3 million worth of bitcoin Cryptocurrency exchange Coinsecure, India’s second exchange, announced that it has suffered a severe issue, 438 bitcoin, $3,3 million worth of bitcoin, have been transferred from the main wallet to an account that is […]
APT33 devised a code injection technique dubbed Early Bird to evade detection by anti-malware tools
The Iran-linked APT33 group continues to be very active, security researchers at Cyberbit have discovered an Early Bird code injection technique used by the group. The Early Bird method was used to inject the TurnedUp malware into the infected systems evading security solutions. The technique allows injecting a malicious code into a legitimate process, it […]