A team of academics has successfully developed and tested malware that can exfiltrate data from air-gapped computers via power lines. The team —from the Ben-Gurion University of the Negev in Israel— named their data exfiltration technique PowerHammer.
PowerHammer works by infecting an air-gapped computer with malware that intentionally alters CPU utilization levels to make the victim’s computer consume more or less electrical power.
By default, computers extract power from the local network in a uniform manner. A PowerHammer attack produces a variation of the amount of power a victim’s PC sucks from the local electrical network. This phenomena is known as a « conducted emission. »
By altering the high and low power consumption levels, PowerHammer malware can encode binary data from a victim’s computer into the power consumption pattern.
There are two types of PowerHammer attacks
To retrieve this data, an attacker must tap a victim’s electrical network so it can read the power consumption variation and decode the binary data hidden inside.
Based where the attacker places his tapping rig, two types of PowerHammer attacks exists, with two different exfiltration speeds.
The first is « line level power-hammering, » and this occurs when the attacker manages to tap the power cable between the air-gapped computer and the electrical socket. The exfiltration speed for a line level hammering is around 1,000 bits/second.
The second is « phase level power-hammering, » this version of the attack occurs when the intruder taps the power lines at the phase level, in a building’s electrical panel. This version of the PowerHammer attack is more stealthy but can recover data at only 10 bits/second, mainly due to greater amount of « noise » at the power line phase level.
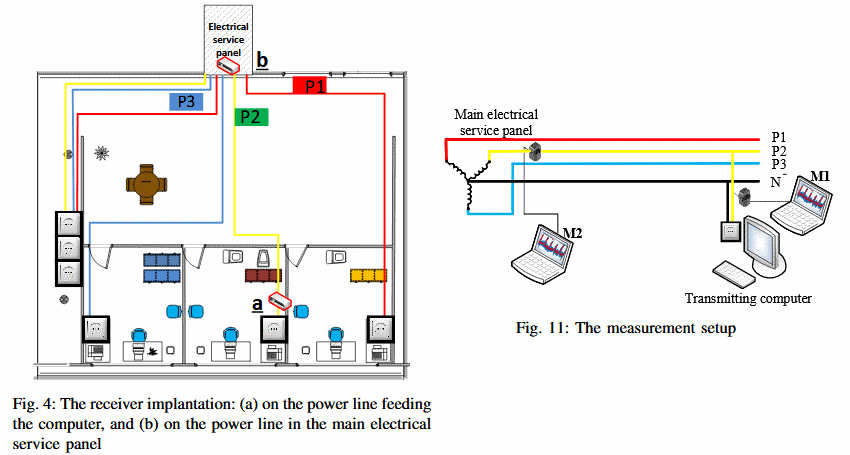
Attack uses off-the-shelf electrical equipment
The tapping device isn’t anything super-advanced, being a mundane split-core current transformer that can be attached to any electrical line.
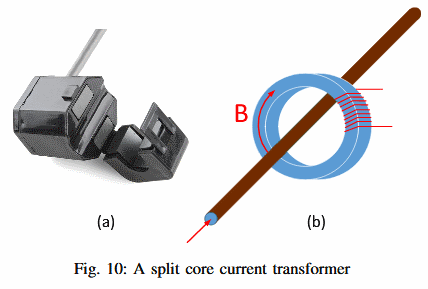
The tapping device (probe) is also capable of sending the recorded data to a nearby computer via WiFi, making data collection easier from afar, without the attacker having to physically connect to the tapping probe.
Attack works on desktops, servers, IoT devices
Experiments revealed the attack is successful for stealing data from air-gapped desktops, laptops, servers, and even IoT devices, but the speed exfiltration speed is slower for the latter. Another observation is that exfiltration speed gets better the more cores a CPU possesses.
Mitigations and more details for our technically inclined users are available in the research team’s paper, entitled « PowerHammer: Exfiltrating Data from Air-Gapped Computers through Power Lines. » It also must be said that this malware is only an experiment and if ever deployed in the wild, such a tool would only be found in the arsenal of intelligence agencies and not something that normal users would see every day.
To read the original article:https://www.bleepingcomputer.com/news/security/researchers-create-malware-that-steals-data-via-power-lines/