A script compile error has temporarily stopped the infection chain of a malspam campaign trying to infect users with the GandCrab ransomware.
Not all GandCrab versions are affected, but only a GandCrab operation that tries to infect victims via malicious Word files users receive via spam emails.
These Word documents contain malicious VBScript code hidden inside a Word macro. If users download and open these Word files, then allow the macro to execute, the VBScript downloads and installs the GandCrab ransomware.
Compile error spotted earlier this week
While investigating this malspam campaign, security researcher Brad Duncan has spotted a compile error that blocks the VBScript from executing, meaning users won’t get infected with GandCrab.
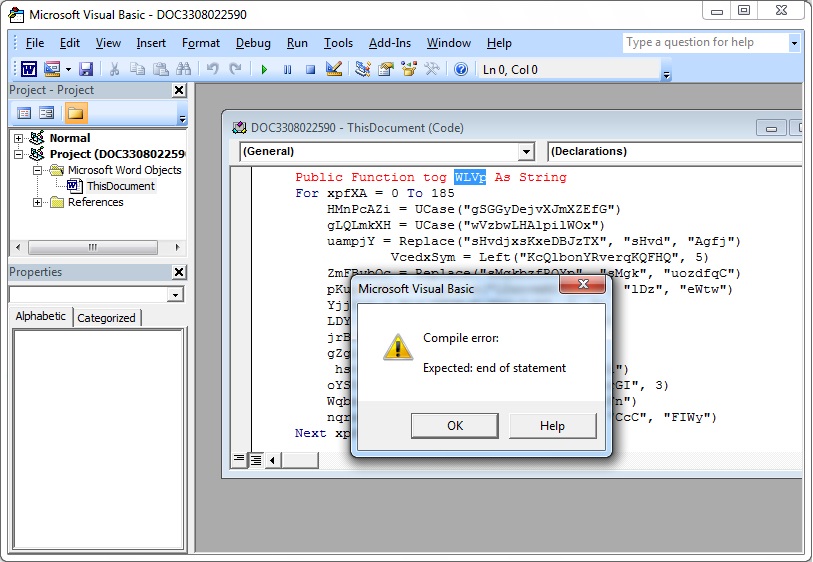
« Due to this compile error in the macro code, I can’t say how many potential victims might have been spared from an infection since 2018-04-10, » Duncan wrote on the SANS ISC forum yesterday.
But according to data Bleeping Computer obtained from the ID-Ransomware service, there was hardly a noticeable dent in GandCrab infection numbers this week or compared to last week.
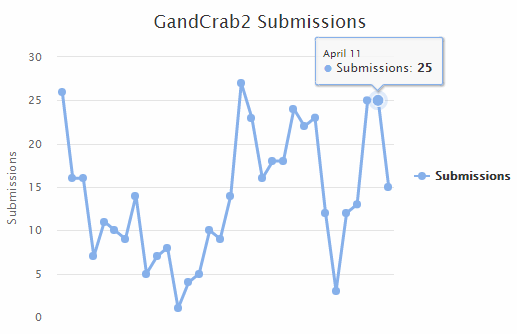
According to Duncan, this is because malspam campaigns aren’t efficient at infecting users to begin with.
« The risk of infection is normally quite low for a malspam campaign distributing commodity ransomware like GandCrab, » Duncan explains.
« In order to infect their computers, potential victims would have to bypass Protected View and ignore security warnings about activating macros on a Word document, » Duncan adds. « People can also easily implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections. »
Error will get fixed
« I’m sure the compile error in the [malspam] campaign will be resolved sooner or later, » Duncan said. « When that happens, the normal risk of infection will return to any improperly-managed Windows hosts hit by this malspam. »
The reason why Duncan might believe the error will get resolved quite quickly is because the GandCrab crew is usually on top of their operation. When Bitdefender released a decrypter for the first version of the GandCrab ransomware at the end of February, the GandCrab crew had version 2.0 out in less than a week.
To read the original article:
https://www.bleepingcomputer.com/news/security/compile-error-halts-some-gandcrab-ransomware-infections/
