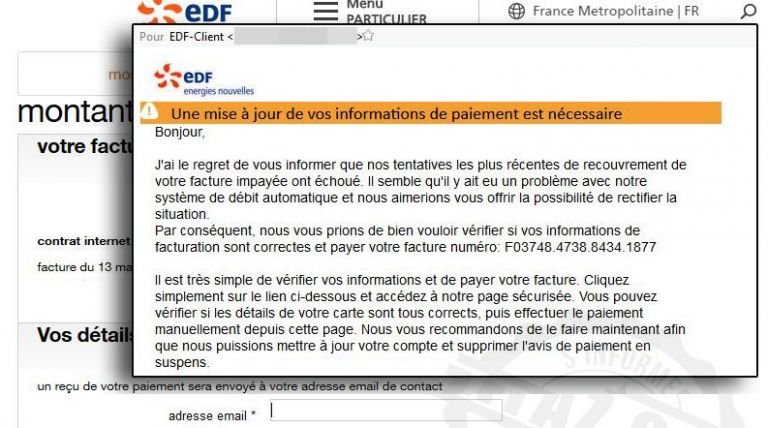
Fraude EDF : gare au courriel d’un pirate ! Fraude EDF – Des centaines de courriers électroniques aux couleurs d’EDF diffusés par un pirate. Mission de l’escroc, se faire passer pour l’opérateur d’énergie et mettre la main sur vos données bancaires. Nouvelle vague de phishing et d’une fraude EDF. Des hameçonnages […]
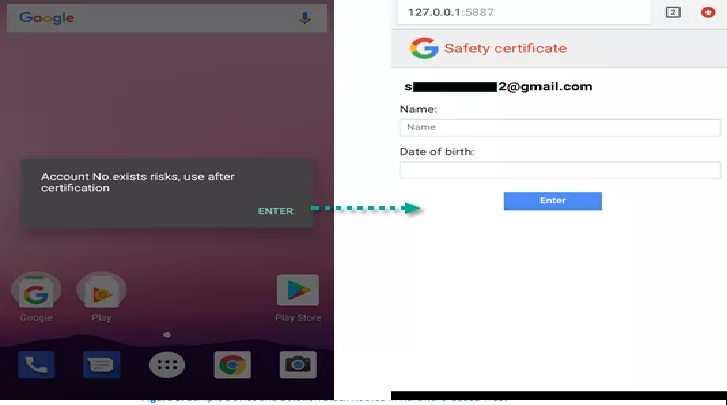
Roaming Mantis Malware Campaign Leverages Hacked Routers to Infect Android Users With Banking Trojan
According to experts at Kaspersky, the Roaming Mantis malware is designed for distribution through a simple, but very efficient trick based on DNS hijacking. According to experts at Kaspersky, the Roaming Mantis malware is designed for distribution through a simple, but very efficient trick based on DNS hijacking. Imagine a […]
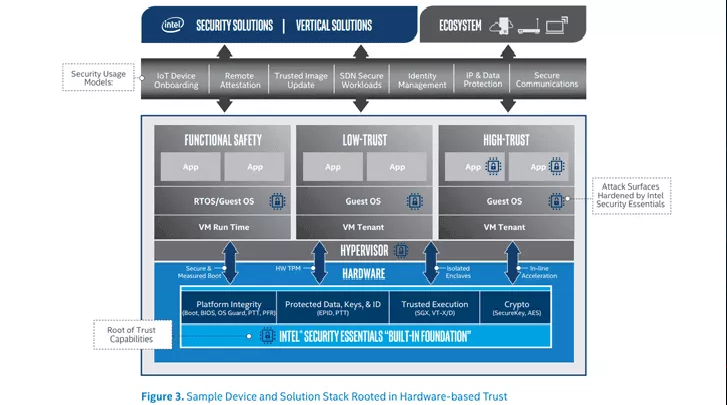
Intel announced the new Threat Detection Technology and Security Essentials
Intel announced a new Threat Detection Technology and a framework of critical root-of-trust hardware security capabilities in its chips. Intel continues to innovate its products, the tech giant announced two new technologies, the Threat Detection Technology (TDT) and Security Essentials. The Threat Detection Technology leverages the silicon-level telemetry and functionality to allow […]
US, UK warn Russians hackers are compromising networking devices worldwide
Russian state-sponsored hackers are targeting network infrastructure devices worldwide, the US Department of Homeland Security (DHS), Federal Bureau of Investigation (FBI), and the United Kingdom’s National Cyber Security Centre (NCSC) have warned on Monday. A joint technical alert published by the organizations says that the targets are “primarily government and […]
Bank web apps are the « most vulnerable » to getting hacked, new research says
Bad news if you’re one of the hundreds of millions of online banking users around the world. The chances are your bank’s website and web apps are horribly insecure. Researchers at security firm Positive Technologies, which has a commercial stake in securing web apps, tested 33 websites and services using its […]
Talos experts found many high severity flaws in Moxa EDR-810 industrial routers
Security experts at Cisco’s Talos group have discovered a total of 17 vulnerabilities in Moxa EDR-810 industrial routers manufactured by Moxa. The Moxa EDR-810 is an integrated industrial multiport router that implements firewall, NAT, VPN and managed Layer 2 switch capabilities. These devices are used in industrial environments to protect systems such […]
Gootkit banking Trojan continues to be delivered via fake invoices via Mailgun SMTP relay service and Microsoft one drive for business
Gootkit banking trojan is still being distributed via the Mailgun SMTP sending service, using Microsoft’s One drive business file hosting service to deliver the malicious macro enabled word docs that in turn download the gootkit banking trojan payload from another site. These use compromised mail accounts or websites to relay […]
New malware strikes panic among B’luru bank customers
The bankers in Bengaluru claimed to have discovered a new malware that helps the hackers siphon off money from a number of bank accounts forcing the southern city policemen to probe a number of complaints they received from the affected account holders. The policemen probing the cyber crime initially talk […]
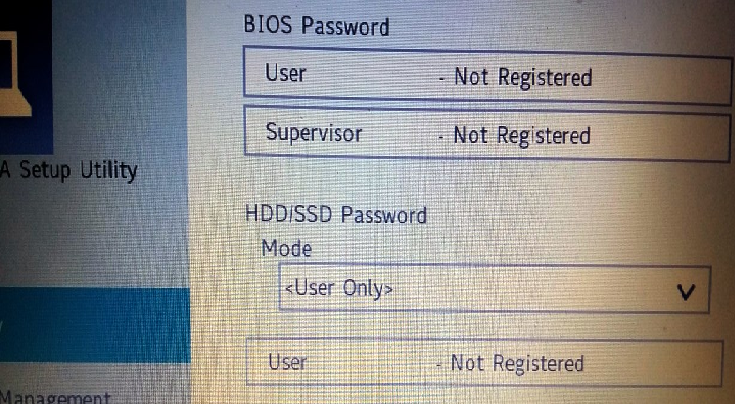
Intel SPI Flash Flaw Lets Attackers Alter or Delete BIOS/UEFI Firmware
Intel has addressed a vulnerability in the configuration of several CPU series that allow an attacker to alter the behavior of the chip’s SPI Flash memory —a mandatory component used during the boot-up process . According to Lenovo, who recently deployed the Intel fixes, « the configuration of the system firmware […]
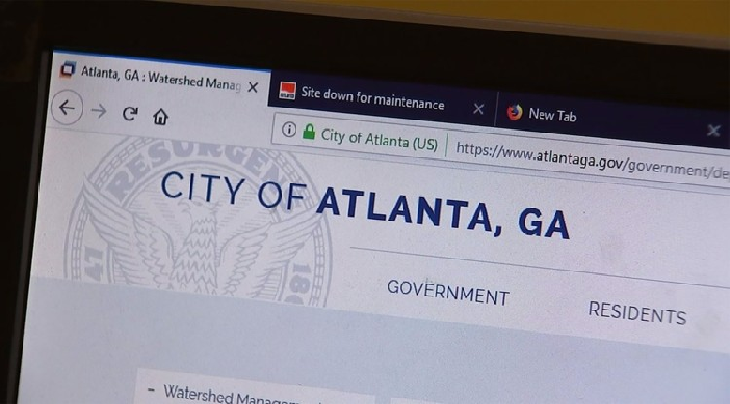
Cost of City of Atlanta’s cyber attack: $2.7 million — and rising
The City of Atlanta entered into emergency contracts worth $2.7 million to help restore the city’s computer network in the days following the March 22 ransomware cyber attack. But despite hiring a stable of security consultants and crisis communications experts, some departments remain hobbled by an attack that occurred after years […]