If you have ever copied or opened a Unix file in the Windows Notepad, you would have seen that the result is very ugly as all of the text appears as a mess on one line as Notepad does not recognize Linux End of Line (EOL) characters. This is all going […]
« Hide and Seek » Becomes First IoT Botnet Capable of Surviving Device Reboots
Security researchers have discovered the first IoT botnet malware strain that can survive device reboots and remain on infected devices after the initial compromise. This is a major game-changing moment in the realm of IoT and router malware. Until today, equipment owners could always remove IoT malware from their smart […]
SIERRA WIRELESS PATCHES CRITICAL VULNS IN RANGE OF WIRELESS ROUTERS
Sierra Wireless has patched two critical vulnerabilities for its range of wireless gateways that would leave the enterprise devices helpless to an array of remote threats, including the charms of the Reaper IoT botnet. The more critical of the two (with a 9.4 CVSSv3 Temp Score) is a privilege-escalation bug (CVE-2018-10251), […]
Hackers continue to hack Drupal installs to install backdoors and inject cryptocurrency malware
Recently security experts discovered two critical vulnerabilities in the Drupal CMS (CVE-2018-7600 and CVE-2018-7602), and cybercriminals promptly attempted to exploit them in the wild. The hackers started using the exploits for the above vulnerabilities to compromise drupal installs, mostly cryptocurrency mining. It has been estimated that potentially over one million Drupal websites are vulnerable […]
UPDATED – Critical RCE vulnerability found in over a million GPON Home Routers
Security researchers at VPNMentor conducted a comprehensive assessment on of a number of GPON home routers and discovered a Critical remote code vulnerability that could be exploited to gain full control over them. The researchers have found a way to bypass the authentication to access the GPON home routers (CVE-2018-10561). The experts chained this authentication […]
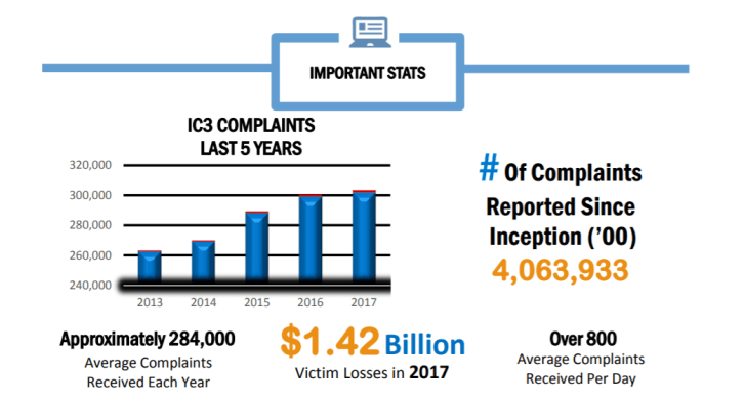
Reading the 2017 Internet Crime Complaint Center (IC3) report
The FBI’s Internal Crime Complaint Center (IC3) released the FBI 2017 Internet Crime Report, a document that outlines cybercrime trends over the past year. Here we are to analyze the annual FBI 2017 Internet Crime Report, one of the most interesting documents on the crime trends in the last 12 months. The […]
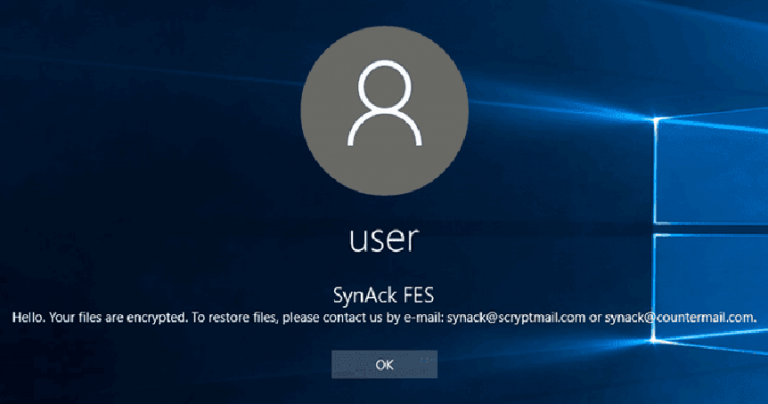
First-Ever Ransomware Found Using ‘Process Doppelgänging’ Attack to Evade Detection
Security researchers have spotted the first-ever ransomware exploiting Process Doppelgänging, a new fileless code injection technique that could help malware evade detection. The Process Doppelgänging attack takes advantage of a built-in Windows function, i.e., NTFS Transactions, and an outdated implementation of Windows process loader, and works on all modern versions of Microsoft Windows […]
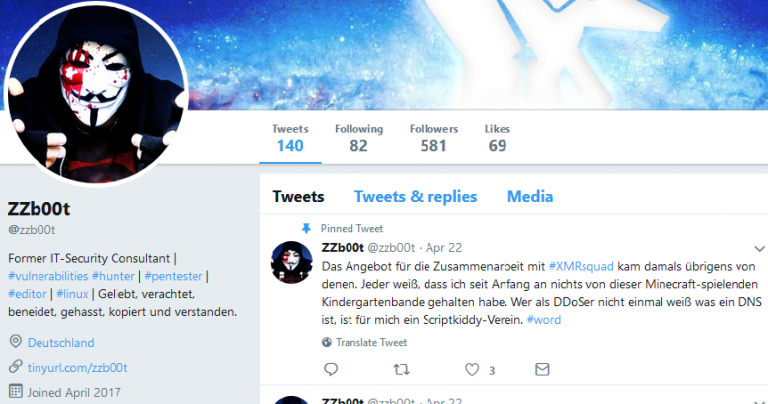
DDoSer Who Terrorized German and UK Firms Gets Off Without Jail Time
A German hacker who launched DDoS attacks and tried to extort ransom payments from German and UK firms was sentenced last month to one year and ten months of probation. The hacker, identified by authorities only as 24-year-old Maik D., but known online as ZZb00t, was fingered for attacking companies such […]
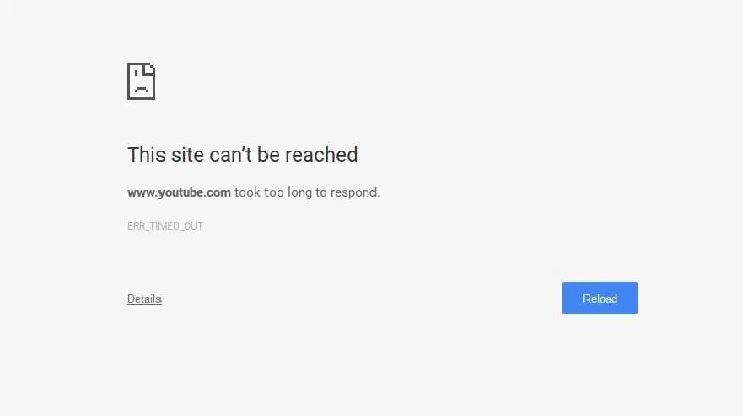
Chrome freezes PC running Windows OS after Windows 10 April update
Some Chrome users are reporting freezes and timeouts after the installation of the Windows 10 April Update, let’s see what has happened After the installation of Windows 10 April Update I observed continuous freezes while using the Chrome browser with one of my PCs, in some cases, I was not […]
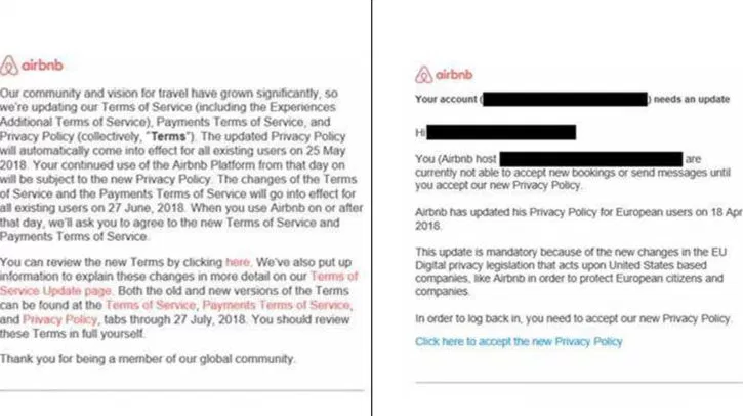
Phishing campaign aimed at Airbnb users leverages GDPR as a bait
Cybercriminals are targeting Airbnb users with phishing emails that urge the compliance with the new privacy regulation General Data Protection Regulation(GDPR). The upcoming General Data Protection Regulation (GDPR) privacy laws threaten with severe penalties to demand personal information from Airbnb users. The interest on the subject is very high among professionals and companies operating in […]