Security researchers have spotted the first-ever ransomware exploiting Process Doppelgänging, a new fileless code injection technique that could help malware evade detection.
The Process Doppelgänging attack takes advantage of a built-in Windows function, i.e., NTFS Transactions, and an outdated implementation of Windows process loader, and works on all modern versions of Microsoft Windows OS, including Windows 10.
Process Doppelgänging attack works by using NTFS transactions to launch a malicious process by replacing the memory of a legitimate process, tricking process monitoring tools and antivirus into believing that the legitimate process is running.
If you want to know more about how Process Doppelgänging attack works in detail, you should read this article I published late last year.
Shortly after the Process Doppelgänging attack details went public, several threat actors were found abusing it in an attempt to bypass modern security solutions.
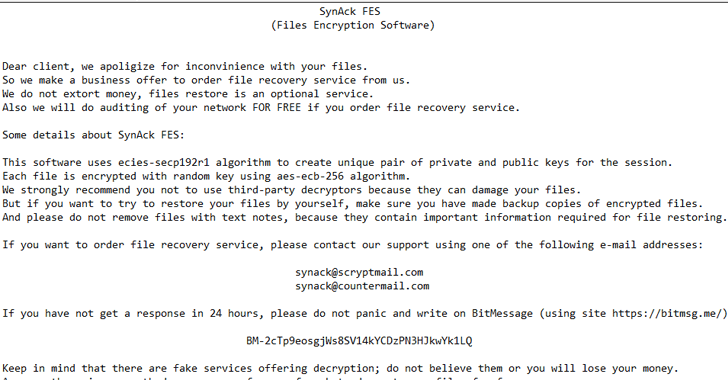
Security researchers at Kaspersky Lab have now found the first ransomware, a new variant of SynAck, employing this technique to evade its malicious actions and targeting users in the United States, Kuwait, Germany, and Iran.
Initially discovered in September 2017, the SynAck ransomware uses complex obfuscation techniques to prevent reverse engineering, but researchers managed to unpack it and shared their analysis in a blog post.
An interesting thing about SynAck is that this ransomware does not infect people from specific countries, including Russia, Belarus, Ukraine, Georgia, Tajikistan, Kazakhstan, and Uzbekistan.
To identify the country of a specific user, the SynAck ransomware matches keyboard layouts installed on the user’s PC against a hardcoded list stored in the malware. If a match is found, the ransomware sleeps for 30 seconds and then calls ExitProcess to prevent encryption of files.
SynAck ransomware also prevents automatic sandbox analysis by checking the directory from where it executes. If it found an attempt to launch the malicious executable from an ‘incorrect’ directory, SynAck won’t proceed further and will instead terminate itself.
Once infected, just like any other ransomware, SynAck encrypts the content of each infected file with the AES-256-ECB algorithm and provides victims a decryption key until they contact the attackers and fulfill their demands.
SynAck is also capable of displaying a ransomware note to the Windows login screen by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. The ransomware even clears the event logs stored by the system to avoid forensic analysis of an infected machine.
Although the researchers did not say how SynAck lands on the PC, most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.
Therefore, you should always exercise caution when opening uninvited documents sent over an email and clicking on links inside those documents unless verifying the source in an attempt to safeguard against such ransomware infection.
Although, in this case, only a few security and antivirus software can defend or alert you against the threat, it is always a good practice to have an effective antivirus security suite on your system and keep it up-to-date.
Last but not the least: to have a tight grip on your valuable data, always have a backup routine in place that makes copies of all your important files to an external storage device that isn’t always connected to your PC.
To read the original article:
https://thehackernews.com/2018/05/synack-process-doppelganging.html