A la fin du support de Windows 7 en janvier 2020, Microsoft proposera une prolongation jusqu’en 2023 à ses clients qui le souhaitent, à condition de payer pour les correctifs de sécurité. L’horloge tourne et la fin de support de Windows 7 programmée pour le 14 janvier 2020 se rapproche. […]
Lancement des guichets automatiques 30 Crypto en Inde – Unocoin dévoile une solution à l’interdiction bancaire de RBI
Unocoin, un important centre de cryptographie en Inde, a officiellement annoncé le lancement de ses guichets automatiques cryptographiques. Le PDG Sathvik Vishwanath a déclaré à news.Bitcoin.com que, Initialement, la société prévoit de déployer des machines 30 dans trois villes indiennes. «Ces guichets automatiques aident les gens à encaisser et à encaisser […]
Natural Disaster Related Phishing Scam Abusing Microsoft Azure to Steal login Credentials & Credit Card Numbers
Cybercriminals are distributing new phishing scam related to natural disasters that abusing Microsoft Azure Blog Hosting and also attempt to steal the login credentials. Victims abused by forcing them to involved with fake donations or steal funds directly via fraudulent donations in order to steal the credit card numbers. This Phishing campaign Lures Florida Hurricane […]
WizCase Report: Vulnerabilities found in WD My Book, NetGear Stora, SeaGate Home, Medion LifeCloud NAS
Security researchers from WizCase have discovered several vulnerabilities in WD My Book, NetGear Stora, SeaGate Home, Medion LifeCloud NAS. NAS devices have become the storage device of choice for many small and medium businesses (SMB). They are inexpensive, easy to operate, and you can add additional storage if you’re running low on […]
DarkPulsar and other NSA hacking tools used in hacking operations in the wild
Attackers are targeting high-value servers using a three of hacking tools from NSA arsenal, including DarkPulsar, that were leaked by the Shadow Brokers hacker group. The hackers used the powerful cyber weapons to compromise systems used in aerospace, nuclear energy, R&D, and other industries. According to experts from Kaspersky Lab, threat actors leverage NSA tools DarkPulsar, DanderSpritz and Fuzzbunch to infect Windows […]
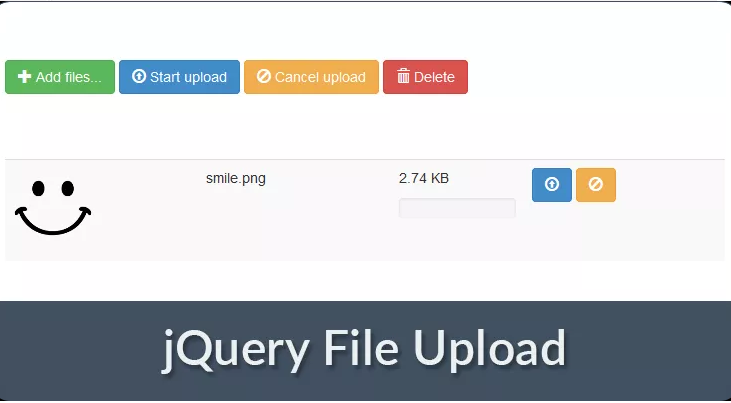
Thousands of applications affected by a zero-day issue in jQuery File Upload plugin
A security researcher discovered a zero-day vulnerability, tracked as CVE-2018-9206, that affects older versions of the jQuery File Upload plugin since 2010. Attackers can exploit the vulnerability to carry out several malicious activities, including defacement, exfiltration, and malware infection. The flaw was reported by the Akamai researcher Larry Cashdollar, he explained that many […]
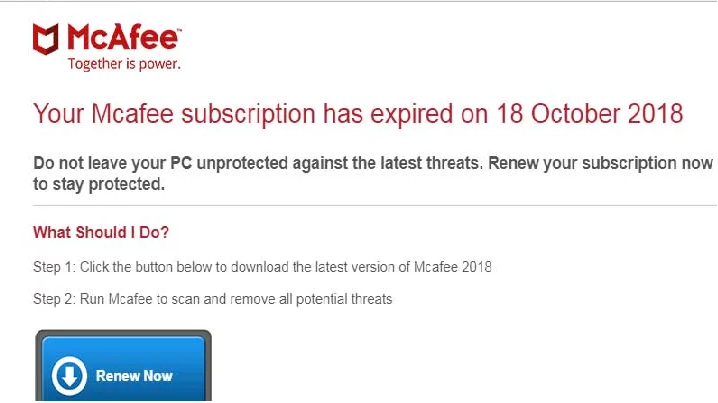
McAfee Tech Support Scam Harvesting Credit Card Information
A new tech support scam pretending to be from McAfee was discovered last week that is harvesting credit card details and personal information of its victims. Last week I was tipped off about a new browser-based tech support scam that stated « Your Mcafee subscription has expired on 18 October 2018 ». […]
IBM and banks back data project to fight human trafficking
Western Union, Barclays and Lloyds Banking Group are backing a new project that uses IBM’s Watson technology to tap into financial data to help track and combat human trafficking. Despite an increased awareness of human trafficking, efforts to manually track and counter the issue through legislation, preventative measures and enforcement, […]
Apple privacy portal lets you see everything it knows about you
A month after its most recent iPhone and Mac launches, Apple has refreshed its privacy pages. There isn’t much that’s changed: those pages still espouse Apple’s long-held commitment to privacy being a “fundamental human right” and that your information is, for the most part, kept on your iPhones, iPads and Macs. […]
Mozilla Brings Encrypted SNI to Firefox Nightly
Mozilla says Firefox Nightly now supports encrypting the Transport Layer Security (TLS) Server Name Indication (SNI) extension, several weeks after Cloudflare announced it turned on Encrypted SNI (ESNI) across all of its network. Introduced in 2003 to address the issue of accessing encrypted websites hosted at the same IP, the SNI extension […]