A new tech support scam pretending to be from McAfee was discovered last week that is harvesting credit card details and personal information of its victims.
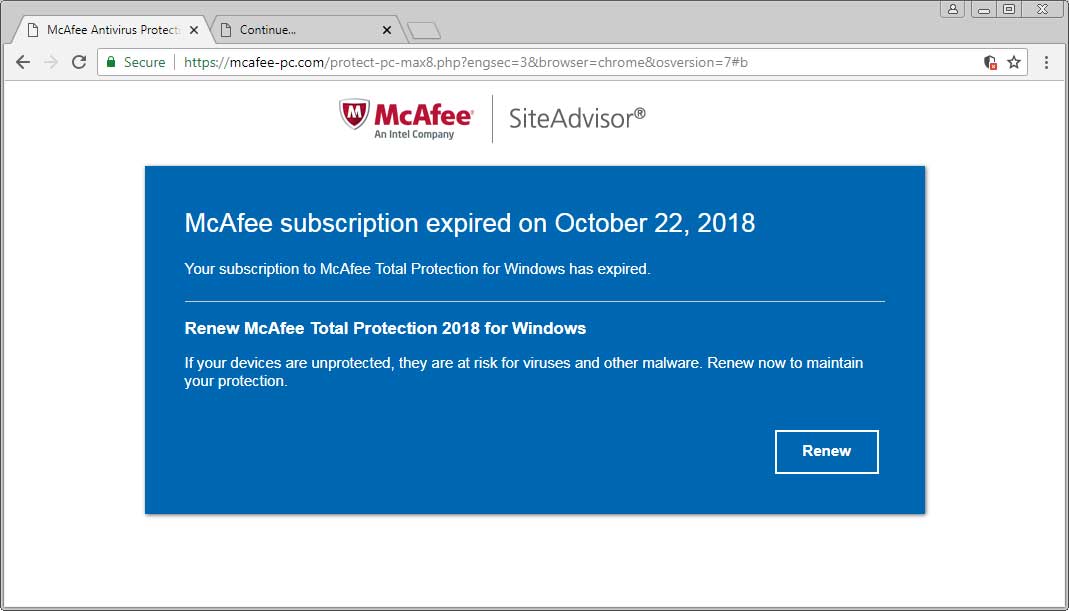
Last week I was tipped off about a new browser-based tech support scam that stated « Your Mcafee subscription has expired on 18 October 2018 ». This page then prompted me to renew as shown below.
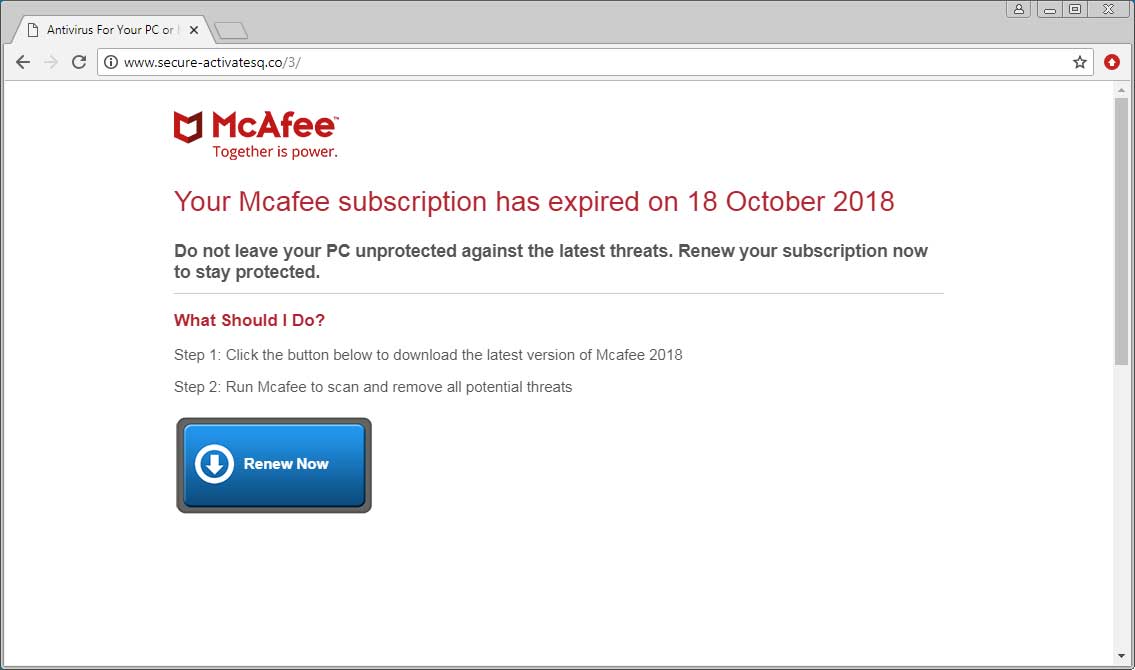
These McAfee scams are nothing new, but in the past they simply redirected you to McAfee’s site using an affiliate link. If you then purchased something at McAfee’s site, the scammers would generate a commission.
This variant of the scam, though, does things a bit differently. When users click on the « Renew Now » button, a small form will open up that asks for your credit card information. It is then followed by another form asking for your personal information.
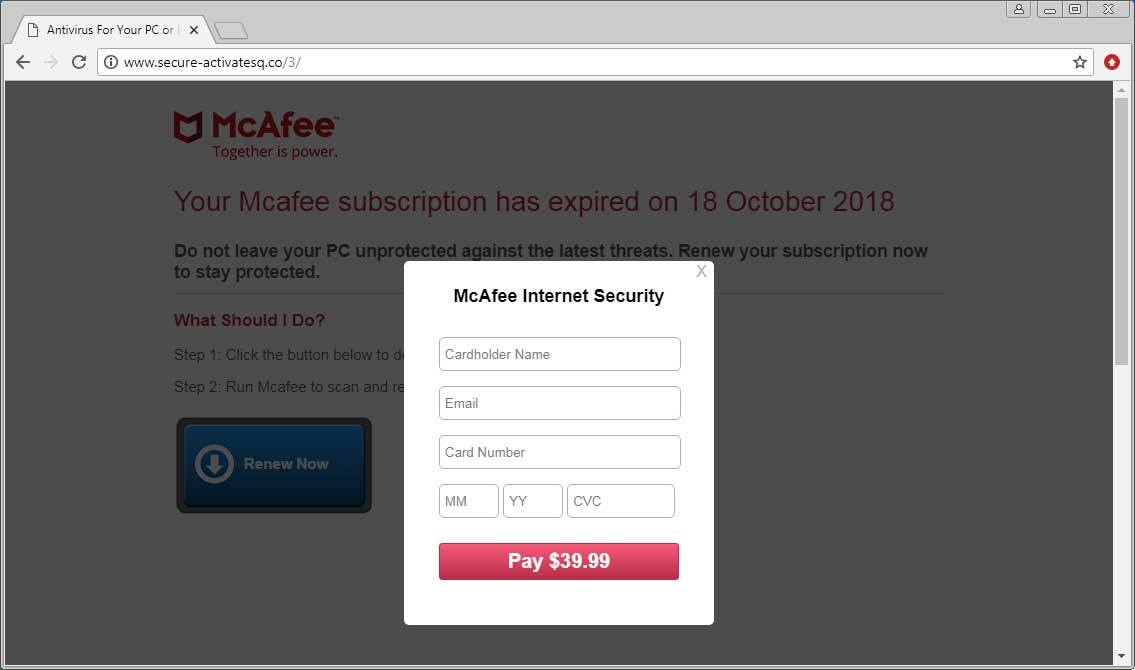
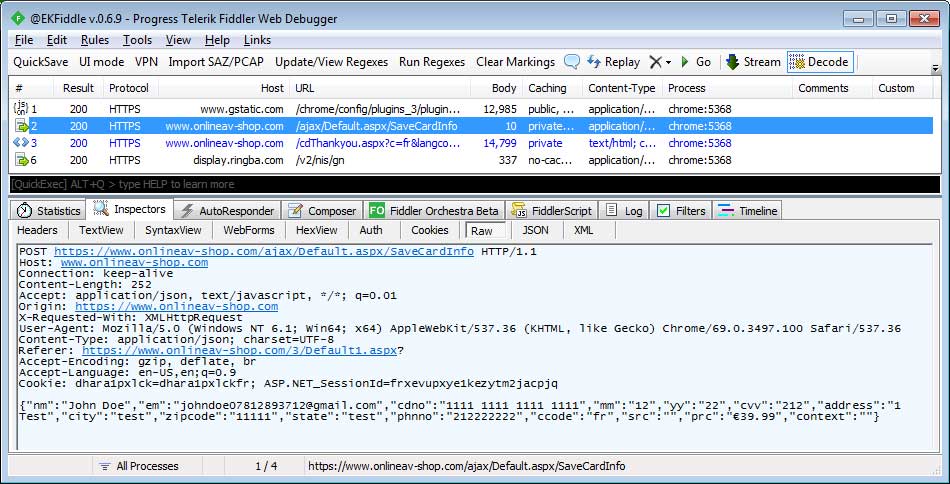
The information collected by this scam consists of the visitor’s name, email, card number, expiration date, CVC (Card Verification Code), address, city, state, zip, and phone number. When you are done entering your info and submit it, the page will connect to https://www.onlineav-shop.com/ajax/Default.aspx/SaveCardInfo where the information is saved.
You can see an example of this in the Fiddler traffic below.
When finished, the page will then redirect you to a thank you page that contains a rotating number, which you a told to call for help in installing your purchased software.
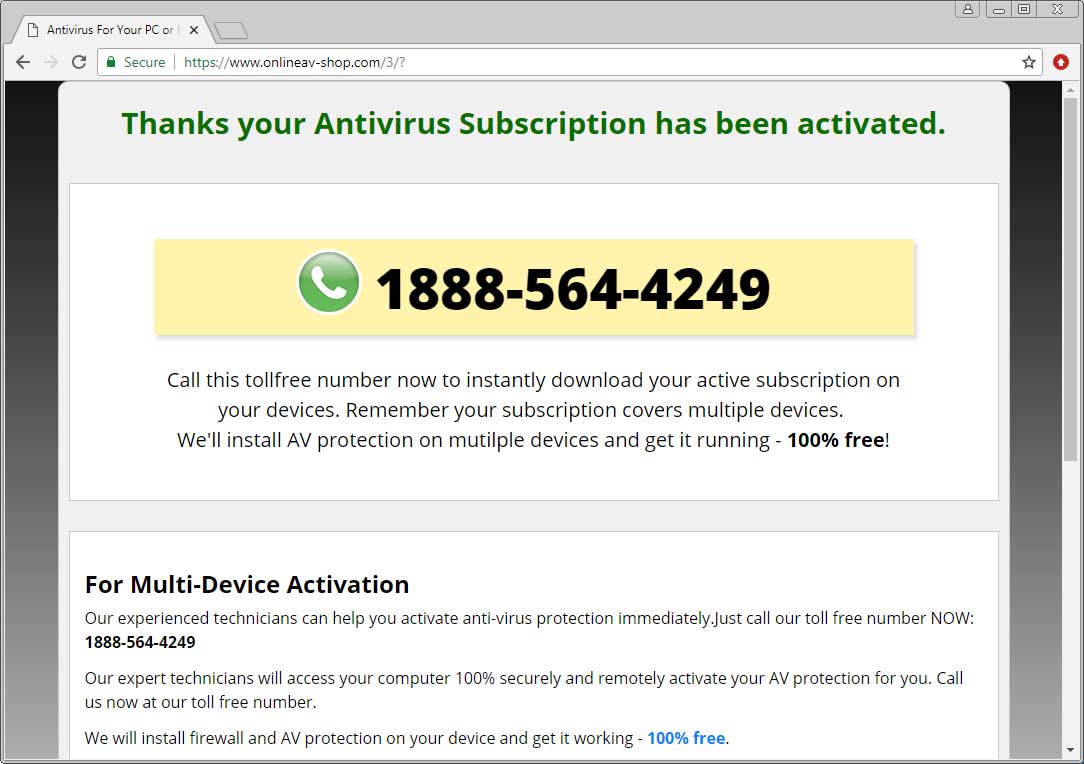
When calling this number, you will be connected to a company calling themselves « Premium Technical Support » that states they are partnered with or are McAfee depending on the agent you speak to.
They then request that they remotely connect to your computer in order to assist in install your software. Once connected, though, they state that the credit card information did not go through and that you need to purchase the software through McAfee’s site. They would then open a browser and connect to what appeared to be an affiliate URL.
I called this number numerous times and each time was told that there was a server error and that the submitted credit card information was not saved and that we would have to purchase the software using McAfee’s site.
Essentially, these scammers are not only earning commissions on affiliate sales, but also stealing your credit card and personal information. This information can then be used to charge other purchases or perform identity theft using your credentials.
If you were affected by a scam like this, it is strongly advised that contact your credit card company and cancel any unknown charges. It also suggested that you monitor your credit report for any unusual activity.
Scam site also pushes adware
According to Thomas Roccia, a security researcher at McAfee Labs, the associated scam site, onlineav-shop.com, is also known to host and distribute unwanted software and adware.
When examining some of the malware hashes provided by Roccia, I was able to identify the samples as being the WizzCaster adware. This adware will create random named executables on the infected PC and configure them to automatically start on login.
When started, the adware will open adverting redirects that promote adult sites, fake blogs, unwanted chrome extensions, and adware downloads. Coincidentally, the first advertisement shown by this adware was one for McAfee, but was the one that just redirects you to their site via an affiliate link.
The WizzLabs adware is detected by most antivirus programs, so if your browser it routinely opening the browser and showing advertisements or scams like the one above, you should perform a scan with a security program/
To read the original article: