Coldroot, a remote access trojan (RAT), is still undetectable by most antivirus engines, despite being uploaded and freely available on GitHub for almost two years.
The RAT appears to have been created as a joke, « to Play with Mac users, » and « give Mac it’s rights in this [the RAT] field, » but has since expanded to work all three major desktop operating systems — Linux, macOS, and Windows— according to a screenshot of its builder extracted from a promotional YouTube video.
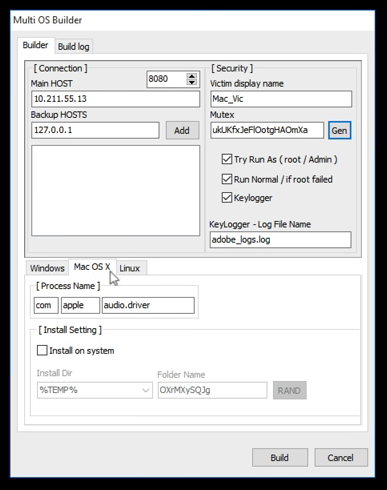
But despite being open-sourced in 2016, the RAT remained in anonymity, never being at the center of major cybercrime operations. Unfortunately, things appear to have changed in the meantime, and the RAT has now entered active distribution.
Coldroot RAT found in fake Apple audio driver package
Patrick Wardle, a Mac expert with Digita Security, has recently stumbled on a new version of the Coldroot RAT, which he broke down in a technical teardown here.
Wardle says this new version of the Coldroot RAT that he discovered in a faux Apple audio driver is different from the old version posted on GitHub in 2016.
But artifacts he found by analyzing the fake Apple audio driver matched the modus operandi and technical details included in the old Coldroot RAT GitHub code, suggesting the two were very likely connected, if not the same.
In the end, Wardle concluded that he stumbled upon the same Pascal-based Coldroot RAT, but over a new and improved version, with more features when compared to the original version from 2016.
According to the researcher, this new Coldroot RAT can spawn new remote desktop sessions, take screen captures and assemble them into a live stream of the victim’s desktop, can start and kill processes on the target’s system, and can search, download, upload, and execute files. All stolen data is sent to a remote web panel, similar to how most RATs work these days.
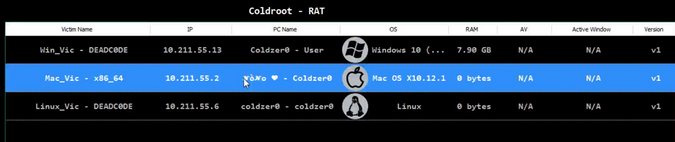
It is unclear if this new version has been improved by the same author, or by someone else who grabbed the code off GitHub. The new Coldroot RAT version still includes the contact details of its initial author —a hacker known as Coldzer0— but those could very well be false flags left behind to throw off security researchers looking into the malware.
To read the original article:https://www.bleepingcomputer.com/news/security/coldroot-rat-still-undetectable-despite-being-uploaded-on-github-two-years-ago/
