Some models of Huawei routers are affected by a flaw that could be exploited by attackers to determine whether the devices have default credentials or not.
Ankit Anubhav, a principal researcher at NewSky Security, discovered a vulnerability in some models of Huawei routers that could be exploited by attackers to determine whether the devices have default credentials or not, without connecting to them
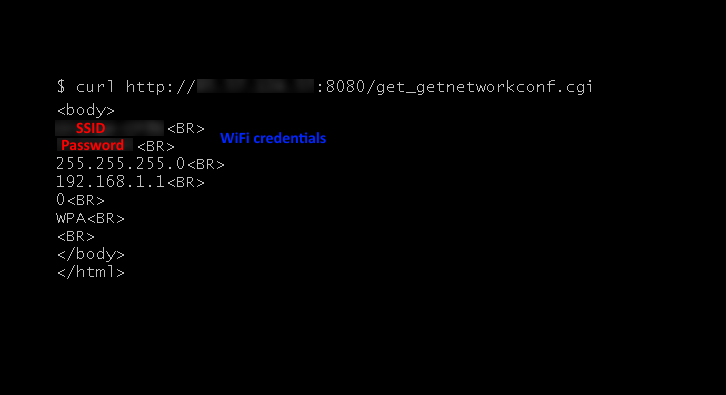
The flaw, tracked as CVE-2018-7900, resides in the router administration panel and allows credentials information to leak. An attacker could use IoT search engines such as ZoomEye or Shodan to scan the internet for devices having default passwords.
“CVE-2018–7900 makes the process of attacking a router even more simplified. Rather than doing a spray and pray technique (attack any device whether it has default credentials or not), an attacker can easily find a way to tell whether the router has default credentials without the need to connect to the device, since the router panel leaks this information.” reads the blog post published by the expert.
“Hence the attacker can craft a ZoomEye / Shodan dork to implicitly get a list of the devices having default password. “
The expert pointed out that analyzing the HTML source code of login page it is possible to observe that a few variables are declared and one of them contains a specific value. By analyzing this value it is possible to determine if the device has the defailt password.
This information could be used by attackers to query IoT search engines and retrieve a list of devices and associated login.

“How Easy CVE-2018-7900 Makes It Easy to Hack These Devices” continues the expert
- “The attacker does not need to scan the internet for finding the devices.
- The attacker does not need to attempt a failed login anymore, or encounter a generic honeypot which doesn’t have this flag.
- The attacker can simply go to ZoomEye, find a list of devices, login, and do what they want with minimal hacking skills. As easy as that.”
Huawei already fixed the vulnerability, but is working with carrier operators for complete resolution.
NewSky will not disclose details of the flaw to avoid its massive exploitation.
Below the timeline of the vulnerability:
- Sep 26, 18: Issue discovered and disclosed privately to Huawei.
- Sep 26, 18: Huawei confirms that they got the mail and starts looking into the issue.
- Oct 1, 18: Huawei completes analysis and mentions it is consulting with their customers on how to resolve it.
- Nov 6, 18: Huawei has provided a fix but is working with carrier operators for complete resolution.
- Dec 5, 18: Huawei has finished communication with operators/customers and is ready for a responsible disclosure.
- Dec 19, 18: Issue is disclosed publicly.
Source: https://securityaffairs.co/wordpress/79115/hacking/huawei-router-flaw.html