Two vulnerabilities affecting over one million routers, and disclosed earlier this week, are now under attack by botnet herders, who are trying to gather the vulnerable devices under their control. Attacks started yesterday, Thursday, May 3, according to Netlab, the network security division of Chinese cyber-security vendor Qihoo 360. […]
Année : 2018
Microsoft addressed critical flaw in Windows Host Compute Service Shim library
Microsoft released an out of band update to address a critical remote code execution vulnerability in the Windows Host Compute Service Shim library (hcsshim). Microsoft announced that it has issued a security update to address a critical remote code execution vulnerability in the Windows Host Compute Service Shim library (hcsshim). […]
CVE-2018-2879 – Vulnerability in Oracle Access Manager can let attackers impersonate any user account
Security researchers have discovered a security vulnerability in Oracle Access Manager that can be exploited by a remote attacker to bypass the authentication and take over the account of any user. Security researcher Wolfgang Ettlinger from SEC Consult Vulnerability Lab has discovered a security vulnerability in Oracle Access Manager that can be […]
La plus grande banque d’Australie reconnait la perte des données de 20 millions de clients
La plus grande banque d’Australie, la Commonwealth Bank, a admis jeudi avoir perdu les données financières d’environ 20 millions de clients tout en assurant qu’il n’y avait pas matière à s’inquiéter. Le premier prêteur d’Australie et sa première entreprise par la capitalisation boursière a reconnu ne pas être en mesure […]
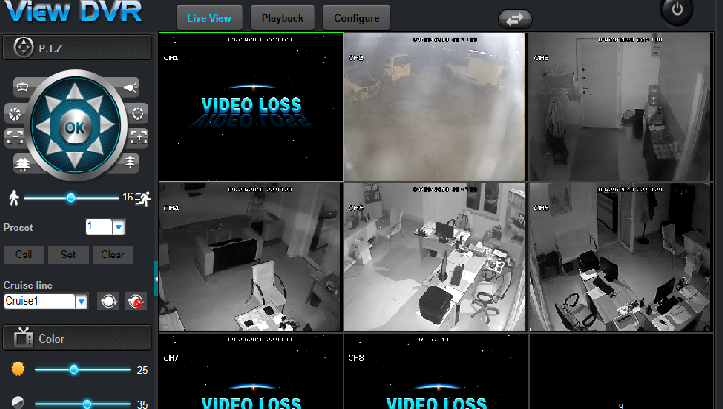
New Hacking Tool Lets Users Access a Bunch of DVRs and Their Video Feeds
An Argentinian security researcher named Ezequiel Fernandez has published a powerful new tool yesterday that can easily extract plaintext credentials for various DVR brands and grant attackers access to those systems, and inherently the video feeds they’re supposed to record. The tool, named getDVR_Credentials, is a proof-of-concept for CVE-2018-9995, a vulnerability discovered […]
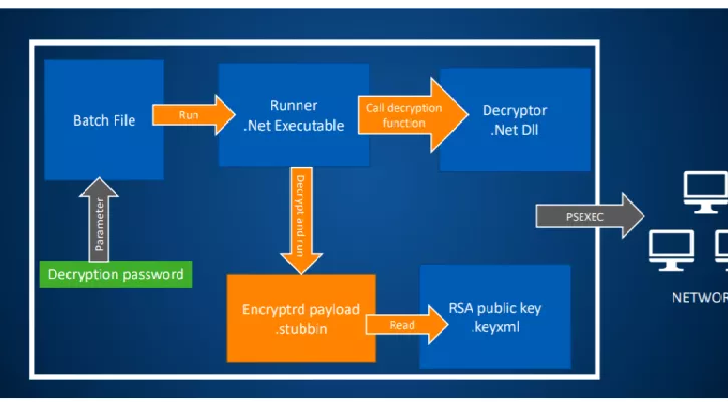
SamSam operators switch tactic and are more focused on targeted organizations
SamSam ransomware made the headlines again, crooks now spreading thousands of copies of the ransomware at once into individual targeted organizations. Ransomware continues to be one of the most dangerous cyber threat and incident like the one suffered by the city of Atlanta demonstrates that their economic impact on victims could be severe. SamSam ransomware made […]
CVE 2018-8781 Privilege Escalation flaw was introduced in Linux Kernel 8 years ago
Researchers from security firm Check Point discovered a security vulnerability in a driver in the Linux kernel, tracked as CVE 2018-8781, that leads to local privilege escalation. The CVE 2018-8781 flaw, introduced 8 years ago, could be exploited by a local user with access to a vulnerable privileged driver to escalate local privileges and […]
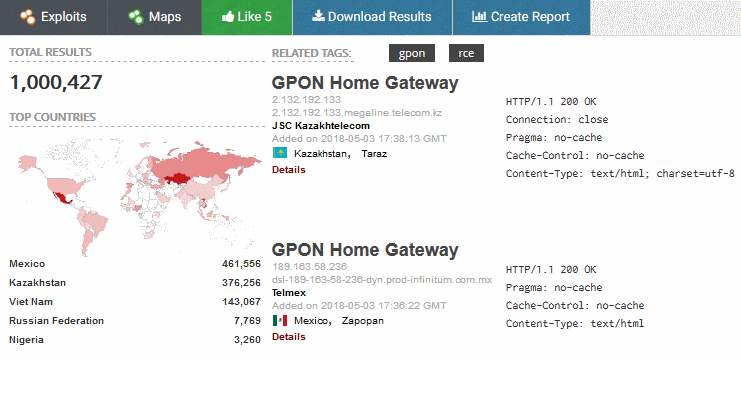
Critical RCE vulnerability found in over a million GPON Home Routers
Security researchers at VPNMentor conducted a comprehensive assessment on of a number of GPON home routers and discovered a Critical remote code vulnerability that could be exploited to gain full control over them. The researchers have found a way to bypass the authentication to access the GPON home routers (CVE-2018-10561). The experts chained this authentication […]
Hackers Scan the Web for Vulnerable WebLogic Servers After Oracle Botches Patch
For more than a week hackers have started scanning the Internet, searching for machines running Oracle WebLogic servers. Scans started after April 17, when Oracle published its quarterly Critical Patch Update (CPU) security advisory. The April 2018 CPU contained a patch for CVE-2018-2628, a vulnerability in the WLS core component of WebLogic, […]
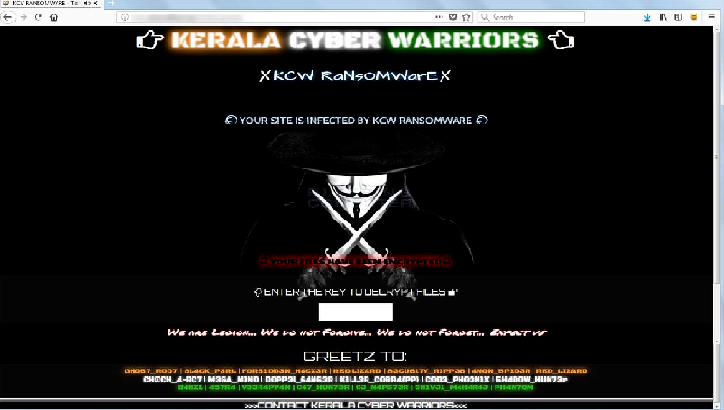
KCW Ransomware Encrypting Web Sites in Pakistan
Team Kerala Cyber Warriors, a hacking group based out of India, have begun to install ransomware on web sites based out of Pakistan. This ransomware, called KCW Ransomware, encrypts the files on a web site and then demands a ransom payment in order to get the files back. You can […]