An Argentinian security researcher named Ezequiel Fernandez has published a powerful new tool yesterday that can easily extract plaintext credentials for various DVR brands and grant attackers access to those systems, and inherently the video feeds they’re supposed to record.
The tool, named getDVR_Credentials, is a proof-of-concept for CVE-2018-9995, a vulnerability discovered by Fernandez at the start of last month.
CVE-2018-9995 —the dangerous flaw that everyone ignored
Fernandez discovered that by accessing the control panel of specific DVRs with a cookie header of « Cookie: uid=admin, » the DVR would respond with the device’s admin credentials in cleartext. The entire exploit is small enough to fit inside a tweet.
$> curl "http://{DVR_HOST_IP}:{PORT}/device.rsp?opt=user&cmd=list" -H "Cookie: uid=admin"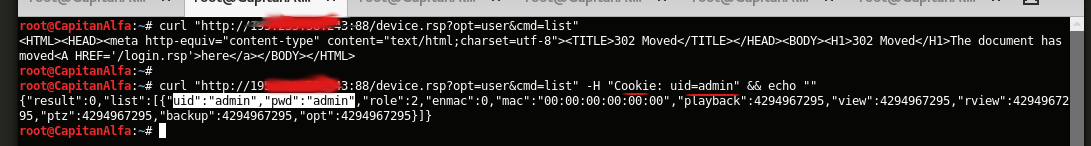
Initially, Fernandez discovered that CVE-2018-9995 affected only DVR devices manufactured by TBK, but in an update to his original report published on Monday, the researcher expanded the list of vulnerable devices to include systems made by other vendors, most of which appeared to be selling rebranded versions of the original TBK DVR4104 and DVR4216 series.
Novo
CeNova
QSee
Pulnix
XVR 5 in 1
Securus
Night OWL
DVR Login
HVR Login
MDVR Login
Tens of thousands of vulnerable devices available online
The researcher estimated the number of vulnerable devices to at least a few tens of thousands. A screenshot of a Shodan query Fernandez used to identify vulnerable devices showed over 55,000 DVRs readily available online, while another showed 10,000 more.
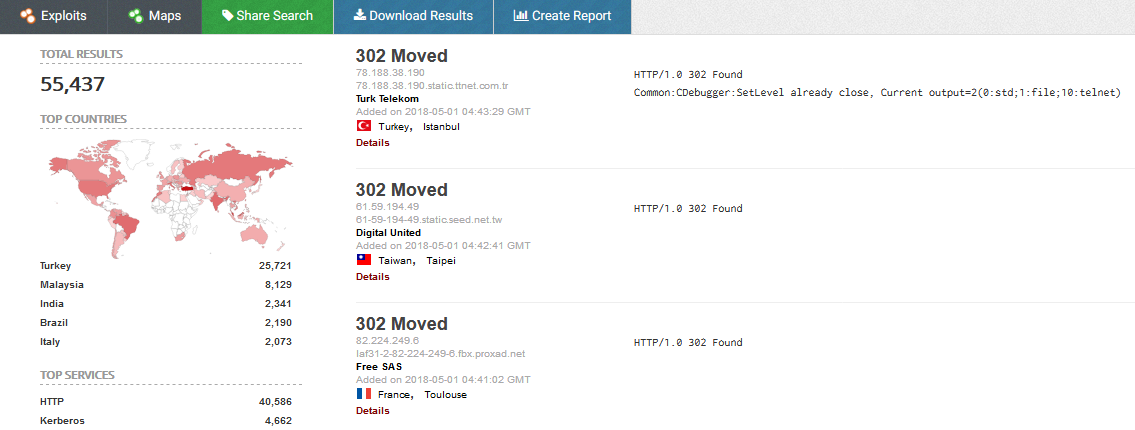
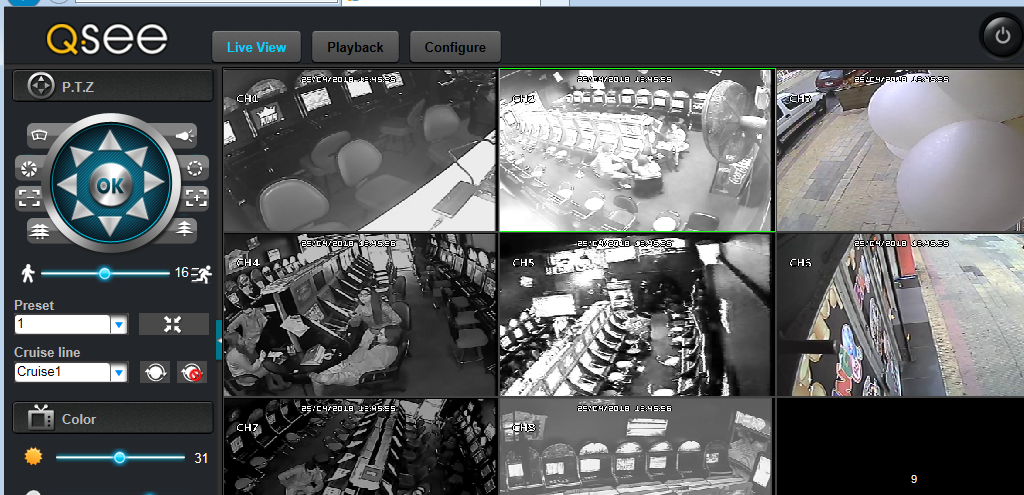
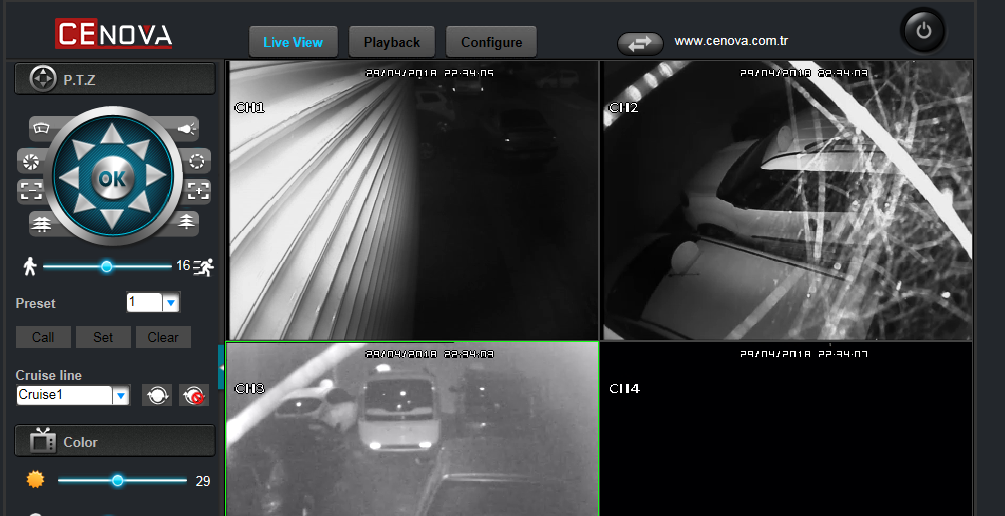
Fernandez also published a few screenshots of devices he gained access to by leveraging CVE-2018-9995 and his tool. The screenshots showed Fernandez having full access to the DVRs’ settings, but also to live video feeds.
 |
 |
 |
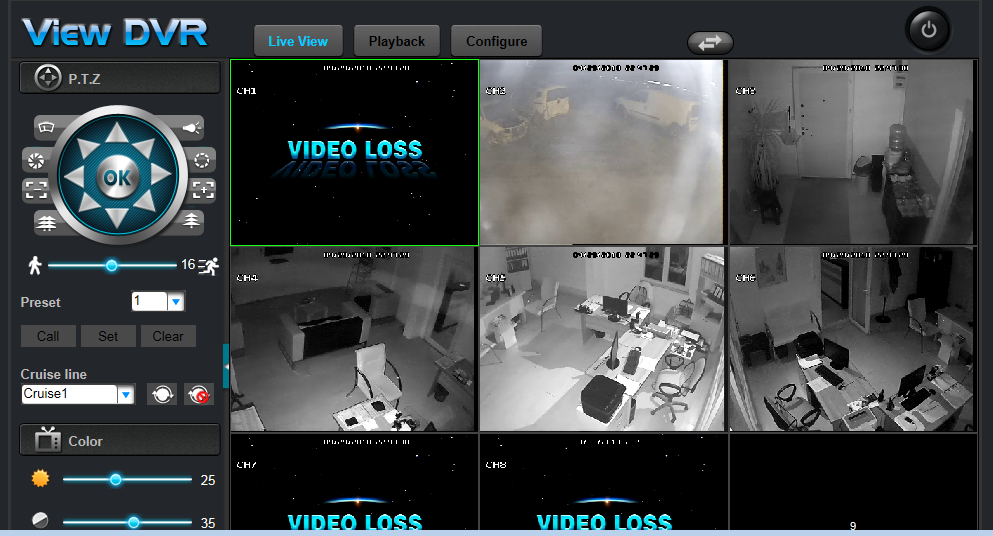 |
There have been websites in the past that leveraged security flaws to aggregate live video feeds from hacked security cameras and DVRs, so Fernadez’s tool might power a new wave of similar portals.
Vulnerability confirmed. No attacks detected just yet.
Bleeping Computer reached out yesterday to a few security researchers to assess the tool’s working state and efficacy.
« I verified the code, and the script smoothly does what it is advertised, providing plaintext credentials for a variety of DVR models at the press of a button, » Ankit Anubhav, Principal Researcher at NewSky Security, a cyber-security company specialized in IoT security, told Bleeping Computer.
« Additionally, the mentioned Shodan dorks provided an accurate source for getting the list of potential devices which are needed to exploit, giving the attacker answers to two critical questions, ‘who’ to attack and ‘how’ to attack, » Anubhav said, pointing out that the GitHub repo also contains the Shodan searches someone would need to identify vulnerable devices.
Fernandez declined to comment for this article, fearing he might be misunderstood or misquoted due to his insufficient knowledge of the English language.
But his insufficient English might have also been the reason why CVE-2018-9995 was never popular with IoT botnet herders in the past month, ever since Fernandez published his first blog post on this vulnerability.
An exploit this easy to exploit and which grants such access to devices should not have been ignored all these past weeks.
There were no massive scans for CVE-2018-9995, and there don’t appear to scans for CVE-2018-9995 yesterday, either, after Fernandez published this tool.
« Not seeing anyone scan the Internet strictly for /login.rsp or /device.rsp, » Andrew Morris, Founder of GreyNoise Intelligence, a company that catalogs Internet-wide scanner activity, told Bleeping Computer yesterday.
CVE-2018-9995 is the next GoAhead debacle
But Anubhav doesn’t see this flaw remaining an unknown for long, especially after the PoC’s publication on GitHub.
« NewSky Security has recently seen a few IoT exploits weaponized in the wild, but they were vendor-specific, i.e., CVE-2017-17215 (Huawei), CVE-2017-18046 (Dasan), and ChimayRed (Mikrotik), » Anubhav told us. « With CVE-2018-9995 added to the equation, now, one can expect scans and damages done at the level of another cross-vendor IoT exploit, CVE-2017-8225 (GoAhead). »
What Anubhav is referring to is a famous vulnerability affecting the firmware of IP security cameras manufactured GoAhead, which the company sold as white-label (non-branded) products to many other companies. For the past two years, these cameras have been attacked on a daily basis by most IoT botnets looking for new devices to infect.
With tens of thousands of TBK DVRs available online under different brands, with publicly-available PoC code, and an easy-to-exploit scripting-friendly routine, CVE-2018-9995 will, for sure, become one of the most scanned and most exploited security bugs of the year.
Mitigation possible
For now, barring modifications to the PoC code, Anubhav says companies can detect attacks and block them.
« Usage of the PoC code can be easily identified as it uses a mock user-agent with the [mispelled] terms of ‘Morzilla’ and ‘Pinux x86_128’ instead of Mozilla and Linux x86_128, » Anubhav pointed out.
« However, attackers with a basic skillset can change the script for their own usage, as the exploit is fairly straightforward to understand, » Anubhav said, referring to the fact that attackers can modify the user-agent string and other constants present in the script.
Nonetheless, companies can still detect attempts to access /login.rsp or /device.rsp URL paths and block those, allowing access to the DVR’s management interface only for trusted IPs.
« With the code being made public, the question is not about whether the vulnerable devices will be compromised, it is more in the lines of how soon the attackers will pick up on it, » Anubhav warned.
To read the original article:https://www.bleepingcomputer.com/news/security/new-hacking-tool-lets-users-access-a-bunch-of-dvrs-and-their-video-feeds/
