It has been a pretty slow ransomware week as most of the malware developers have started pushing cryptominers. We did see the continued distribution of the GnuPG based Qwerty Ransomware and a new variant of the GandCrab ransomware that makes it secure again.
March 3rd 2018
New GlobeImposter discovered
GrujaRS found a new GlobeImposter variant that utilizes the extension .encrypt and drops a ransom note named instructions.html.
March 4th 2018
New Jigsaw Ransomware variant
Michael Gillespie found a new Jigsaw Ransomware variant that uses the extension .Bitconnect and new extortion text wanting you to take a photo of yourself to post on Instagram.
![]()
March 5th 2018
RotorCrypt Ransomware updated
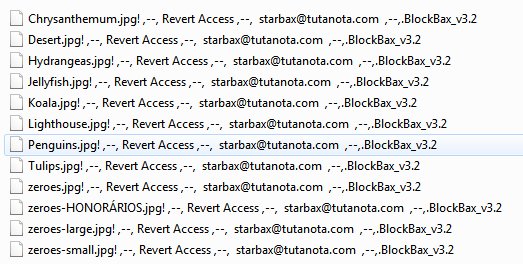
Michael Gillespie found a RotorCrypt Ransomware that appends the extension ! ,–, Revert Access ,–, starbax@tutanota.com ,–,.BlockBax_v3.2.
March 6th 2018
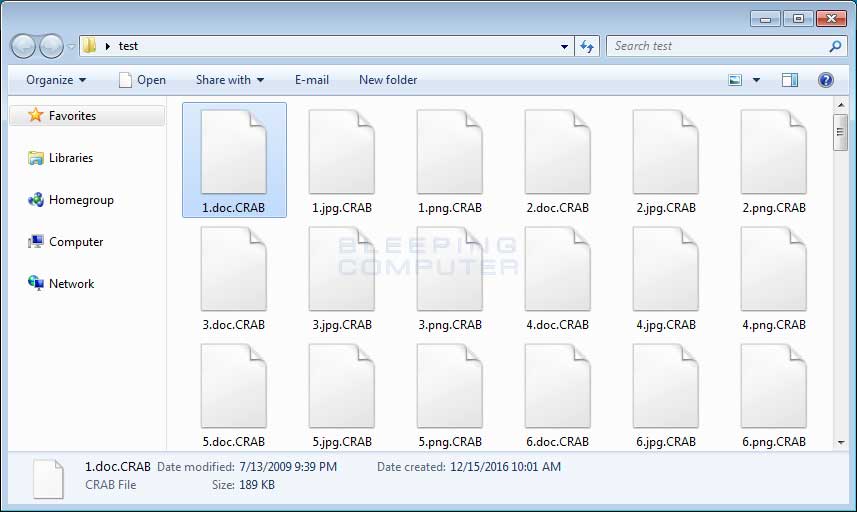
GandCrab Ransomware Version 2 Released With New .Crab Extension & Other Changes
MalwareHunterTeam discovered that GandCrab version 2 was released, which contains changes that supposedly make it more secure and allow us to differentiate it from the original version. In this article we will provide a quick overview as to what has changed and how you can identify that you are are infected with the GandCrab Ransomware.
Cryakl Ransomware upgrade to version v1.5.1.0
Michael Gillespie noted that Cryakl Ransomware has been updated to version 1.5.1.0 based on a ransom note submitted to ID Ransomware.
Spanish Jigsaw Ransomware discovered
Michael Gillespie found a new Spanish Jigsaw Ransomware variant that appends the .jes extension and utilizes a Cthulhu background image. Michael’s decryptor was updated to handle this variant.

March 7th 2018
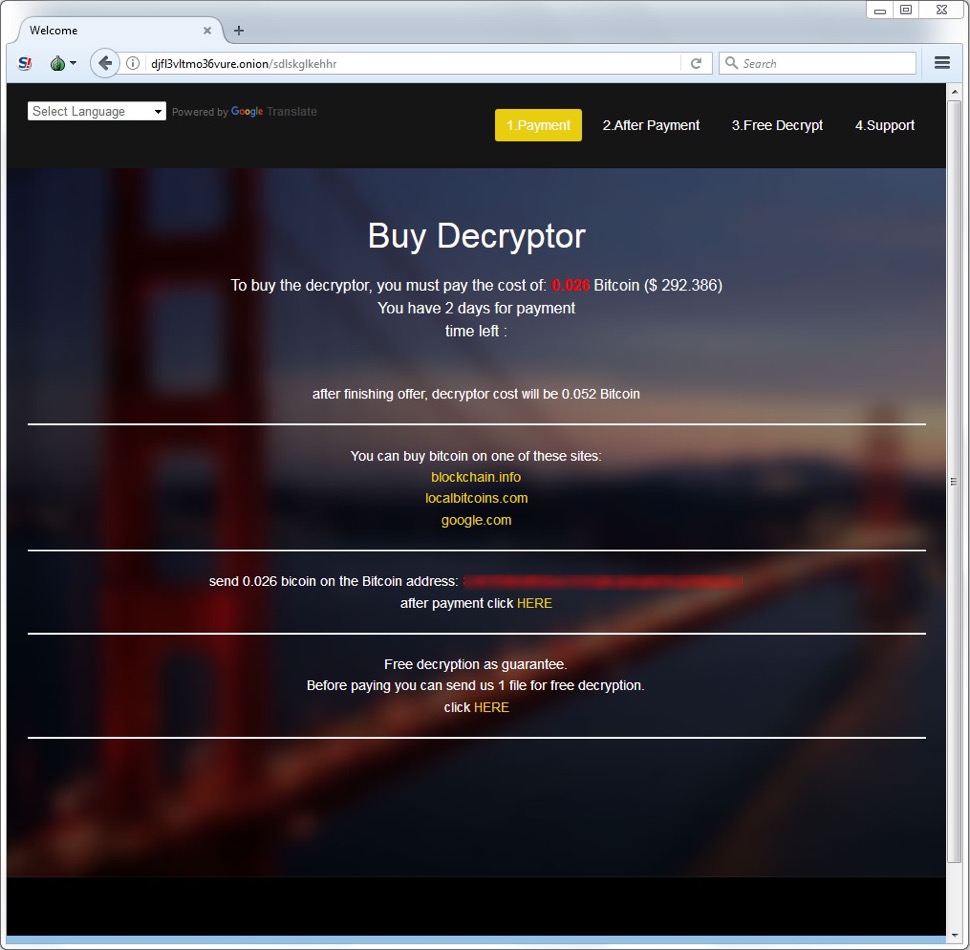
GlobeImposter gets a facelift, GandCrab is still out there
Brad Duncan analyzes a new malspam campaign that is pushing GandCrab and a GlobeImposter that had a redesign.
SilentSpring Ransomware discovered
MalwareHunterTeam discovered a new ransomware called SilentSpring. This ransomware appends the .Sil3nt5pring extension to encrypted files.
Encryption 101: How to break encryption
Malwarebytes posted a good primer on how to break encryption.
March 9th 2018
Only Half of Those Who Paid a Ransomware Were Able to Recover Their Data
A massive survey of nearly 1,200 IT security practitioners and decision makers across 17 countries reveals that half the people who fell victim to ransomware infections last year were able to recover their files after paying the ransom demand.
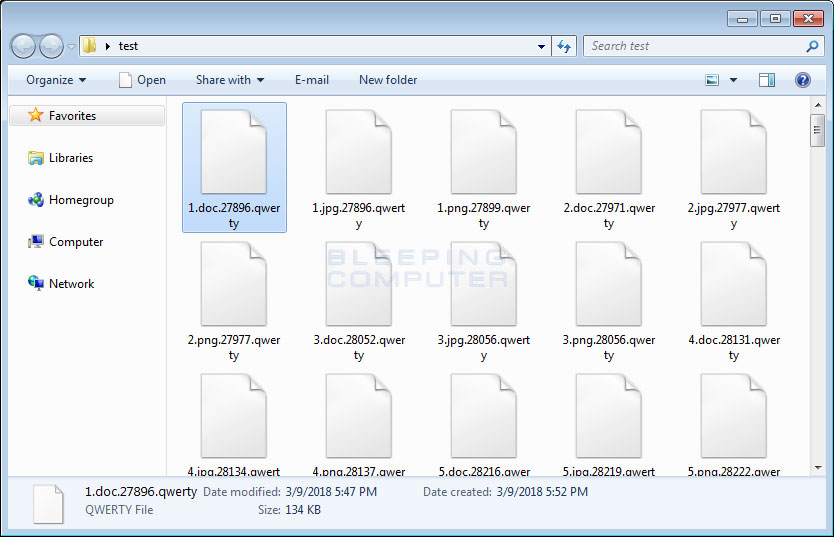
Qwerty Ransomware Utilizes GnuPG to Encrypt a Victims Files
A new ransomware has been discovered that utilizes the legitimate GnuPG, or GPG, encryption program to encrypt a victim’s files. Currently in the wild, this ransomware is called Qwerty Ransomware and will encrypt a victims files, overwrite the originals, and the append the .qwerty extension to an encrypted file’s name.
FRS Ransomware discovered
Karsten Hahn discovered the FRS Ransomware that appends the .FRS extension to encrypted files and drops a ransom note named READ_ME_HELP.png and READ_ME_HELP.txt.
To read the original article:
