The exploit kit landscape has continued its downfall started in the summer of 2016 and its leading player —the RIG exploit kit— has stopped delivering any ransomware strains in 2018, focusing now on spreading cryptocurrency miners (coinminers) and information-stealing trojans (infostealers).
These are the main conclusions of months of observation by Palo Alto Network security researcher Brad Duncan.
Exploit kit market continues to fall
Duncan, one of the leading specialists in malvertising campaigns and exploit kit usage, has been one of the first to notice the declining state of the exploit kits —web-based applications that facilitate the delivery of malicious code to vulnerable and outdated browsers.
The expert pointed out last year that the exploit kit market, which started a general decline in the summer of 2016, has continued to fall in the first half of 2017. In a blog post today, Duncan says that fall has continued all throughout 2017 and the first month of 2018.
No large EK operation has surfaced on the exploit kit market in 2017, but two major players —Sundownand Neutrino— faded out instead.
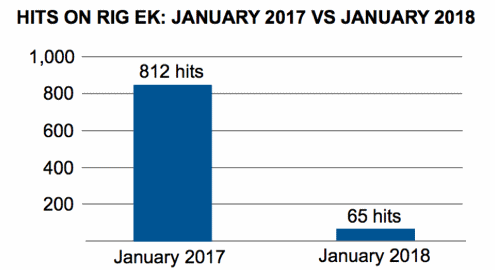
RIG has continued to dominate detections for exploit kit activity, but these detections are a fraction of what RIG used to get. Looking at Palo Alto’s internal data, Duncan reveals a sharp drop in RIG EK, activity from 812 monthly campaigns in January 2017 to only 65 in January 2018.
Duncan says various reasons contributed to RIG and the EK landscape’s downfall, such as modern browsers getting harder to hack, Flash use going down after major browsers switched to an HTML5-first policy, and several coordinated takedowns aimed at EK operations.
Current state of exploit kits
Even cybercriminals have noticed the hard times exploit kits are going through, and many have switched to email spam or social engineering (spear-phishing, tech support scams).
Currently, exploit kits are nothing more today than a dying fad with a strong clientele that continues to rely on them for spreading various sorts of malware strains. But even this clientele will abandon EK operators once they stop infecting enough users. Below is Duncan’s review of what’s left of the exploit kit landscape in 2018.
[…]
None of the ransomware we saw being distributed using Rig EK in January 2017 was being distributed in 2018. Cerber, CryptoMix, CryptoShield, Locky, and Spora are no longer active.
[…]
Similarly, none of the campaigns we saw pushing ransomware in January 2017 were doing so in January 2018. The Afraidgate and pseudo-Darkleech campaigns disappeared by May 2017. Criminals behind the EITest campaign are still active, but they stopped using Rig EK and have turned to social engineering methods like fake browser plugins and tech support scams.
[…]
In January 2018, Rig EK was used by at least three identifiable campaigns: Fobos, Ngay, and Seamless. Fobos has used Rig EK to distribute the Bunitu proxy Trojan. Ngay has distributed coin miners and information stealing malware. Seamless has mainly distributed an information stealing Trojan named Ramnit.
Barring the discovery of a slew of non-Flash exploits to power a new generation of EKs, all exploit kits are primed for extinction. Right now, all security researchers are rubbing their hands waiting for the end to come.
To read the original article: