Crooks have infected over 40,000 web servers, modems, and other IoT devices with the Prowli malware as part of a cryptocurrency mining campaign and to redirect victims to malicious sites.
The Prowli malware was spotted by researchers at GuardiCore, attackers composed the huge botnet by exploiting known vulnerabilities and brute-force attacks.
This campaign, dubbed Operation Prowli, aimed at servers and devices using the following arrack methods, including:
- Using a self-propagating worm that targets systems running SSH by brute force credential guessing, then the infected machines download and run a cryptocurrency miner.
- Exploiting the CVE-2018-7482 file download vulnerability to compromise Joomla! Servers running the K2 extension
- Accessing the internet facing configuration panel of variety of DSL modems by using a URL such as http://:7547/UD/act?1 and passing in parameters exploiting a known vulnerability. The vulnerability affects the processing of SOAP data and allows remote code execution. This vulnerability was previously used by the Mirai worm.
- Using several exploits and launching brute-force attacks o admin panel of WordPress sites.
- Exploiting a 4-year-old vulnerability, CVE-2014-2623, to execute commands with system privileges on servers running HP Data Protector exposed to the internet (over port 5555).
- Targeting Drupal, PhpMyAdmin installations, NFS boxes, and servers with exposed SMB ports via brute-force credentials guessing.
Once attackers have compromised a server or an IoT device, they determine if they can use it for cryptocurrency mining operations. Hackers used a Monero miner and the r2r2 worm, a piece of malware used to launch SSH brute-force attacks from the hacked devices.
“The attackers behind Prowli incur no expenses when they use r2r2 to take over computers owned by others and use mining pools to launder their gains. Cryptocurrency is a common payload of modern worms, and in this case as in many others, our attackers prefer to mine Monero, a cryptocurrency focused on privacy and anonymity to a greater degree than Bitcoin.” reads the analysis published by the experts.
“Second source of revenue is traffic monetization fraud. Traffic monetizers, such as roi777, buy traffic from “website operators” such as the Prowli attackers and redirect it to domains on demand. Website “operators” earn money per traffic sent through roi777. The destination domains frequently host different scams, such as fake services, malicious browser extensions and more.”
The hackers also compromised servers with the WSO Web Shell backdoor. Hacked websites were used to host malicious code that redirects visitors to a traffic distribution system (TDS), with such kind of attack scheme crooks monetize their efforts by selling hijacked traffic.
“Traffic monetizers, such as roi777, buy traffic from “website operators” such as the Prowli attackers and redirect it to domains on demand. Website “operators” earn money per traffic sent through roi777. The destination domains frequently host different scams, such as fake services, malicious browser extensions and more.” continues the experts.
Further details on the Prowli campaign, including IoCs are reported in the analysis published by GuardiCore.
[Prowli Operation] Victims by Industry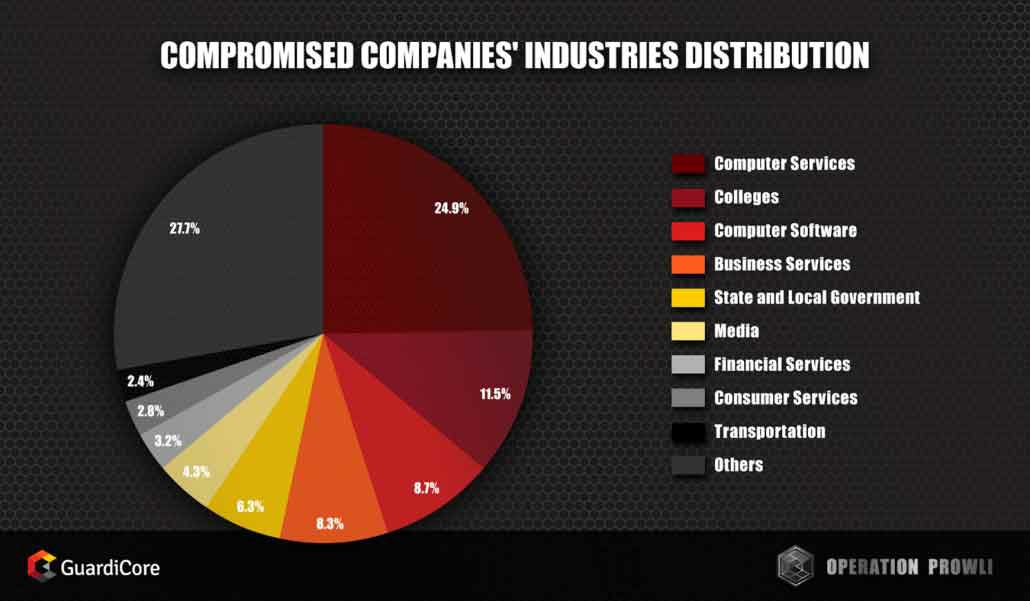
[Prowli Operation] Most of the victims ran with weak SSH credentials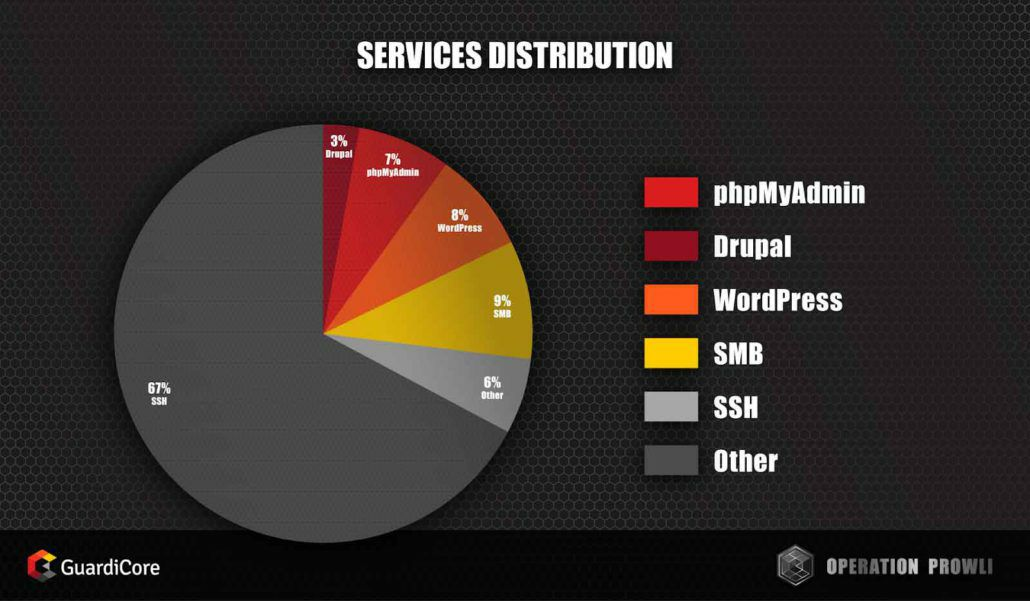
[Prowli Operation] Operation Prowli’s victims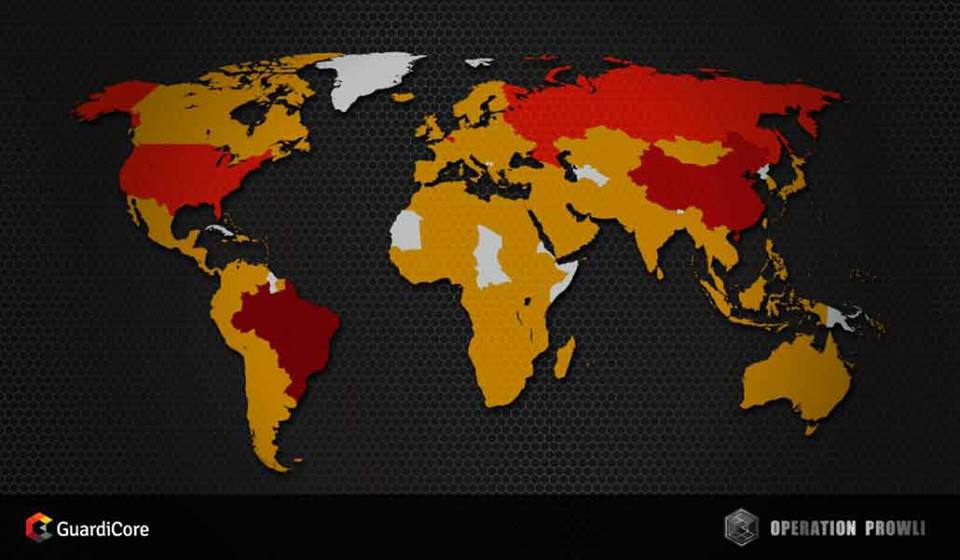
To read the original article
https://securityaffairs.co/wordpress/73265/malware/prowli-campaign.html

