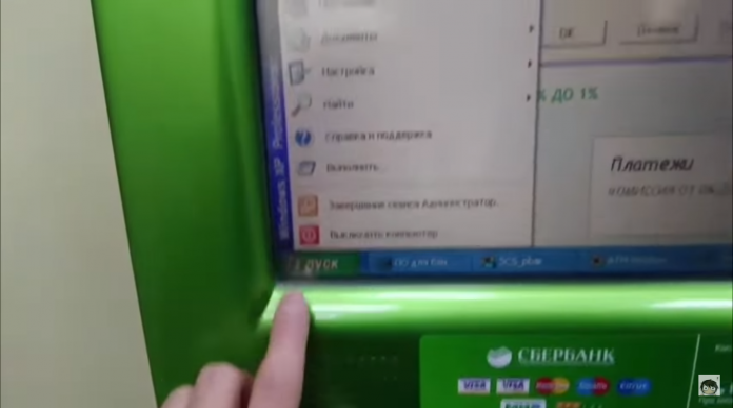
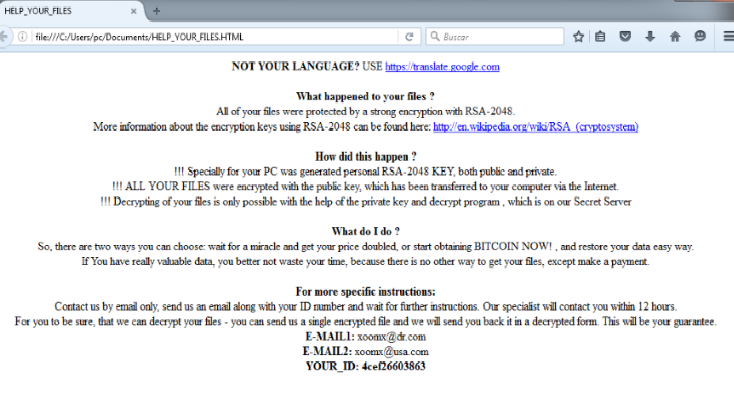
All ATMs that are still running on Microsoft’s 16-year-old Windows XP operating system are at the risk of getting hacked easily, as the OS is no longer supported by the Redmond giant except for emergency security patches (for instance, patch blocking the WannaCry ransomware released this year). An employee of Russian […]
Facebook messenger falls victim to an anonymous crypto cousin of Bitcoin
With the booming value of digital currency, numerous hackers are rolling out schemes to unwittingly trap or trick more likely, the regular web users into mining for them. The most recent scheme to hoodwink people into mining cryptographic money is exploiting Facebook Messenger by means of some shrewd malware.The malware […]
Protégé : CCA CTF I Qualifier Writeups PART 1
Il n’y a pas d’extrait, car cette publication est protégée.
Schneider Electric Patches Flaws in Pelco VideoXpert Enterprise product
Schneider Electric recently released a firmware update for its Pelco VideoXpert Enterprise product that addresses several vulnerabilities, including a high severity code execution flaw, tracked as CVE-2017-9966. The Pelco VideoXpert solution is widely used in commercial facilities worldwide. The security researcher Gjoko Krstic has found two directory traversal bugs and an […]
The Week in Ransomware – December 22nd 2017 – WannaCry, Arrests, & More
The holidays are upon us and that means even ransomware developers are taking some time off. This showed this week with very few ransomware infections being released and for the most part we have only seen new variants of existing infections. The biggest news is the U.S. government officially attributing the […]
Experts from Bleeping Computer spotted a new Cryptomix Ransomware variant
Security experts spotted a new variant of the CryptoMix ransomware that uses a different extension (.FILE) and a new set of contact emails. Security experts from BleepingComputer discovered a new variant of the CryptoMix ransomware that uses a different extension (.FILE) to append to the file names of the encrypted files and uses new contact emails. For […]
Cayla: A Toy That Connects Hackers To Your Life
Toys are amazing, and kids love them. They are being sold like hot cakes these days thanks to the holiday season. However, quite recently, a toy in the market has been doing a lot more than just make children happy. Cayla is a toy doll that responds to questions. That’s […]
Security Researchers prove that Windows 10 Facial Recognition can be breached with a Photo
Their spoofing attempts were declared on the cybersecurity site Seclists on Dec. 18. The cybersecurity experts bypassed Windows Hello which is Microsoft’s password-free security Lock on both a Dell and Microsoft laptop operating different versions of Windows 10, which is the reason for concern for anyone utilizing this feature to log into […]
5 Common network channels used by malware
Living in a modern digital era of computers can bring a lot of risks including data exfiltration to you and your PC. Computers are extremely vulnerable, and if the person on the other side of your network knows how to find the exact loophole in the system – you may suffer […]
Fake Prime Express Travel statement delivers Globeimposter ransomware
The next in the never ending series of malware downloaders from the Necurs botnet is an email with the subject of Outstanding Statement pretending to come from Prime Express Oldham <sales62@primeexpressuk.com> ( random numbers after sales) delivering Globeimposter ransomware They use email addresses and subjects that will entice, persuade, scare or shock a […]