The holidays are upon us and that means even ransomware developers are taking some time off. This showed this week with very few ransomware infections being released and for the most part we have only seen new variants of existing infections.
The biggest news is the U.S. government officially attributing the WannaCry Ransomware to North Korea. Other big news are various arrests associated with affiliates of Cerber and CTB-Locker.
Contributors and those who provided new ransomware information and stories this week include: @DanielGallagher, @Seifreed, @BleepinComputer, @FourOctets, @malwrhunterteam, @malwareforme, @fwosar, @campuscodi, @PolarToffee, @demonslay335, @hexwaxwing, @jorntvdw, @LawrenceAbrams, @struppigel, @sdkhere, @Amigo_A_, @FortiGuardLabs, @TomBossert45, @WSJ, @ITSimplifie.
December 18th 2017
New variant of the RSAUtil Ransomware
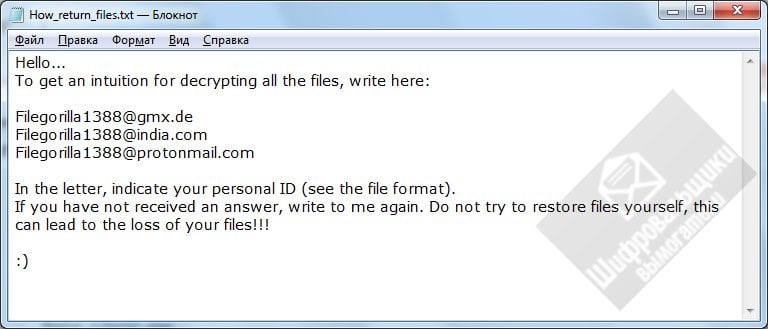
Amigo-A discovered a new variant of the RSAUtil Ransomware that uses the extension .ID.GORILLA and drops a ransom note named How_return_files.txt.
Satan Cryptor Ransomware 2.0 discovered
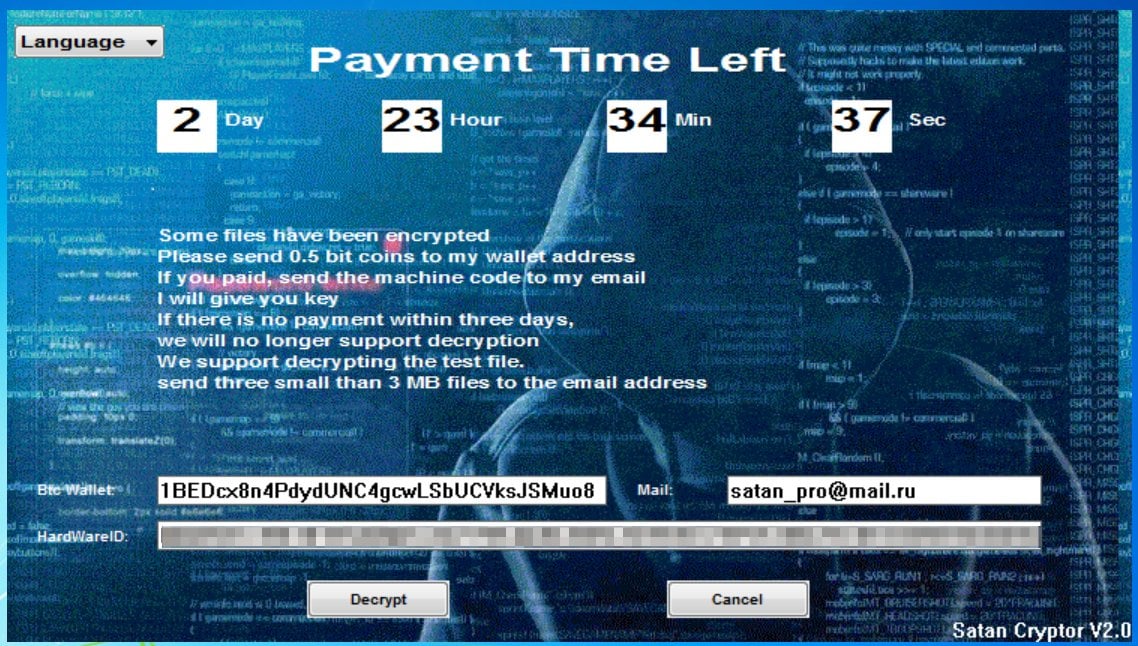
Jack discovered the Satan Cryptor 2.0 Ransomware that appends the .satan extension and tries to spread via SMB.
Fake bitcoin multiplier installs ransomware
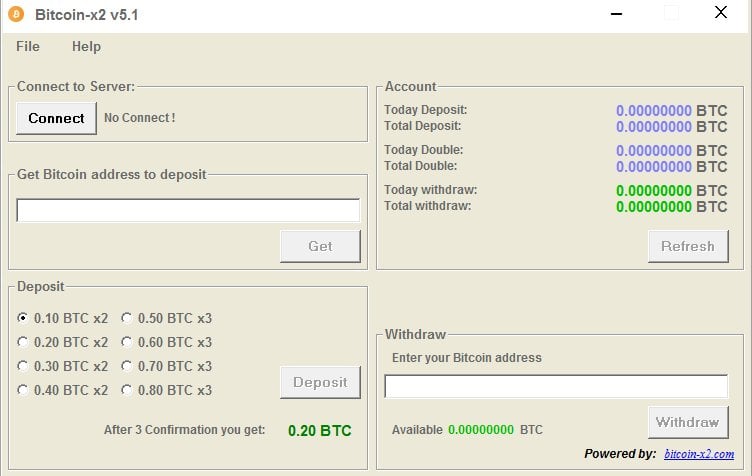
SDK discovered a fake bitcoin multipler that installs ransomware.
December 19th 2017
White House Officially Blames North Korea for WannaCry Ransomware Outbreak
In an op-ed in the Wall Street Journal, President Trump’s Homeland Security Adviser Thomas Bossert has officially blamed North Korea for the WannaCry ransomware incident that devasted hundreds of thousands of computers worldwide in May this year.
GlobeImposter with the .wallet extension
Michael Gillespie discovered a new GlobeImposter ransomware variant that appends the .wallet extension.
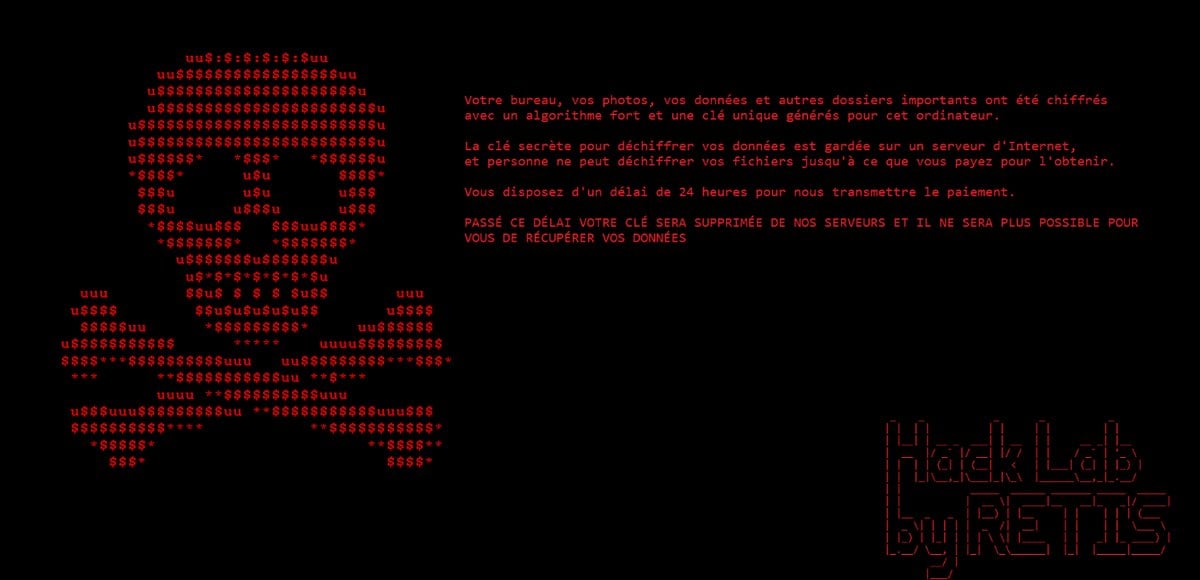
Retis Ransomware Discovered
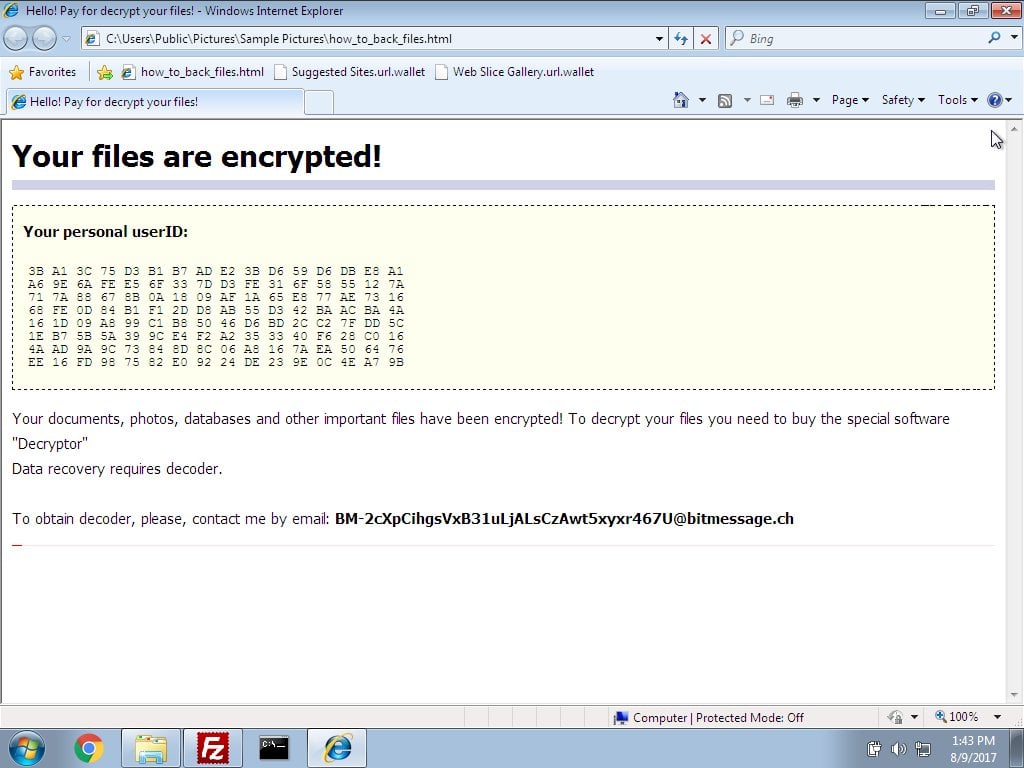
SDK discovered the Retis Ransomware that appends the .crypted extension to encrypted files.
Another RSAUtil variant discovered
Amigo-A discovered another RSAUtil Ranssomware variant. This one appends the extension .ID.VENDETTA.
December 20th 2017
Five Romanians Arrested for Spreading CTB-Locker and Cerber Ransomware
Romanian authorities have arrested five people on accusations of spreading email spam that infected users with the CTB-Locker and Cerber ransomware families.
December 21st 2017
Hackers Used DC Police Surveillance System to Distribute Cerber Ransomware
A Romanian man and woman are accused of hacking into the outdoor surveillance system deployed by Washington DC police, which they used to distribute ransomware.
VenusLocker Ransomware Gang Switches to Monero Mining
FortiGuard Labs released research about how the criminal group behind previous campaigns that have spread the VenusLocker ransomware have now switched their focus to delivering a Monero cryptocurrency miner instead.
GlobeImposter variant being spread via malspam
Eric Taylor discovered that a GlobeImposter variant that appends .doc is being spread via malspam with JS downloaders.
Security Brief: The French Retis Ransomware Appends .Crypted
The Retis Ransomware was discovered by security researcher SDK on December 19th 2017. This is a .NET ransomware, so its source code is easily accessible. When started it will first target the victim’s Desktop, Documents, and Pictures folder for encryption. After encrypting those folder, it will target the rest of the drives on the computer.
File-Locker Ransomware Targets Korean Victims and asks for 50K Won
This is a quick analysis of a ransomware discovered by Lawrence Abrams called File-Locker. This brief will contain technical information related to how it infects a computer, how it is distributed, and whether it can be decrypted or not.[…]
To read the original articlehttps://www.bleepingcomputer.com/news/security/the-week-in-ransomware-december-22nd-2017-wannacry-arrests-and-more/
