Living in a modern digital era of computers can bring a lot of risks including data exfiltration to you and your PC. Computers are extremely vulnerable, and if the person on the other side of your network knows how to find the exact loophole in the system – you may suffer from huge loss of data and permanent damage to your PC.
Even your personal data can be lost, and we are not talking here just about the firewall. A firewall can help, and it does in fact help, but there are a lot of other channels that can make your computer vulnerable to all sorts of malware.
For example, leaving a trace while Tweeting, different forum posting, etc. These are all things that represent the specific types of channels that an attacker can find to get in your system. One of the best indicators of how much malware is spread is in the statistics. Math does not lie, and here are the facts:
1: Simple browser attacks account for almost half of the attacks (45%), and it is done by tracing the packets you sent to a specific website.
2: Android malware has had exponential growth – in the past year, malware in the Google Play Store has risen by amazing 388 percent.
3: Software that is not updated, especially Java and Flash; there are some big companies that still use Java 6 today, which is extremely vulnerable.
4: Leaving statistics aside, here are the 5 most common ways attackers get their malware into your system, and how you could defend against it.
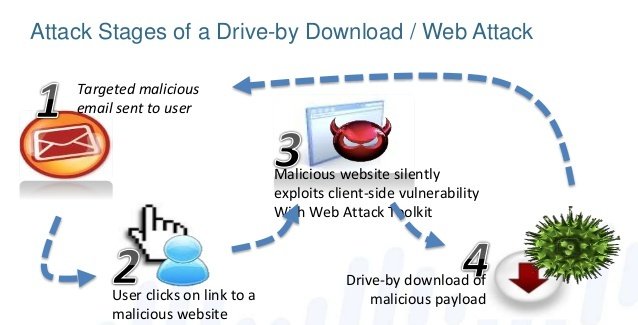
1. Drive-By Download
It is obvious; anybody can put anything into a file and name it whatever he or she wants. It may look legit to you, and you do not know until you download and open it.
As reports from Palo Alto say, a huge majority of malware entrances into systems are with a drive-by download. The best cure for this is to scan your computer and file first – before you open it.
There are many software services for that; you can check out everything about it here.
2. Email And Instant Messaging
You would be surprised with the statistics of email malware. Biggest data exfiltration in the past has occurred via email and messaging systems. A huge majority of email sent today contains some kind of malware.
Luckily the services we use such as Gmail, Yahoo, and Outlook possess a certain level of security – so you have filters for spam as well as the service sometimes not even letting you open a certain file.
This technique is also called phishing, and it has different purposes – from hacking social media accounts to tracking your keystrokes and getting all your computer data emailed directly to them.
They can even be pre-programmed, so the malware gets spread from your email without you knowing about it. Be careful what you open and whom it’s from!

3. USB Drives
All of the USB devices have a file called autorun. That is the way they work, as soon as you put it on your PC, the autorun is being started, and that is the first thing that happens when plugging your USB in.
However, the problems begin when you realize that this autorun file can be changed and modified. There were some very popular USB attacks in the past, used to spy on people, watch their screen and what they are doing. […]
To read the original article: