Malware researchers at CSE Cybsec – ZLab have analyzed a new variant of Mobef ransomware, a malware that in the past mainly targeted Italian users. Malware researchers at CSE Cybsec – ZLab have analyzed a new variant of Mobef ransomware, that was involved in past attacks against Italian users. I […]
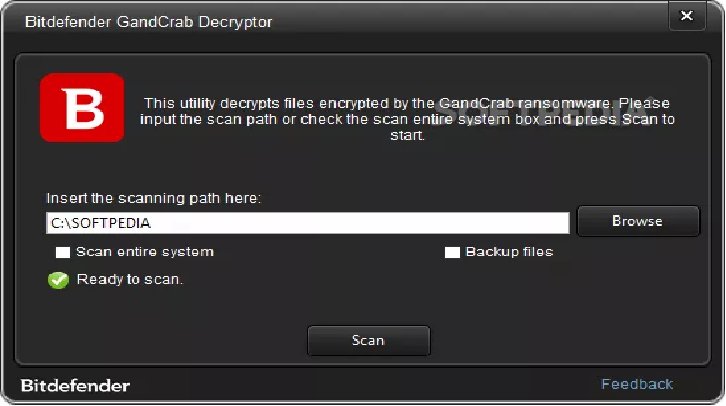
Victims of the GandCrab ransomware can decrypt their files for free using the decryptor
The GandCrab ransomware decryptor has been released by the Romanian Police (IGPR) under the supervision of the General Prosecutor’s Office (DIICOT) and in collaboration with the internet security company Bitdefender and Europol. Bitdefender has teamed up with Europol, the Romanian Police, and the Directorate for Investigating Organized Crime and Terrorism (DIICOT) […]
Hundreds of sites based on WordPress, Joomla and CodeIgniter infected by ionCube Malware
Security researchers at the firm SiteLock have discovered that hundreds of websites have been infected with the ionCube malware. Security researchers at SiteLock have discovered that hundreds of websites have been infected with malware that masquerades as legitimate ionCube-encoded files. ionCube is an encoding technology used to protect PHP software from being […]
Infamous Russian Cyber-Espionage Group Hacks German Government
APT28, an infamous cyber-espionage unit that many security firms believe is acting at the behest of the Russian government, has hacked various German government agencies for more than a year. According to German news agency dpa, Russian hackers infiltrated computers on the network of the German Foreign Ministry, the German Defence […]
Unprotected AWS Bucket Exposes 50.4 GB of Financial Giant’s Data
Another day, another AWS Bucket exposed to the public – This time the AWS Bucket belonged to Birst. The Cyber Risk Team at Cloud security firm UpGuard have discovered a massive trove of data exposed due to an unprotected Amazon Web Services (AWS) S3 bucket. The database belonged to Birst, a Cloud Business […]
Mobile banking Trojans spread confusion worldwide
Consumers around the world that use mobile banking apps are at a greater risk of being tricked by cybercriminals and falling victim to mobile banking theft. This is according to new global research from Avast, which asked almost 40,000 consumers in Spain and eleven other countries around the world to compare the […]
New RedDrop Android Spyware Records Nearby Audio
A new Android malware strain named RedDrop can perform a vast array of malicious actions, including recording nearby audio and uploading the data to cloud-storage accounts on Dropbox and Google Drive. The malware was first spotted by UK mobile security firm Wandera on the phones of employees of several global […]
Memcache Servers Can Be Abused for Insanely Massive DDoS Attacks
Crooks can abuse Memcache servers to launch insanely massive DDoS attacks using very few computational resources on their end. These type of DDoS attacks are possible because of the unsecured way Memcache developers have implemented support for the UDP protocol in their product. Furthermore, to make matters worse, Memcache servers […]
Cisco IOS and IOS XE Software Crafted Network Time Protocol Packets Denial of Service Vulnerability
A vulnerability in the processing of Network Time Protocol (NTP) packets by Cisco IOS and Cisco IOS XE could allow an unauthenticated, remote attacker to cause an interface wedge and an eventual denial of service (DoS) condition on the affected device. The vulnerability is due to insufficient checks on clearing […]
SAML Vulnerability Lets Attackers Log in as Other Users
Security researchers from Duo Labs and the US Computer Emergency Response Team Coordination Center (CERT/CC) will release security advisories today detailing a new SAML vulnerability that allows malicious attackers to authenticate as legitimate users without knowledge of the victim’s password. The flaw affects SAML (Security Assertion Markup Language), an XML-based markup language […]