New versions of the SamSam ransomware will not execute unless the person running the malware’s payload enters a special password via the command-line.
This is a new protection mechanism added by the SamSam crew in a recent SamSam version discovered by Malwarebytes researchers.
Previous versions did not feature this mechanism, meaning anyone who found a SamSam binary could have infected his computer by double-clicking and running the file.
Modification aimed at security researchers
But the addition of this password-protection system has nothing to do with end users.
The SamSam ransomware is the creation of a group who deploys it only on rare occasions, usually after hacking into the private networks of large companies or government institutions. The ransomware is not something someone finds in spam emails or lying around the web.
The password has been added to prevent security researchers from executing the ransomware binary, in case they stumble upon a working version, and limit what kind of information they can gather about the SamSam’s latest version.
Researchers say this is a new addition to the SamSam ransomware, a strain that has slowly evolved in the past year. Proof stands recent reports from fellow cyber-security firms that have also analyzed the ransomware, but where the password-protection system was not in place.
For example, reports from Sophos, Crowdstrike, Secureworks, and a previous Malwarebytes analysis did not mention the password-protection system that appears to have been added this month.
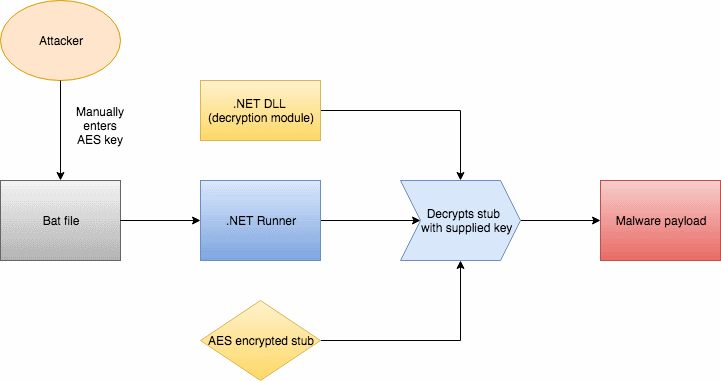
« That password appears to be set at compile time, which means each campaign may have a different password associated with it, » Allan Liska, Senior Solutions Architect at Recorded Future, told Bleeping Computer.
« While, to the best of our knowledge, the SamSam group is not a nation state actor, these tactics, protecting the code from security researchers and limiting the exposure of your tools, are very similar to what nation state actors do, » Liska added.
Timeline of SamSam attacks in 2018
While other ransomware strains are more widespread, being the subject of massive malspam and exploit kit-based distribution efforts, such as Dharma, GlobeImpostor, or Scarab, the SamSam ransomware is today’s most famous and well-known strain.
This is because the group behind SamSam has been quite active in the first quarter of 2018, hitting countless of targets such as hospitals, city councils, ICS firms, state agencies, and many more.[….]
To read the original article:
