Since its discovery early this year, the Hide and Seek IoT botnet has been increasing its infection capabilities with new vectors. The latest samples look for Android devices with the wireless debugging feature enabled.
While IoT botnets appear and go away on a daily basis, Hide and Seek first attracted attention through its rapid growth to over 90,000 devices in a just a few days.
The new infection mechanism observed in the latest version does not exploit a vulnerability, but a misconfiguration of the devices, which ship with an active Android Debug Bridge connection over WiFi.
By default, Android has this option turned off, but device makers enable it in production stage to customize the operating system for their products. Users have to activate it manually.
Thousands of devices ready for the plucking
By leveraging this oversight from device manufacturers, Hide and Seek stands to expand its reach to tens of thousands of potential bots.
Security researchers at Bitdefender have been tracking the botnet since January 10, and monitored the new functionalities added to the new versions.
« The newly identified samples add functionality by exploiting the Android Debug Bridge (ADB) over Wi-Fi feature in Android devices, which developers normally use for troubleshooting, » says Liviu Arsene, Senior E-Threat Analyst.
Exploiting the open ADB connection is not new. It was first reported back in February for a botnet that dropped a cryptocurrency miner.
According to Bitdefender, Hide and Seek can add 40,000 new devices to its army of bots, most of them in Taiwan, Korea, and China.
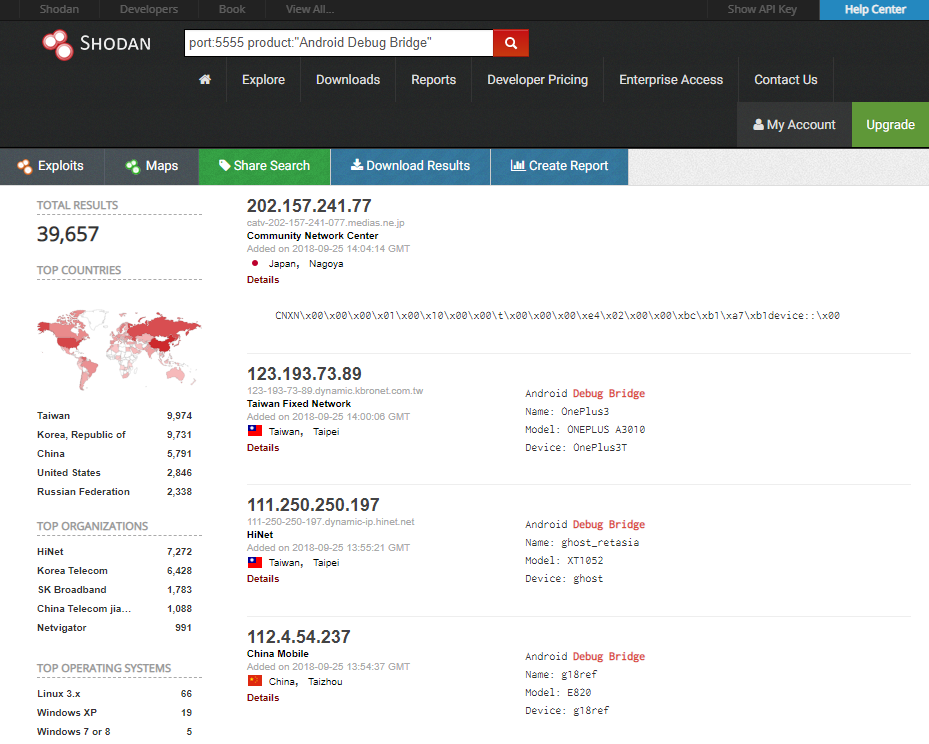
Growing seems to be the current objective
In a conversation with BleepingComputer, Chief Security Researcher at Bitdefender Alex Balan said that the botnet’s purpose for the moment appears to be to increase its size and nothing more.
Although it supports commands for data exfiltration and code execution the researchers have not seen them used by the botnet. Also, there is no module for launching distributed denial-of-service attacks, a primary method for botnet monetization.
Botnet adds as many device types as possible
From the beginning, Hide and Seek was clear that it did not care about the type of devices it infected. It began by targeting IP cameras and then extended to DVRs, NVRs and IPTV boxes. Now Android devices are in its sight, too.
Its developers compiled binaries for multiple architectures, including MIPS, ARM, Motorola 68020, SuperH, PowerPC, x86, and x64. They also developed a custom P2P mechanism to communicate with other infected systems.
Furthermore, the malware also added persistence capabilities, which would enable it to survive reboots on an infected router.
The infection vectors Hide and Seek uses now include telnet scanning and brute-forcing, exploiting a vulnerability in AVTECH IP Camera, NVR and DVR; exploiting a vulnerability in Wansview NCS601W camera, and scannin
To read the original article:
