Even after many efforts made by Google last year, malicious apps always somehow manage to make their ways into Google app store.
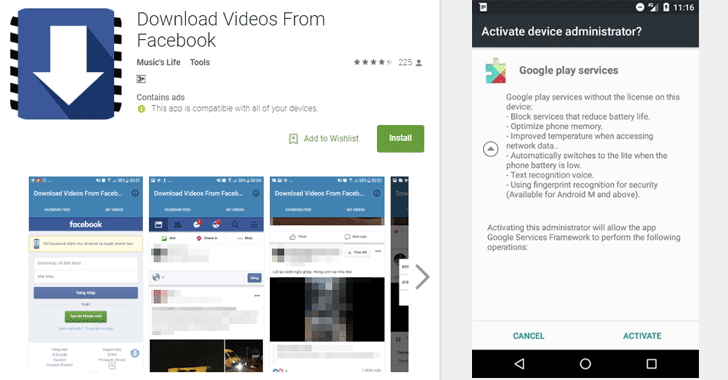
Security researchers have now discovered a new piece of malware, dubbed GhostTeam, in at least 56 applications on Google Play Store that is designed to steal Facebook login credentials and aggressively display pop-up advertisements to users.
Discovered independently by two cybersecurity firms, Trend Micro and Avast, the malicious apps disguise as various utility (such as the flashlight, QR code scanner, and compass), performance-boosting (like file-transfer and cleaner), entertainment, lifestyle and video downloader apps.
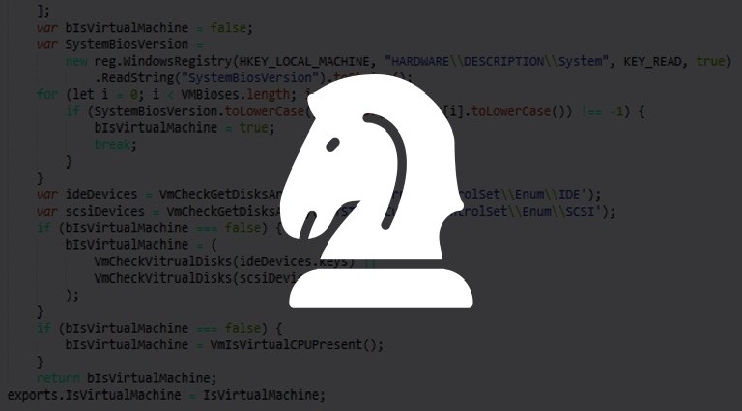
Once installed, it first confirms if the device is not an emulator or a virtual environment and then accordingly downloads the malware payload, which prompts the victim to approve device administrator permissions to gain persistence on the device.
« The downloader app collects information about the device, such as unique device ID, location, language and display parameters, » Avast said. « The device’s location is obtained from the IP address that is used when contacting online services that offer geolocation information for IPs. »
How Android Malware Steals Your Facebook Account Password
As soon as users open their Facebook app, the malware immediately prompts them to re-verify their account by logging into Facebook. Instead of exploiting any system or application vulnerabilities, the malware uses a classic phishing scheme in order to get the job done.
These fake apps simply launch a WebView component with Facebook look-alike login page and ask users to log-in. Apparently, WebView code steals the victim’s Facebook username and password and sends them to a remote hacker-controlled server.
« This is most likely due to developers using embedded web browsers (WebView, WebChromeClient) in their apps, instead of opening the webpage in a browser, » Avast said.
Trend Micro researchers warn that these stolen Facebook credentials can later be repurposed to deliver « far more damaging malware » or « amass a zombie social media army » to spread fake news or generate cryptocurrency-mining malware.
To read the original article: