A new report by the CyberEdge Group found that 55 percent of responding organizations were compromised by ransomware in 2017, down from 61 percent in 2016. How victims responded to ransomware Respondents who were victimized by ransomware and who elected to pay the ransoms were asked if they successfully recovered […]
Hacking
Fake resume malspam delivers Sigma Ransomware
I haven’t seen any examples of this Resume malware for a while now, so when this popped up in my spam folder, it looked interesting enough to investigate a bit more. This is a continuation from these 4 previous posts about malware using resumes or job applications as the lure. They […]
Une nouvelle tentative de phishing qui usurpe les mails d’OVH
Attention, une nouvelle campagne de phishing vise les détenteurs de comptes OVH . Elle joue sur la peur et indique que votre compte sera suspendu et qu’il faut « ‘effectuer le règlement par carte bancaire à l’ordre d’OVH » ! OVH est l’un des plus grands hébergeurs web du net. Il […]
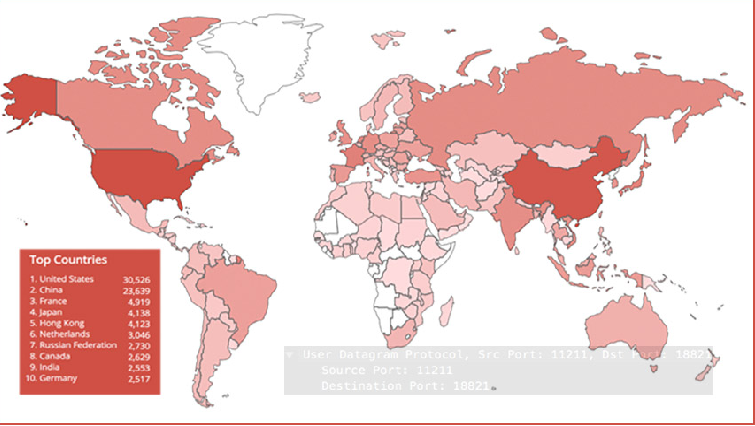
NRA Websites Heavily Targeted by Memcached-Based DDoS Attacks
Websites associated with the US National Rifle Association (NRA) have often been the targets of Memcached-based DDoS attacks, according to Qihoo 360’s Network Security Research Laboratory (Netlab). The Chinese company, who has one of the widest views of all Internet traffic due to its leading position on the Chinese market, […]
CVE-2018-6789 Exim Flaw Expose 400,000 Serveurs de messagerie
Une faille dans un programme de messagerie largement utilisé qui peut exposerons quelques-uns 400,000 serveurs à l’échelle mondiale a été découvert par des chercheurs de sécurité. La vulnérabilité, qui a été identifié comme CVE-2018-6789 réside dans toutes les versions de l’agent de transfert de messages Exim (plus spécifiquement en fonction […]
Memcached DDoS Attacks: 95,000 Servers Vulnerable to Abuse
More than 95,000 servers could still be vulnerable to being abused to launch massive distributed denial-of-service attacks. The risk comes via Memcached, an open source utility designed to cache in RAM frequently used web pages. The web page caching utility was never designed to be internet-accessible and requires no authentication to […]
Hidden Cobra Targets Turkish Financial Sector With New Bankshot Implant
On February 28, the McAfee Advanced Threat Research team discovered that the cybercrime group Hidden Cobra continues to target cryptocurrency and financial organizations. In this analysis, we observed the return of Hidden Cobra’s Bankshot malware implant surfacing in the Turkish financial system. Based on the code similarity, the victim’s business […]
North Korea Suspected in Cyberattack on Turkey
SEOUL—Suspected North Korean hackers blitzed Turkish financial institutions and a government organization last week, seeking intelligence for a future heist, a new report says. The attacks on March 2 and 3, identified by cyber researcher McAfee LLC in a Thursday report, attempted to lure targets with faux links to a popular cryptocurrency […]
Multiples vulnérabilités dans Juniper Junos OS
De multiples vulnérabilités ont été découvertes dans Juniper Junos OS. Elles permettent à un attaquant de provoquer un déni de service à distance, un contournement de la politique de sécurité et une élévation de privilèges. RISQUE(S) Déni de service à distance Contournement de la politique de sécurité Élévation de privilèges […]
The state of Mac malware
Mac users are often told that they don’t need antivirus software, because there are no Mac viruses. However, this is not true at all, as Macs actually are affected by malware, and have been for most of their existence. Even the first well-known virus—Elk Cloner—affected Apple computers rather than MS-DOS […]