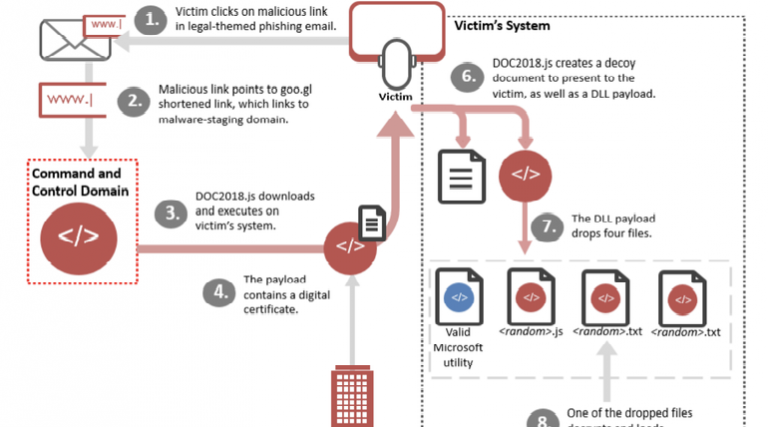
Advanced persistent threat group (APT) the Cobalt Gang, also known as Gold Kingswood, is spreading SpicyOmelette malware in campaigns targeting financial institutions worldwide. In a world where cyberattacks against businesses and consumers alike are spreading and evolving in nature and sophistication, it is often financial institutions which bear the brunt. […]
Hacking
FBI warns companies about hackers increasingly abusing RDP connections
In a public service announcement published today by the US Federal Bureau of Investigation’s (FBI) Internet Crime Complaint Center (IC3), the FBI is warning companies about the dangers of leaving RDP endpoints exposed online. RDP stands for the Remote Desktop Protocol, a proprietary technology developed by Microsoft in the 90s […]
LoJax: First UEFI rootkit found in the wild, courtesy of the Sednit group
UEFI rootkits are widely viewed as extremely dangerous tools for implementing cyberattacks, as they are hard to detect and able to survive security measures such as operating system reinstallation and even a hard disk replacement. Some UEFI rootkits have been presented as proofs of concept; some are known to be […]
LA FAILLE DE SÉCURITÉ WD MY CLOUD OFFRE AUX PIRATES UN ACCÈS COMPLET
Pourquoi c’est important: la question de la confidentialité et de la sécurité des données se répercute chaque fois qu’un fournisseur de matériel refuse de reconnaître ou de prendre connaissance des exploits qui compromettent les données de ses clients. Bien que les données des clients soient exposées, personne ne se soucie de […]
VPNFilter Malware Adds Seven New Tools For Exploiting Network Devices
The VPNFilter malware is a globally deployed threat infected thousands of network devices across the globe, it is a multi-stage, modular platform with versatile capabilities to support both intelligence-collection and destructive cyber attack operations. It was uncovered by Talos researchers, the malware infects more than 500,000 in at least 54 […]
Uber to Pay $148 Million as a Settlement for Data Breach Cover
Uber Agreed to Pay $148 Million as a Settlement for 2016 Uber data breach which impacts 57 million Uber users around the world and 600,000 drivers names including their license numbers were stolen. The breach took place in October 2016 and the leaked data includes names, email addresses and mobile phone numbers […]
LA NOUVELLE FAILLE DE SÉCURITÉ LINUX ‘MUTAGEN ASTRONOMY’ AFFECTE LES DISTRIBUTIONS RED HAT ET CENTOS
ne entreprise de cyber-sécurité a publié des détails et un code de preuve de concept (PoC) sur une vulnérabilité du noyau Linux qui n’a d’impact que sur les distributions CentOS et Red Hat Enterprise Linux (RHEL). Le nom de vulnérabilité est Mutagen Astronomy et est suivi par CVE-2018-14634. Découvert par l’équipe […]
New Linux Kernel Bug Affects Red Hat, CentOS, and Debian Distributions
Security researchers have published the details and proof-of-concept (PoC) exploits of an integer overflow vulnerability in the Linux kernel that could allow an unprivileged user to gain superuser access to the targeted system. The vulnerability, discovered by cloud-based security and compliance solutions provider Qualys, which has been dubbed « Mutagen Astronomy, » […]
Hide and Seek Botnet Adds Infection Vector for Android Devices
Since its discovery early this year, the Hide and Seek IoT botnet has been increasing its infection capabilities with new vectors. The latest samples look for Android devices with the wireless debugging feature enabled. While IoT botnets appear and go away on a daily basis, Hide and Seek first attracted attention […]
Banking Trojan found on Google Play stole 10,000 Euros from victims
Recently was discovered Android banking Trojan available on Google Play with more than 10,000 installs. This infiltration was capable of luring user’s banking credentials and send them to the attacker. Trojan was also capable of bypassing SMS two factor authentication. Based on analysis, app targeted German, Polish and Czech banks. […]