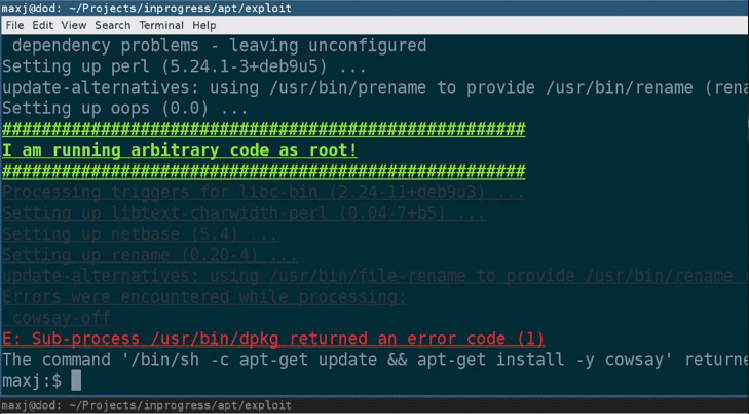
Some cybersecurity experts this week arguing over Twitter in favor of not using HTTPS and suggesting software developers to only rely on signature-based package verification, just because APT on Linux also does the same. Ironically, a security researcher just today revealed details of a new critical remote code execution flaw in the apt-get utility that […]
Hacking
A flaw in MySQL could allow rogue servers to steal files from clients
A rogue MySQL server could be used to steal files from clients due to a design flaw in the popular an open source relational database management system (RDBMS). The flaw resides in the file transfer process between a client host and a MySQL server, it could be exploited by an attacker running a […]
Unpatched Cisco critical flaw CVE-2018-15439 exposes small Business Networks to hack
Unpatched critical flaw CVE-2018-15439 could be exploited by a remote, unauthenticated attacker to gain full control over the device. Cisco Small Business Switch software is affected by a critical and unpatched vulnerability (CVE-2018-15439) that could be exploited by a remote, unauthenticated attacker to gain full control over the device. Cisco Small Business Switch SOHO devices allow […]
Attacks in the wild leverage flaw in ThinkPHP Framework
Threat actors in the wild are leveraging a recently discovered flaw in the ThinkPHP PHP framework to install cryptominers, skimmers, and other malware. Multiple threat actors are leveraging a recently discovered code execution vulnerability (CVE-2018-20062) in the ThinkPHP framework. The flaw was already addressed by the Chinese firm TopThink that designed the framework, but security expert […]
Hackers infect e-commerce sites by compromising their advertising partner
Magecart strikes again, one of the most notorious hacking groups specializes in stealing credit card details from poorly-secured e-commerce websites. According to security researchers from RiskIQ and Trend Micro, cybercriminals of a new subgroup of Magecart, labeled as « Magecart Group 12, » recently successfully compromised nearly 277 e-commerce websites by using […]
Ukrainian Police Arrest 6 Hackers Linked to DDoS and Financial Attacks
Ukrainian Police have this week busted out two separate groups of hackers involved in carrying out DDoS attacks against news agencies and stealing money from Ukrainian citizens, respectively. According to the authorities, the four suspected hackers they arrested last week, all aged from 26 to 30 years, stole more than 5 […]
CISCO addresses DoS bugs in CISCO ESA products
Cisco addressed two DoS vulnerabilities in CISCO ESA products that can be exploited by remote unauthenticated attacker. Cisco fixed two denial-of-service (DoS) flaws in Email Security Appliance (ESA) products that can be exploited by a remote unauthenticated attacker. The first flaw tracked as CVE-2018-15453 has been rated as “critical,” it is a memory corruption […]
New Systemd Privilege Escalation Flaws Affect Most Linux Distributions
Security researchers have discovered three vulnerabilities in Systemd, a popular init system and service manager for most Linux operating systems, that could allow unprivileged local attackers or malicious programs to gain root access on the targeted systems. The vulnerabilities, assigned as CVE-2018-16864, CVE-2018-16865, and CVE-2018-16866, actually resides in the « systemd-journald » […]
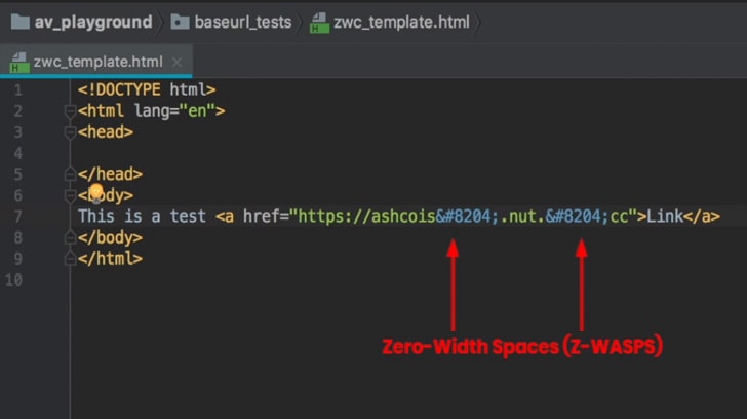
Hackers Using Zero-Width Spaces to Bypass MS Office 365 Protection
Security researchers have been warning about a simple technique that cybercriminals and email scammers are already being using in the wild to bypass security features of Microsoft Office 365, including Safe Links, which are originally designed to protect users from malware and phishing attacks. Safe Links has been included by […]
PyLocky Ransomware Decryption Tool Released — Unlock Files For Free
If your computer has been infected with PyLocky Ransomware and you are searching for a free ransomware decryption tool to unlock or decrypt your files—your search might end here. Security researcher Mike Bautista at Cisco’s Talos cyber intelligence unit have released a free decryption tool that makes it possible for victims infected with […]