xperts at Akamai have identified a running Fast Flux botnet composed of over 14,000 compromised systems used to spread malware. Experts at Akamai have identified a running botnet of over 14,000 compromised systems used to spread malware. The botmasters implemented a technique dubbed Fast Flux to make the infrastructure hard […]
Cybersecurity
DDoS attacks: Brands have plenty to lose, even if attacked only once
DDoS attacks continue to be an effective means to distract and confuse security teams while inflicting serious damage on brands. Neustar discovered that brands experienced a 27 percent increase in the number of breaches per DDoS attack, despite suffering similar attack levels in the same time period last year. Attackers […]
Cyber Threat Intelligence – Minority Report
Threat intelligence (TI) is at the maturity level to become a decision making tool. TI refers to evidence based information including context such as mechanisms, Indicators of Compromise (IOC), Indicators of Attribution (IOA), implications and actionable advice about existing or emerging hazards to assets. TI allows the technical staff professionals […]
4G/5G Wireless Networks as Vulnerable as WiFi and putting SmartCities at Risk
Researchers from security firm Positive Technologies warns of 4G/5G Wireless Networks as vulnerable as WiFi and putting smart-cities at risk The Internet of Things (IoT) presents many new opportunities and some different challenges. The vast number of devices makes it very expensive to connect everything with traditional network cabling and […]
ATMii Malware can make ATMs drain available cash
Security researchers from Kaspersky have detected a new ATM malware called ATMii that targets only ATMs operating on Microsoft Windows 7 and Windows Vista. The malware was first detected in April 2017 when one of the affected banks shared the malware with Kaspersky security researchers. The malware consists of two […]
MICROSOFT PATCHES CRITICAL WINDOWS DNS CLIENT VULNERABILITIES
Three critical Windows DNS client vulnerabilities were patched today by Microsoft, closing off an avenue where an attacker could relatively simply respond to DNS queries with malicious code and gain arbitrary code execution on Windows clients or Windows Server installations. The flaws were discovered and privately disclosed to Microsoft by […]
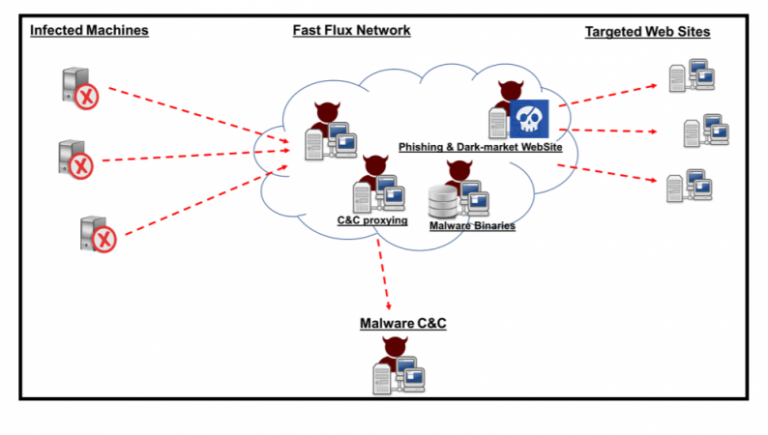
Investigation reveals large botnet hiding behind Fast Flux technique
Fast Flux, a DNS technique first introduced in 2006 and widely associated with the Storm Worm malware variants, can be used by botnets to hide various types of malicious activities – including phishing, web proxying, malware delivery, and malware communication. The technique allows the botnet to “hide” behind an ever-changing […]
INSIDE THE CCLEANER BACKDOOR ATTACK
MADRID—As the investigation continues into the backdoor planted inside CCleaner, two members of parent company Avast’s threat intelligence team said today the desktop and cloud versions of the popular software contained different payloads. The revelation was made during a talk at Virus Bulletin 2017 during which Jakub Kroustek and Jiri […]
SAP vulnerabilities can take servers offline
Eight vulnerabilities have been found in SAP products which can lead not only to information leaks, but also the possibility of taking entire servers offline. On Wednesday, security researchers from Positive Technologies said the bugs were found in a variety of SAP solutions, including the Web Dynpro Island development — […]
NETGEAR FIXES 50 VULNERABILITIES IN ROUTERS, SWITCHES, NAS DEVICES
Netgear recently issued 50 patches for its routers, switches, NAS devices, and wireless access points to resolve vulnerabilities ranging from remote code execution bugs to authentication bypass flaws. Twenty of the patches address “high” vulnerability issues with the remaining 30 scored as “medium” security risks. Netgear posted advisories for the […]