Le FBI avertit que les cybercriminels préparent un piratage de masse contre les guichets automatiques bancaires Les chefs des services de renseignement américains ont averti les banques qu’une menace de piratage importante pesait sur les distributeurs de billets dans le monde entier au cours des prochains jours. Le FBI a […]
Haythem Elmir
Experts published a PoC code for Intel Management Engine JTAG flaw
A group of security researchers has published a proof-of-concept exploit code for a vulnerability in the Intel Management Engine JTAG. A team of security researchers has published a proof-of-concept exploit code for a vulnerability in the Intel Management Engine JTAG. Last year the same group of experts at Positive Technologies discovered an undocumented configuration […]
Mobile’s Latest Malware Threat: The All-in-One Android Trojan
A new Android Trojan — dubbed Android.Banker.L — combines the functionality of banking Trojans, keyloggers and ransomware to compromise victim devices and steal data. As reported by Quick Heal, the latest malware threat uses multiple methods simultaneously to attack user devices. In addition to a typical Android banking Trojan, the […]
Windows 10 est vulnérable, une faille Zero-day est divulguée publiquement
Surgit de nul part, une publication sur Twitter dévoile l’existence d’une faille Zero day affectant Windows 10. Les utilisateurs de ce système d’exploitation sont désormais vulnérables. Aucun correctif n’est disponible, Microsoft a été pris au dépourvu. Cette faille a été dévoilée au travers d’un simple tweet. La vulnérabilité concerne le […]
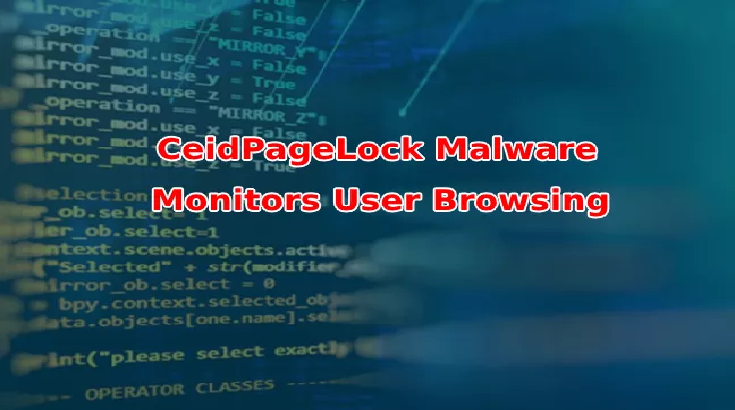
CeidPageLock Malware that Monitors User’s Browsing Data and Redirects Fake Pages
CeidPageLock RootKit evolves again with more improved features, this times it has been distributed by the RIG Exploit kit. The latest version contains functionalities such as monitoring user browsing activities, replace websites with fake pages and ability to redirect victims to fake pages. The CeidPageLock is a browser hijacker which […]
Novel Attack Technique Uses Smart Light Bulbs to Steal Data
Researchers have determined that some light bulbs are suitable for covert data exfiltration from personal devices, and can leak multimedia preferences by recording their luminance patterns from afar. For the light sources to become an attack surface, they need to meet some requirements such as support for multimedia visualizations and […]
A New Ransomware Attack Posed as Windows Activator Emerging in Wild With Hidden Functions
A new ransomware distributed by attackers posing as a Windows Activator appearing to be distributed through external network drives. The ransomware found to be active from August 7th and spreading since then. Researchers from 360totalsecurity spotted the ransomware contains hidden configuration function and the information used for encryption. Once the ransomware execution […]
Iran-linked COBALT DICKENS group targets universities in new phishing campaign
Experts from SecureWorks discovered a large phishing campaign targeting universities carried out by an Iran-linked threat actor COBALT DICKENS. Security firm SecureWorks has uncovered a new phishing campaign carried out by COBALT DICKENS APT targeting universities worldwide, it involved sixteen domains hosting more than 300 spoofed websites for 76 universities in 14 countries, […]
Andromeda Botnet Operator Released With a Slap on the Wrist
Sergey Yarets, also known as Ar3s, a hacker arrested last year for running an instance of the Andromeda botnet, was released by Belarusian authorities with nothing more than a slap on the wrist. Authorities dropped all charged after Yarets cooperated with investigators, and after he handed over all the profits […]
Experts warn of possible attacks after PoC code for CVE-2018-11776 Struts flaw was published
The Exploit code for the recently discovered Critical remote code execution vulnerability CVE-2018-11776 in Apache Struts 2 was published on GitHub, experts fear massive attacks. The CVE-2018-11776 vulnerability affects Struts 2.3 through 2.3.34, Struts 2.5 through 2.5.16, and potentially unsupported versions of the popular Java framework. “Possible Remote Code Execution when using results with […]