Researchers have determined that some light bulbs are suitable for covert data exfiltration from personal devices, and can leak multimedia preferences by recording their luminance patterns from afar.
For the light sources to become an attack surface, they need to meet some requirements such as support for multimedia visualizations and infrared capabilities.
The adversary does not need to attack the internal network of the victim to extract the information. They only need a direct connection between the target device and the lights, and line-of-sight with bulbs during the exfiltration process.
Deducing victim’s music and video tastes
Anindya Maiti and Murtuza Jadliwala from the University of Texas at San Antonio studied how LIFX and Philips Hue bulbs receive their commands for playing visualizations into a room and developed a model to interpret brightness and color modulations occurring when listening to music or watching a video.
During audio-visualization, the brightness level reflects the source sound, while in the case of video visualizations, the modifications reflect the dominant color and brightness level in the current video frame. The associated mobile app controls the oscillations by sending specially formatted packets to the light bulbs.
The model created by the two researchers requires the adversary to create a database of light patterns, like a dictionary for songs and videos, they can use as a reference for the profile captured from the target.

Data exfiltration from personal devices
Extracting information from a personal device is possible under certain conditions. The simple observation of the light pattern is not sufficient in this case.
Light bulbs need to support infrared lighting and should not require authorization for controlling them over the local network. Moreover, the adversary needs to plant malware that encodes private data from the target device and sends it to the smart light bulbs.
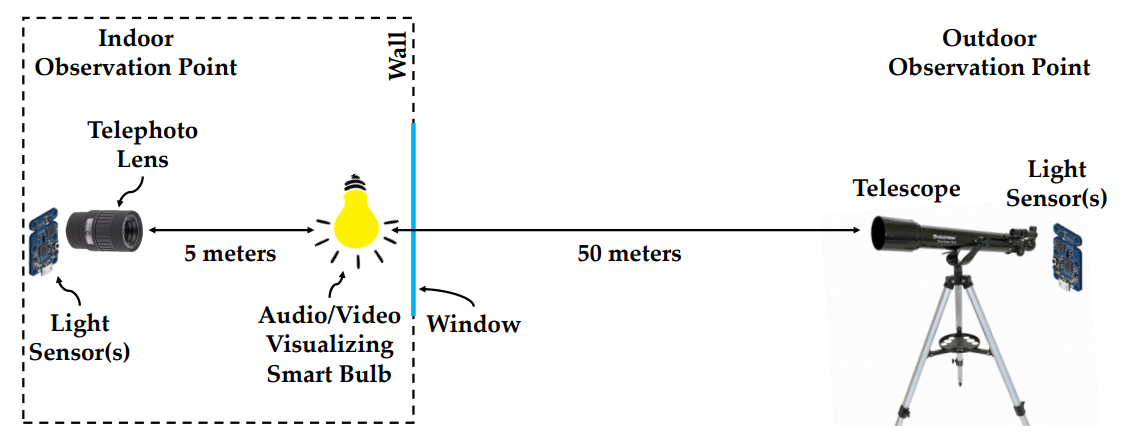
The researchers used two observation points to capture the data: indoor and outdoor. Predictable enough, indoor observation recorded the most accurate results and longer exposure yielded a better outcome.
From a sample set of 100, « 51 songs were correctly predicted in the top rank, while genres of 82 songs were correct in the same prediction, » the researchers reveal about audio inference results.
Data exfiltration was possible through transmission techniques like such as amplitude and/or wavelength shift keying, using both the visible and the infrared spectrum of the smart bulbs (LIFX) were used.
To test the infrared data exfiltration method, the researcher chose to encode a picture at the source and decode it at different distances up to 50 meters. At 5m, the extracted pic is highly intelligible and it degrades visibly as the data capture occurs at greater distances. However, even at 50m, one can discern the information.

The work of the two researchers is experimental, but it shows that using infrared light to steal meaningful information is possible from relatively large distances.
Defending against these attack methods is just a matter of making the light less visible to the outside. A curtain can do the trick. Choosing window glass that has low transmittance is also an adequate defense.
To read the original article