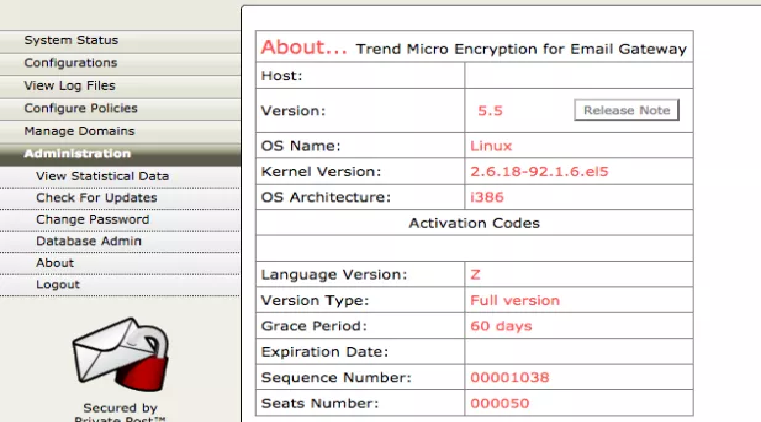
Security researchers at Core Security have discovered a dozen vulnerabilities in Trend Micro Linux-based Email Encryption Gateway. Security researchers at Core Security have discovered a dozen flaws in Trend Micro Linux-based Email Encryption Gateway, some of them have been rated as critical and high severity. The flaws received the CVE […]
Année : 2018
Avzhan DDoS bot dropped by Chinese drive-by attack
The Avzhan DDoS bot has been known since 2010, but recently we saw it in wild again, being dropped by a Chinese drive-by attack. In this post, we’ll take a deep dive into its functionality and compare the sample we captured with the one described in the past. Analyzed sample 05749f08ebd9762511c6da92481e87d8 – The […]
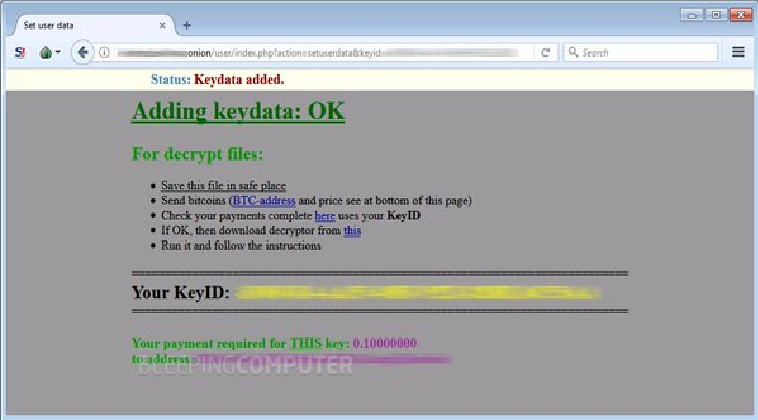
Data Keeper Ransomware Makes First Victims Two Days After Release on Dark Web RaaS
Two days after crooks started advertising the Data Keeper Ransomware-as-a-Service (RaaS) on the Dark Web, ransomware strains generated on this portal have already been spotted in the wild, infecting the computers of real-world users. Spotted earlier this week by Bleeping Computer, Data Keeper is the third ransomware strain offered as a […]
PSA: Improperly Secured Linux Servers Targeted with Chaos Backdoor
Hackers are using SSH brute-force attacks to take over Linux systems secured with weak passwords and are deploying a backdoor named Chaos. Attacks with this malware have been spotted since June, last year. They have been recently documented and broken down in a GoSecure report. Chaos rooted in 2013 sebd rootkit […]
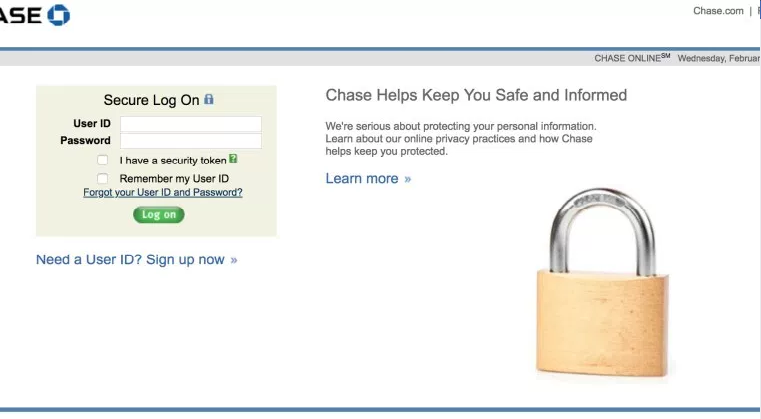
Banking Nightmare: Chase Glitch Gives Online Access to Random People
Have you ever wondered what would happen if hackers got into your bank account? What if YOUR BANK ITSELF let someone into your account? While hackers may be scary, the scarier prospect is your bank’s online system allowing access to random people. As of this afternoon, that’s actually what happened […]
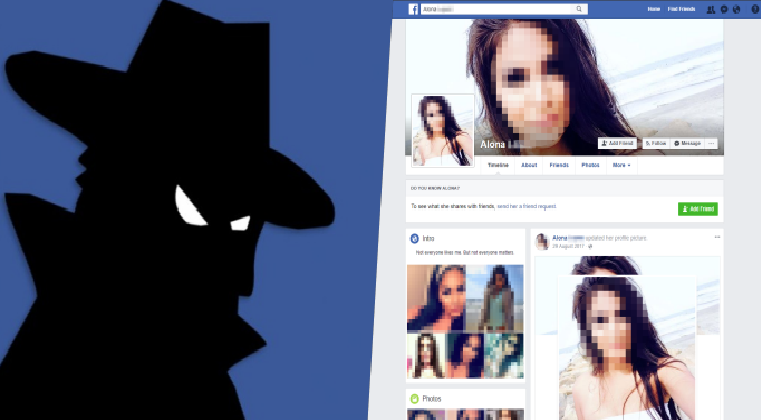
Hackers spread Android spyware through Facebook using Fake profiles
The Android spyware was used to steal personal data of victims – The campaign also shows why users should never use their real photos on Facebook. There are almost 2 billion monthly active users on the social media giant Facebook and that makes it one of the most lucrative targets for hackers […]
Des hackers peuvent infiltrer les comptes Tinder avec un simple numéro de téléphone
Votre vie sentimentale n’a peut-être tenu qu’à la bonne volonté d’un hacker pendant un moment. Un informaticien a dévoilé une faille importante sur Tinder. Elle a depuis été corrigée. Si on vous demandait le type d’applications que vous n’avez pas forcément envie de voir tomber entre les mains d’un pirate, […]
The Drupal development team addressed many vulnerabilities in both Drupal 8 and 7, including some flaws rated as “critical”.
Drupal maintainers have fixed many vulnerabilities in Drupal 7 and 8, including some flaws rated as “critical.” One of the critical security vulnerabilities is related to partial cross-site scripting (XSS) prevention mechanisms that was addressed with Drupal 8.4.5 and 7.57 versions. The popular CMS uses a JavaScript function that doesn’t completely sanitize the […]
SamSam Ransomware Hits Colorado DOT, Agency Shuts Down 2,000 Computers
The Colorado Department of Transportation (DOT) has shut down over 2,000 computers after some systems got infected with the SamSam ransomware on Wednesday, February 21. The agency’s IT staff is working with its antivirus provider McAfee to remediate affected workstations and safeguard other endpoints before before reintroducing PCs into its […]
Cisco Unity Connection Mail Relay Vulnerability
A vulnerability in the SMTP relay of Cisco Unity Connection could allow an unauthenticated, remote attacker to send unsolicited email messages. The vulnerability is due to improper handling of domain information in the affected software. An unauthenticated, remote attacker could exploit this vulnerability by sending crafted requests to the targeted […]