Hackers are using SSH brute-force attacks to take over Linux systems secured with weak passwords and are deploying a backdoor named Chaos.
Attacks with this malware have been spotted since June, last year. They have been recently documented and broken down in a GoSecure report.
Chaos rooted in 2013 sebd rootkit
According to GoSecure experts, the backdoor isn’t actually new and was one of the components of the « sebd » Linux rootkit that saw limited use in 2013 and was later dumped as a free download on HackForums.
It now appears that someone extracted the backdoor from the sebd rootkit source code, has renamed it to « Chaos, » and is now using it as the first-stage payload in attacks on Linux servers.
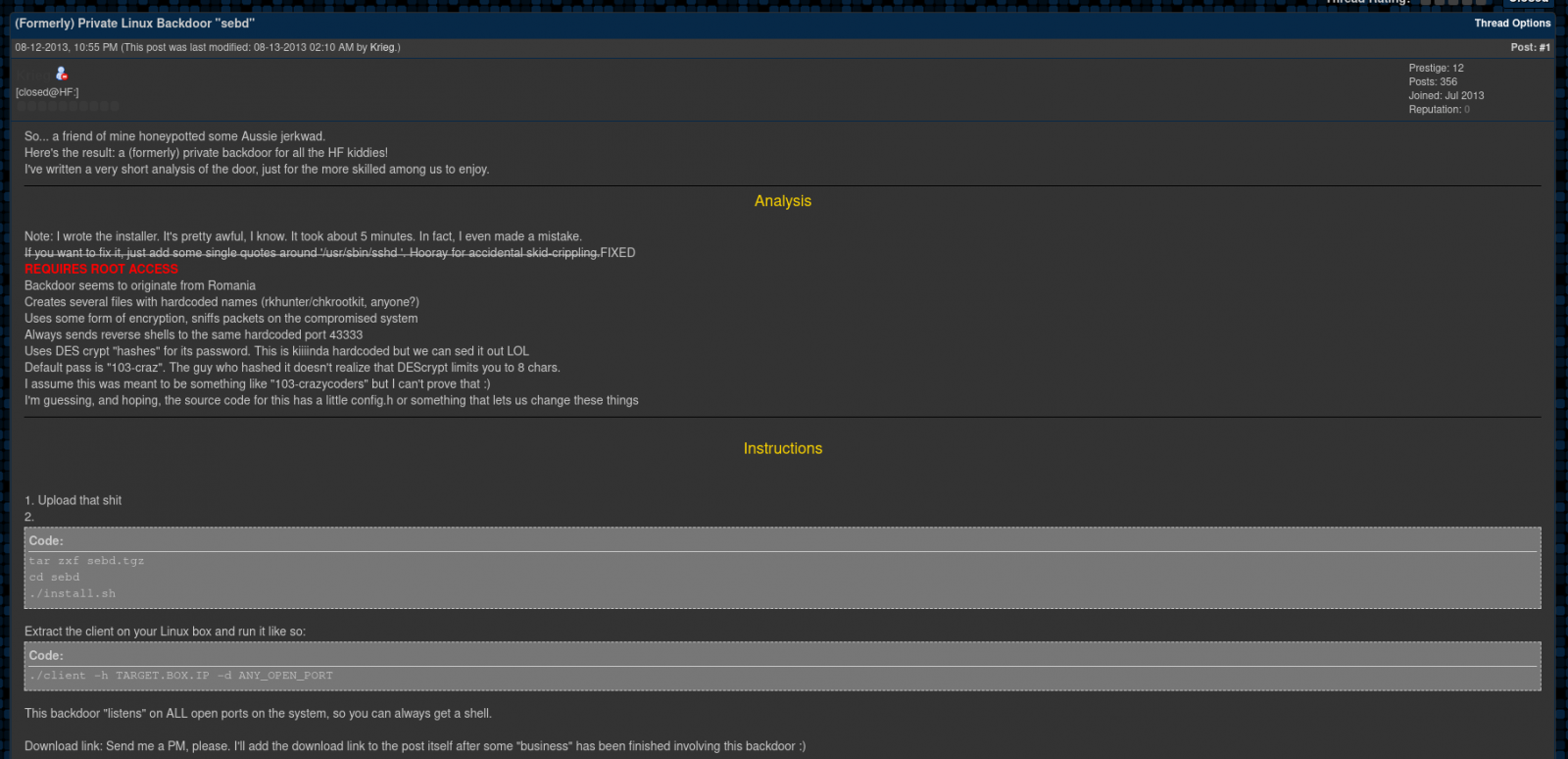
In the attacks spotted by GoSecure, hackers used Chaos to later dump a bot that ensnares the compromised Linux box into a botnet controlled via the IRC protocol.
The backdoor itself isn’t actually that advanced, nor does it utilize any new vulnerabilities. Linux guru and ZDnet reporter Steven J. Vaughan-Nichols was the first to point out earlier this week that the backdoor doesn’t actually rely on any exploits but only the stupidity of server admins who can’t set a strong password for their servers to save their lives.
Chaos uses clever trick to avoid firewalls
The only thing that stands out as interesting in Chaos’ modus operandi is the fact that it opens a raw socket on port 8338 on which it listens to commands.
« Any decent firewall would block incoming packets to any ports that have not explicitly been opened for operational purposes, » GoSecure experts say. « However, with Chaos using a raw socket, the backdoor can be triggered on ports running an existing legitimate service. »
Besides allowing Chaos to run without disturbing services already running on that port, this raw sockets trick also ensures that the backdoor’s process doesn’t appear when server admins run basic netstat -wchecks.
« Because Chaos doesn’t come alone but with at least one IRC Bot that has remote code execution capabilities, we advise infected hosts to be fully reinstalled from a trusted backup with a fresh set of credentials, » GoSecure advises.
To read the original article: