Two days after crooks started advertising the Data Keeper Ransomware-as-a-Service (RaaS) on the Dark Web, ransomware strains generated on this portal have already been spotted in the wild, infecting the computers of real-world users.
Spotted earlier this week by Bleeping Computer, Data Keeper is the third ransomware strain offered as a RaaS offering this year, after Saturn and GandCrab.
Another RaaS opens its gates for everybody
The service launched on February 12 but didn’t actually come online until February 20, and by February 22, security researchers were already reporting seeing the first victims complaining of getting infected.
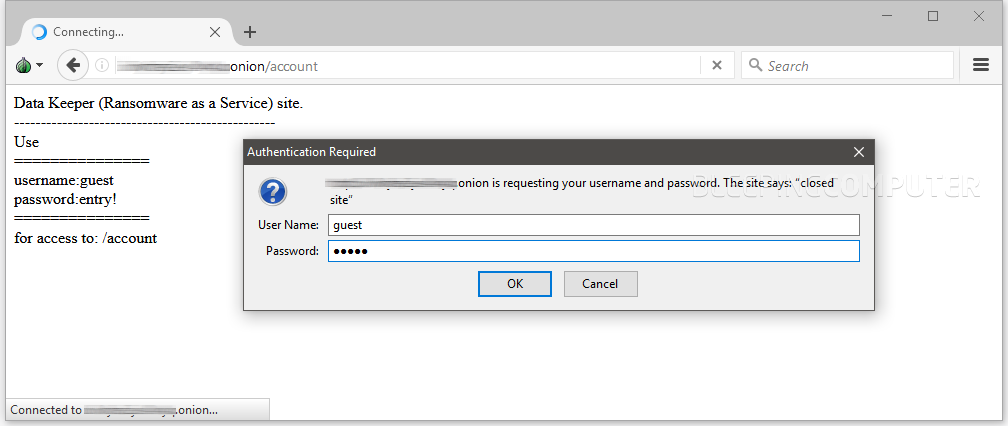
Just like the Saturn RaaS, Data Keeper lets anyone sign up for the service and lets them generate weaponized binaries right away, without having to pay a fee to activate an account.
Data Keeper maintainers are encouraging users to generate ransomware samples and distribute them to victims, with the promise of receiving a share of the ransom fee in case victims pay to decrypt their files. But while the Saturn crew made their commission known upfront (30% of the total ransom fee), the Data Keeper crew doesn’t disclose the amount of Bitcoin they keep from affiliates.
 |
 |
 |
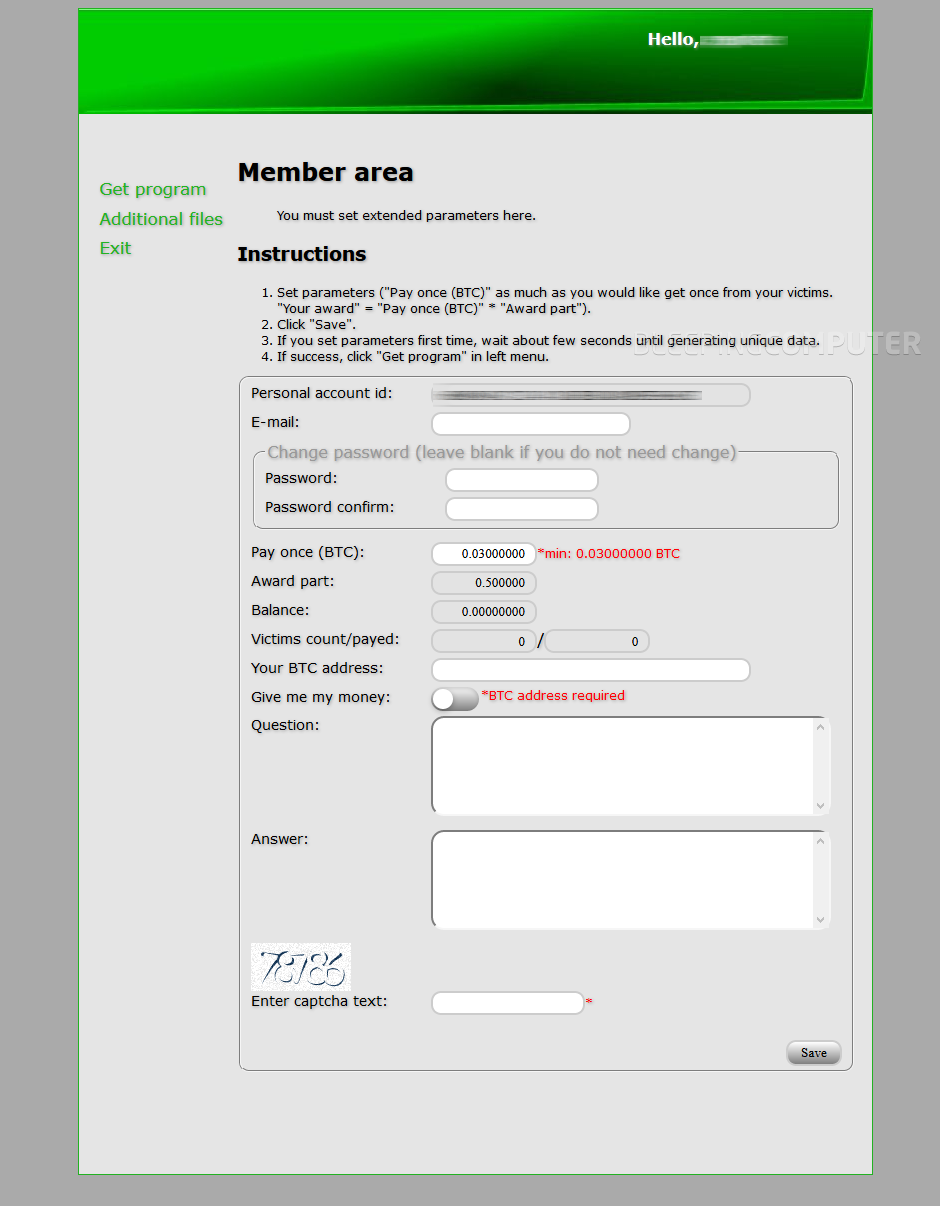
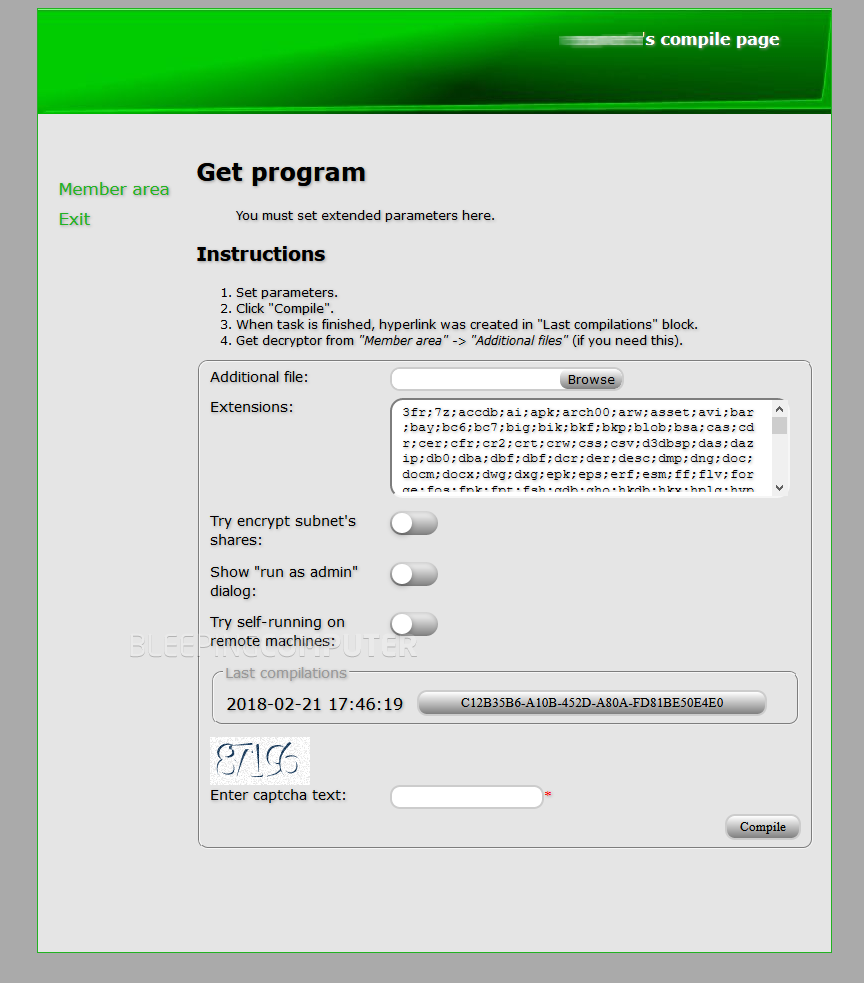
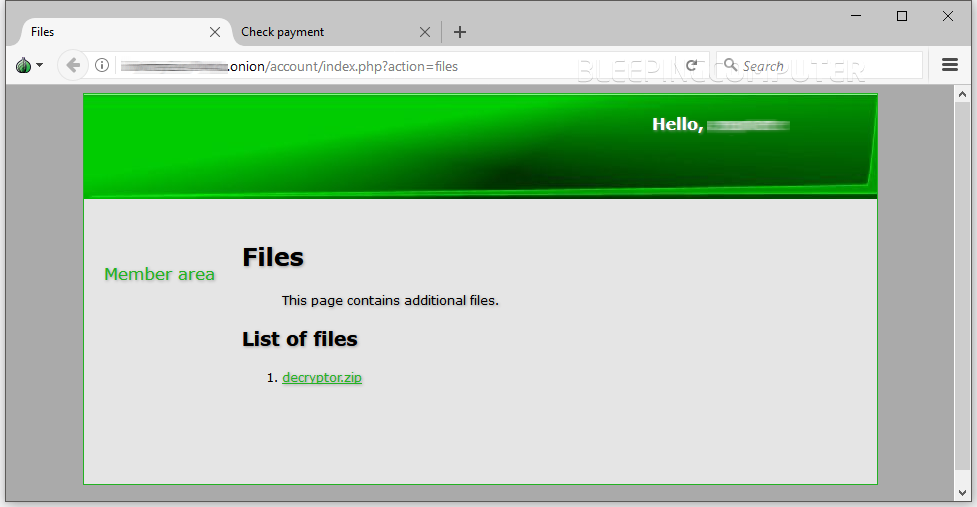
Sections are available in the Data Keeper RaaS backend that allow users to enter their Bitcoin wallet where to receive their « earnings, » sections where they can generate the ransomware’s encryptor binary, and a section from where they can download various files, including a sample decrypter.
 |
 |
 |
Data Keeper ransomware looks well-coded
The ransomware generated via the Data Keeper RaaS is coded in .NET, and while .NET ransomware is usually considered the bottom of the barrel regarding ransomware quality, this one appears to be written by someone more adept than the usual mob of .NET malware noobs.
« The in the wild [Data Keeper ransomware] sample we saw on Thursday consists of 4 layers, » said MalwareHunter, a security researcher who helped Bleeping Computer analyze the ransomware for this article.
« The first layer is an EXE that will drop another EXE to %LocalAppData% with a random name and a .bin extension. It then executes it with ProcessPriorityClass.BelowNormal and ProcessWindowStyle.Hidden parameters, » MalwareHunter says.
« That second EXE will load a DLL, which will load another DLL containing the actual ransomware that encrypts all the files. All layers have custom strings and resources protection, » he says. « And then each layer is protected with ConfuserEx. »
This is an unusual complex level of protection when compared to the troves of .NET ransomware that’s floated online in the past year.
Furthermore, this is also one of the few ransomware strains that uses PsExec, a command-line-based remote administration tool. DataKeeper uses PsExec to execute the ransomware on other machines on victims’ networks.
Data Keeper ransomware doesn’t use a special file extension
Victims infected with versions of this ransomware will have their files encrypted with a dual AES and RSA-4096 algorithm. Data Keeper also enumerates and tries to encrypt all networks shares it can get access to.
Data Keeper doesn’t add a special extension at the end of encrypted files, meaning victims won’t be able to tell what files are encrypted unless they try to open one. This is actually quite clever, as it introduces a sense of uncertainty for each victim, with users not knowing the amount of damage the ransomware has done to their PCs.
Further, the RaaS lets each affiliate select what file types to target, meaning different versions of Data Keeper will encrypt different files for each victim.
The only visible sign that victims have been infected is the « !!! ##### === ReadMe === ##### !!!.htm » file that Data Keeper places in each folder it encrypts files.
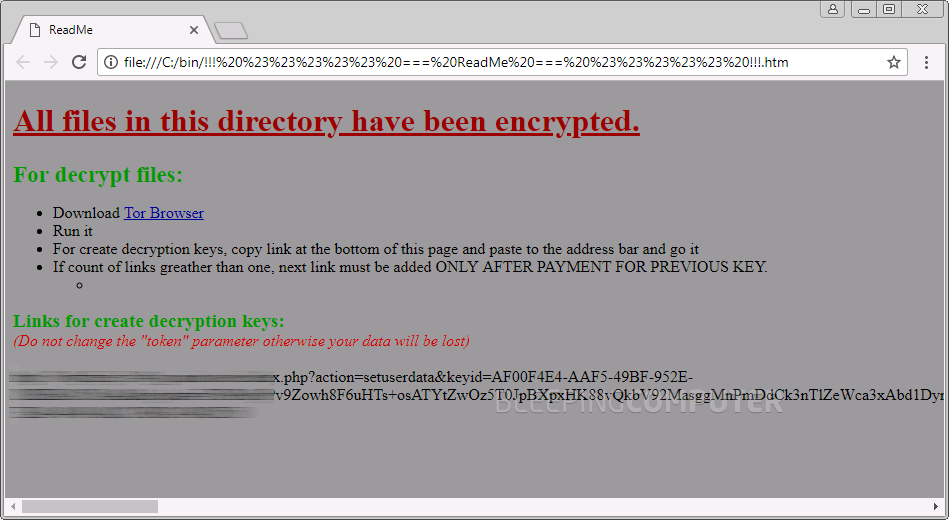
The ransom fee is also configurable in the RaaS, so this value also varies from victim to victim. Infected users are told to access a Dark Web URL for more information on the steps necessary to pay the ransom fee and receive a decrypter that will unlock their files.
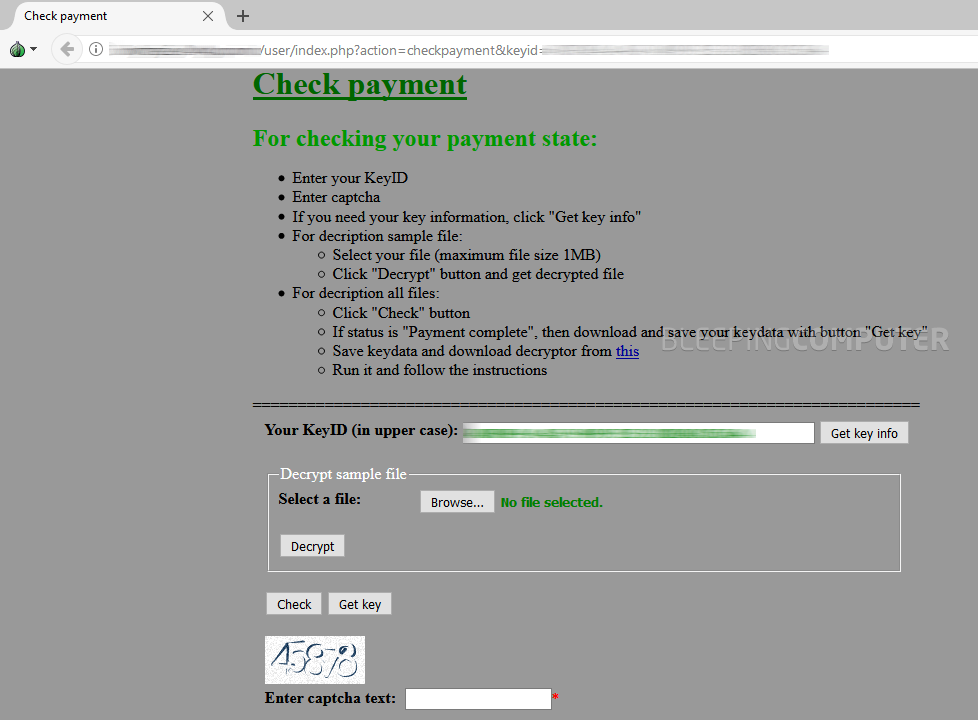
Based on the wording of the ransom note above, if Data Keeper infects a company’s computers, the victim will have to pay to unlock each computer at a time. This means a simple infection can reach staggering costs for some companies that did not have backups but want to recover their files.
Data Keeper ransomware versions spotted in the wild
At the time of writing, there appear to be multiple threat actors that have signed up for the RaaS, obtained weaponized binaries, and are now distributing Data Keeper to users.
MalwareHunter has told Bleeping Computer that one of the threat actors currently distributing a variant of the Data Keeper ransomware is hosting the malicious binaries on the server of a home automation system.
Crooks have also updated this particular ransomware binary from day to day, meaning they are fine-tuning their attacks, and are serious about their intentions and not carrying out just a simple test run.
Researchers who looked into Data Keeper’s encryption scheme for weaknesses were not able to find any bugs or mistakes they could exploit to recover victims’ files. If they find anything and create a free decrypter, we’ll update this article with a link to its download location.
to read the original article:
https://www.bleepingcomputer.com/news/security/data-keeper-ransomware-makes-first-victims-two-days-after-release-on-dark-web-raas/
