Blockchain, the technology that powers cryptocurrencies such as the volatile bitcoin, may provide credible solutions to financial institutions across the world Blockchain is being positioned as a cure for all banking ills. Photo: iStock Mumbai: Banking is necessary, but banks are not,” Bill Gates, co-founder of Microsoft Corp., had said over […]
Année : 2018
A flaw in Alpine Linux could allow executing arbitrary code
Security researcher Max Justicz has discovered several flaws in the distribution Alpine Linux, including an arbitrary code execution. Alpine Linux is an independent, non-commercial, general purpose Linux distribution that is heavily used in containers, including Docker. Alpine Linux is based on musl libc and busybox, it is a tiny distro and is […]
Cracked Windows installations are serially infected with EternalBlue exploit code
According to Avira, hundreds of thousands of unpatched Windows systems are serially infected with EternalBlue exploit code. The EternalBlue, is the alleged NSA exploit that made the headlines with DOUBLEPULSAR in the WannaCry attack. The malicious code was leaked online by the Shadow Brokers hacking group that stole it from the arsenal of the NSA-linked Equation Group. ETERNALBLUE targets the Server […]
Nine Major Phishing Attacks of 2018 (and How to Spot Them)
Phishing attacks are the most common type of cyberattack for good reason: because they work. If an attacker can convince you to click on a link in a phishing email and enter your credentials, it saves them a lot of trouble hacking into a network and cracking passwords. The details […]
HIDE AND SEEK Tracking NSO Group’s Pegasus Spyware to Operations in 45 Countries
In this post, we develop new Internet scanning techniques to identify 45 countries in which operators of NSO Group’s Pegasus spyware may be conducting operations. Key Findings Between August 2016 and August 2018, we scanned the Internet for servers associated with NSO Group’s Pegasus spyware. We found 1,091 IP addresses […]
Old WordPress Plugin Being Exploited in RCE Attacks
Old instances of the popular WordPress Duplicator Plugin are leaving sites open to remote code execution attacks. Researchers are warning that attackers are abusing a vulnerability in WordPress site admins’ outdated versions of a migration plugin called Duplicator – allowing them to execute remote code. Made by Snap Creek Software, all Duplicator plugins […]
Police in Europe Tie Card Fraud to People-Smuggling Gang
Two Syrians Accused of Buying Stolen Corporate Card Data to Mask Activities Coordinated police raids in Germany and Sweden have resulted in the arrest of two individuals suspected of running a cyber fraud gang that used stolen payment card data to book hundreds of airline and train tickets to help […]
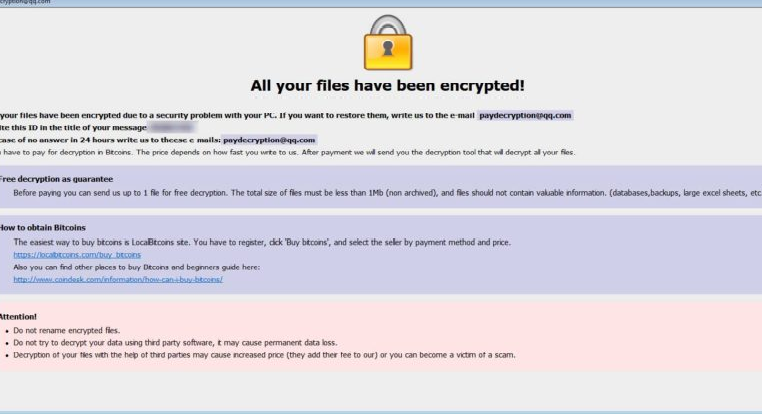
New Brrr Dharma Ransomware Variant Released
A new variant of the Dharma Ransomware was released this week that appends the .brrr extension to encrypted files. This variant was first discovered by Jakub Kroustek who tweeted a link to the sample on VirusTotal. Below I have outlined how this ransomware infects a computer, what happens when your files […]
New XBash malware combines features from ransomware, cryptocurrency miners, botnets, and worms
Palo Alto Network researchers discovered a new malware, tracked as XBash, that combines features from ransomware, cryptocurrency miners, botnets, and worms Security researchers at Palo Alto Networks have discovered a new piece of malware, dubbed XBash piece that is targeting both Linux and Microsoft Windows servers. Xbash was developed using Python, […]
LuckyMouse signs malicious NDISProxy driver with certificate of Chinese IT company
What happened? Since March 2018 we have discovered several infections where a previously unknown Trojan was injected into the lsass.exe system process memory. These implants were injected by the digitally signed 32- and 64-bit network filtering driver NDISProxy. Interestingly, this driver is signed with a digital certificate that belongs to […]