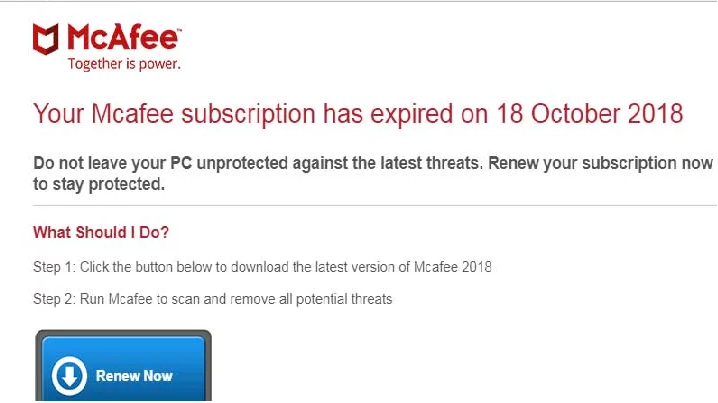
A new tech support scam pretending to be from McAfee was discovered last week that is harvesting credit card details and personal information of its victims. Last week I was tipped off about a new browser-based tech support scam that stated « Your Mcafee subscription has expired on 18 October 2018 ». […]
Année : 2018
IBM and banks back data project to fight human trafficking
Western Union, Barclays and Lloyds Banking Group are backing a new project that uses IBM’s Watson technology to tap into financial data to help track and combat human trafficking. Despite an increased awareness of human trafficking, efforts to manually track and counter the issue through legislation, preventative measures and enforcement, […]
Apple privacy portal lets you see everything it knows about you
A month after its most recent iPhone and Mac launches, Apple has refreshed its privacy pages. There isn’t much that’s changed: those pages still espouse Apple’s long-held commitment to privacy being a “fundamental human right” and that your information is, for the most part, kept on your iPhones, iPads and Macs. […]
Mozilla Brings Encrypted SNI to Firefox Nightly
Mozilla says Firefox Nightly now supports encrypting the Transport Layer Security (TLS) Server Name Indication (SNI) extension, several weeks after Cloudflare announced it turned on Encrypted SNI (ESNI) across all of its network. Introduced in 2003 to address the issue of accessing encrypted websites hosted at the same IP, the SNI extension […]
GreyEnergy cyberespionage group targets Poland and Ukraine
Security researchers from ESET published a detailed analysis of a recently discovered cyber espionage group tracked as GreyEnergy. Security experts from ESET published a detailed analysis of a recently discovered threat actor tracked as GreyEnergy, its activity emerged in concurrence with BlackEnergy operations. ESET researchers have spotted a new strain of malware […]
VestaCP compromis dans une nouvelle attaque de la chaîne de commande
Des consommateurs ont vu leurs informations d’accès Admin volés et leurs serveurs infectés par Linux/ChachaDDoS Au cours des derniers mois, de nombreux utilisateurs de VestaCP, une solution de panneau de contrôle d’hébergement, ont été avertis par leur fournisseur de services que leurs serveurs utilisaient une quantité anormale de bande passante. Nous […]
Attackers behind Operation Oceansalt reuse code from Chinese Comment Crew
Security researchers from McAfee have recently uncovered a cyber espionage campaign, tracked as Operation Oceansalt, targeting South Korea, the United States, and Canada. The threat actors behind Operation Oceansalt are reusing malware previously associated with China-linked cyberespionage group APT1. “McAfee Advanced Threat Research and Anti-Malware Operations teams have discovered another unknown data reconnaissance implant targeting Korean-speaking users.” reads […]
Tumblr Privacy Bug Could Have Exposed Sensitive Account Data
Tumblr stressed that there is no evidence the security bug was being abused or that unprotected account data was accessed. Tumblr on Wednesday disclosed it had fixed a vulnerability that could have exposed sensitive account information including usernames/passwords and individual IP addresses. However, the company stressed there’s no evidence that any […]
Chaining three critical vulnerabilities allows takeover of D-Link routers
Researchers from the Silesian University of Technology in Poland discovered several flaws that could be exploited to take over some D-Link routers. A group of researchers from the Silesian University of Technology in Poland has discovered three vulnerabilities in some models of D-Link routers that could be chained to take full […]
MartyMcFly Malware: new Cyber-Espionage Campaign targeting Italian Naval Industry
Yoroi security firm uncovered a targeted attack against one of the most important companies in the Italian Naval Industry leveraging MartyMcFly Malware. Today I’d like to share an interesting analysis of a Targeted Attack found and dissected by Yoroi (technical details are available here). The victim was one of the most important leaders in the field […]