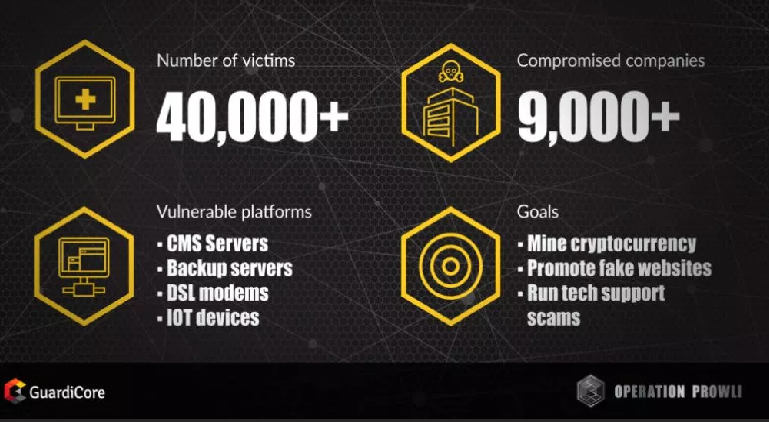
The VPNFilter malware that infected over 500,000 routers and NAS devices across 54 countries during the past few months is much worse than previously thought.
According to new research technical details published today by the Cisco Talos security team, the malware —which was initially thought to be able to infect devices from Linksys, MikroTik, Netgear, TP-Link, and QNAP— can also infect routers made by ASUS, D-Link, Huawei, Ubiquiti, UPVEL, and ZTE.
The list of devices vulnerable to VPNFilter has seen a sharp jump from Cisco’s original report, going from 16 device models to 71 —and possibly more. The full list is embedded at the bottom of this article.
New VPNFilter plugins
Furthermore, researchers have also discovered new VPNFilter capabilities, packed as third-stage plugins, as part of the malware’s tri-stage deployment system.
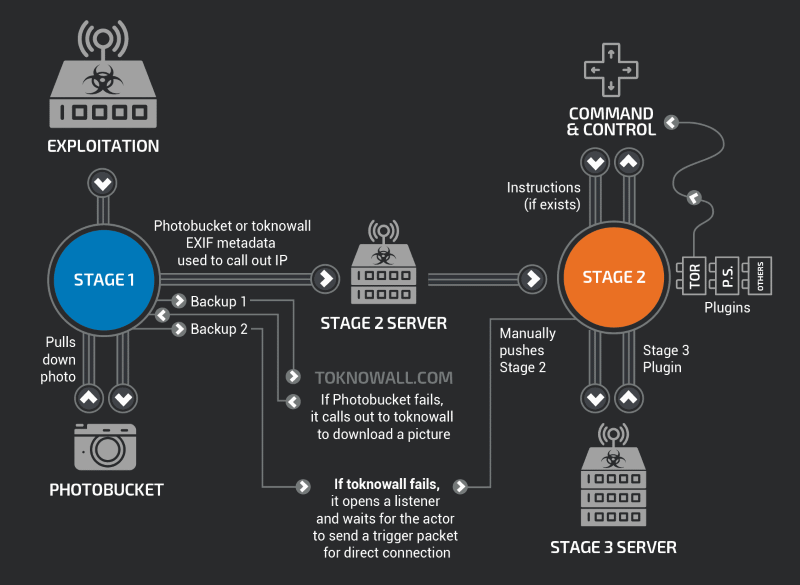
Cisco experts said they discovered the following two new third-stage plugins.
dstr – plugin to overwriting device firmware files. Cisco knew VPNFilter could wipe device firmware, but in its recent report pinpointed this function to this specific third-stage plugin.
These two new plugins add to the two already known.
tor – plugin used by VPNFilter bots to communicate with a command and control server via the Tor network.
Technical details about the VPNFilter malware, in general, are available in Cisco’s first report. Details about the ssler, dstr, and ps third-stage plugins are available in a report published today.
The VPNFilter botnet was found to have infected devices all over the world, but researchers have gone public with their findings when they detected the botnet preparing a cyber-attack on Ukraine’s IT infrastructure. Many believed the cyber-attack was supposed to take place on the day of the UEFA Champions League soccer final, which was held in Kiev, Ukraine, at the end of May.
The FBI intervened to neutralize the botnet by taking over its command and control server. Nevertheless, the group behind the malware, believed to be a unit of the Russian military, has recently begun assembling a new botnet, continuing to focus on infecting devices on Ukraine’s network.
Below is the updated list of routers and NAS devices targeted by the VPNFilter malware. Cisco said last month that VPNFilter does not use zero days to infect devices, meaning all the listed models are vulnerable via exploits against older firmware releases, and updating to the latest firmware version keeps devices out of the malware’s reach.
If users can’t update their router’s firmware, can’t update to a new router, but would still like to wipe the malware from their devices, instructions on how to safely remove the malware are available in this article. Removing VPNFilter from infected devices is quite a challenge, as this malware is one of two malware strains that can achieve boot persistence on SOHO routers and IoT devices. Furthermore, there are no visible signs that a router has been infected with this malware, so unless you can scan your router’s firmware, even knowing you’re infected is a challenge. The best advice we can give right now is to make sure you’re running a router with up-to-date firmware.
RT-AC66U (new)
RT-N10 (new)
RT-N10E (new)
RT-N10U (new)
RT-N56U (new)
RT-N66U (new)
D-Link Devices:
DES-1210-08P (new)
DIR-300 (new)
DIR-300A (new)
DSR-250N (new)
DSR-500N (new)
DSR-1000 (new)
DSR-1000N (new)
Huawei Devices:
HG8245 (new)
Linksys Devices:
E1200
E2500
E3000 (new)
E3200 (new)
E4200 (new)
RV082 (new)
WRVS4400N
Mikrotik Devices: (Bug Fixed in RouterOS version 6.38.5)
CCR1009 (new)
CCR1016
CCR1036
CCR1072
CRS109 (new)
CRS112 (new)
CRS125 (new)
RB411 (new)
RB450 (new)
RB750 (new)
RB911 (new)
RB921 (new)
RB941 (new)
RB951 (new)
RB952 (new)
RB960 (new)
RB962 (new)
RB1100 (new)
RB1200 (new)
RB2011 (new)
RB3011 (new)
RB Groove (new)
RB Omnitik (new)
STX5 (new)
Netgear Devices:
DG834 (new)
DGN1000 (new)
DGN2200
DGN3500 (new)
FVS318N (new)
MBRN3000 (new)
R6400
R7000
R8000
WNR1000
WNR2000
WNR2200 (new)
WNR4000 (new)
WNDR3700 (new)
WNDR4000 (new)
WNDR4300 (new)
WNDR4300-TN (new)
UTM50 (new)
QNAP Devices:
TS251
TS439 Pro
Other QNAP NAS devices running QTS software
TP-Link Devices:
R600VPN
TL-WR741ND (new)
TL-WR841N (new)
Ubiquiti Devices:
NSM2 (new)
PBE M5 (new)
UPVEL Devices:
Unknown Models (new)
ZTE Devices:
ZXHN H108N (new)