The WannaCry and NotPetya outbreaks were by far among the most significant digital attack campaigns that took place in 2017. Together, the crypto-ransomware and wiper malware affected hundreds of thousands of computers all over the world. They achieved this reach by abusing EternalBlue. Allegedly developed by the U.S. National Security Agency (NSA) and leaked online by the Shadow Brokers, EternalBlue exploits the Microsoft Server Message Block (SMB), which allowed WannaCry and NotPetya to move laterally from a single point of infection to other vulnerable network machines.
EternalBlue will forever enjoy the notoriety of WannaCry and NotPeta’s destruction. Even so, it’s not the only SMB-based exploit that the Shadow Brokers dumped online. There are three other exploits in particular that digital attackers might prefer over EternalBlue because of how they work. To make matters worse, these exploits have been rewritten and stabilized in a way that makes them effective against a wider range of still-unpatched Windows systems.
Indeed, a GitHub user known as “zerosum0x0” has written a post discussing EternalSynergy, EternalRomance, and EternalChampion. These exploits have been changed to work against all vulnerable targets Windows 2000 through 2016 along with all standard home and workstation counterparts.
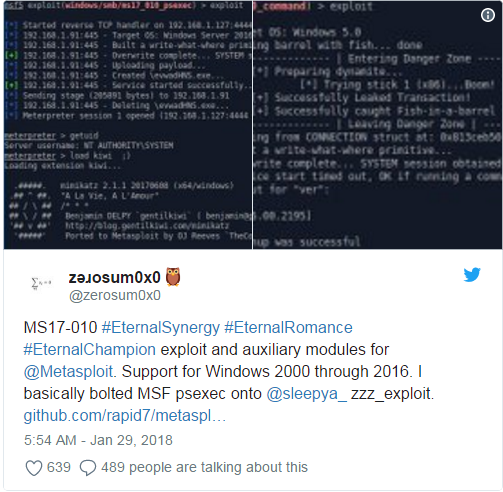
Each of the revised exploits boast remote command and code execution modules that rely on the zzz_exploit adaptation in that they exploit the SMB connection session structures to gain Admin/SYSTEM access. Unlike EternalBlue, EternalSynergy, EternalRomance, and EternalChampion do not use kernel shellcode to stage Meterpreter. Someone could still stage Meterpreter, a payload which comes with the Metasploit penetration testing software, but they would likely need to evade their payloads.
That’s not the only change that differentiates these three rewritten exploits from EternalBlue. As zerosum0x0 explains
To read the original article:https://www.tripwire.com/state-of-security/security-data-protection/cyber-security/three-leaked-nsa-exploits-rewritten-affect-windows-oses-since-windows-2000/
