A new ransomware named AVCrypt has been discovered that tries to uninstall existing security software before it encrypts a computer. Furthermore, as it removes numerous services, including Windows Update, and provides no contact information, this ransomware may be a wiper.
After analysis by MalwareHunterTeam, who discovered the ransomware, myself, and Michael Gillespie, it was decided to name this ransomware AVCrypt as the sample file names are av2018.exe. The developer, though, may be naming it LOL based on some of the debug messages found in the ransomware samples.
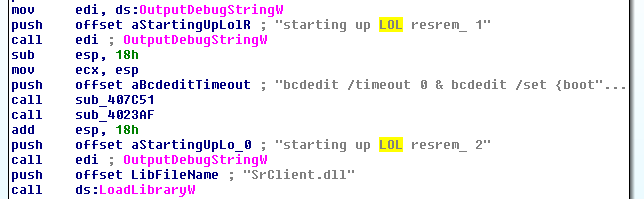
Regardless of what it is called, this infection attempts to uninstall software in a way that we have not seen before. These features are outlined in the sections below.
AVCrypt tries to uninstall your security software
As already stated, when AVCrypt runs it will attempt to remove installed security software from the victim’s computer. It does this in two ways; by specifically targeting Windows Defender and Malwarebytes and by querying for installed AV software and then attempting to remove them.
First AVCrypt will delete Windows services required for the proper operation of Malwarebytes and Windows Defender. It does this using a command like the following format:
cmd.exe /C sc config "MBAMService" start= disabled & sc stop "MBAMService" & sc delete "MBAMService";
It then queries to see what AV software is registered with Windows Security Center and attempts to delete it via WMIC.
cmd.exe /C wmic product where ( Vendor like "%Emsisoft%" ) call uninstall /nointeractive & shutdown /a & shutdown /a & shutdown /a;The above command, though, was not able to uninstall Emsisoft in this manner. It is unknown if it would work with other AV software.
Wiper or In-dev Ransomware?
At this point, it is not clear whether AVCrypt is an in development ransomware or a wiper as there are characteristics that can lead to either categorization.
On the wiper side, this ransomware attempts to delete a variety of Windows services when started. These services are:
MBAMService
MBAMSwissArmy
MBAMChameleon
MBAMWebProtection
MBAMFarflt
ESProtectionDriver
MBAMProtection
Schedule
WPDBusEnum
TermService
SDRSVC
RasMan
PcaSvc
MsMpSvc
SharedAccess
wscsvc
srservice
VSS
swprv
WerSvc
MpsSvc
WinDefend
wuauserv
While Windows will continue to function after these services are deleted, there will likely be issues in the proper operation of Windows.
Furthermore, the ransom notes created by the ransomware do not provide any contact information. They just simply state « lol n ».
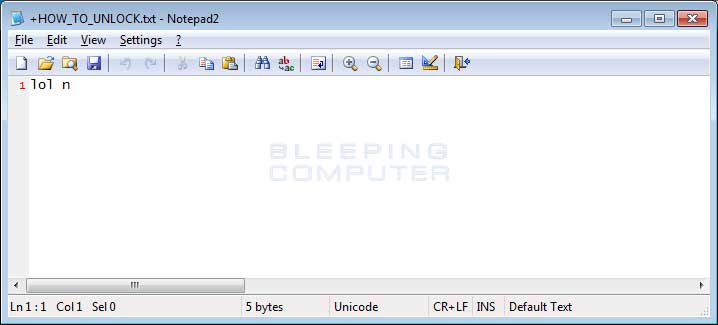
At the same time, this infection does upload the encryption key to a remote TOR site and the contents of the note could simply be a placeholder. Furthermore, when executing the ransomware it displays a alert before it starts and there are numerous debug messages, so it could very well be just an in development ransomware.
Microsoft has told BleepingComputer that they have only detected two samples of this ransomware, with of them possibly being my computer, so they feel that this infection is currently in development. Microsoft is currently detecting it as Ransom:Win32/Pactelung.A.
Already in the wild or just a coincidence?
While I am leaning towards this being an in development ransomware, a security researcher posted on Twitter that computers at a Japanese university were recently infected by a ransomware that also uninstalled antivirus software.
To read the original article:
https://www.bleepingcomputer.com/news/security/the-avcrypt-ransomware-tries-to-uninstall-your-av-software/
