Recently BleepingComputer has received a flurry of support requests for a new ransomware being named StorageCrypt that is targeting NAS devices such as the Western Digital My Cloud. Victims have been reporting that their files have been encrypted and a note left with a ransom demand of between .4 and 2 bitcoins to get their files back.
User’s have also reported that each share on their NAS device contains a Autorun.inf file and a Windows executable named 美女与野兽.exe, which translates to Beauty and the beast. From the samples BleepingComputer has received, this Autorun.inf is an attempt to spread the 美女与野兽.exe file to other computers that open the folders on the NAS devices.
SambaCry being used to infect victims with the StorageCrypt Ransomware
SambaCry is a Linux Samba vulnerability that when exploited, allows an attacker to open a command shell that can be used to download files and execute commands on the affected device. The current method that it is infecting the NAS devices with StorageCrypt appears to be the same as the Elf_Shellbind variant that was previously used to distribute miners.
This time around, attackers are using the vulnerability to install a ransomware called StorageCrypt on the computer. While we still do not have all the samples of this infection, what we do know is that when Samba is exploited, the exploit will execute a command that downloads a file called sambacry, stores it in the /tmp folder as apaceha, and then executes it.

It is not currently know if this executable is the one that installs StorageCrypt or is used as a backdoor for later access.
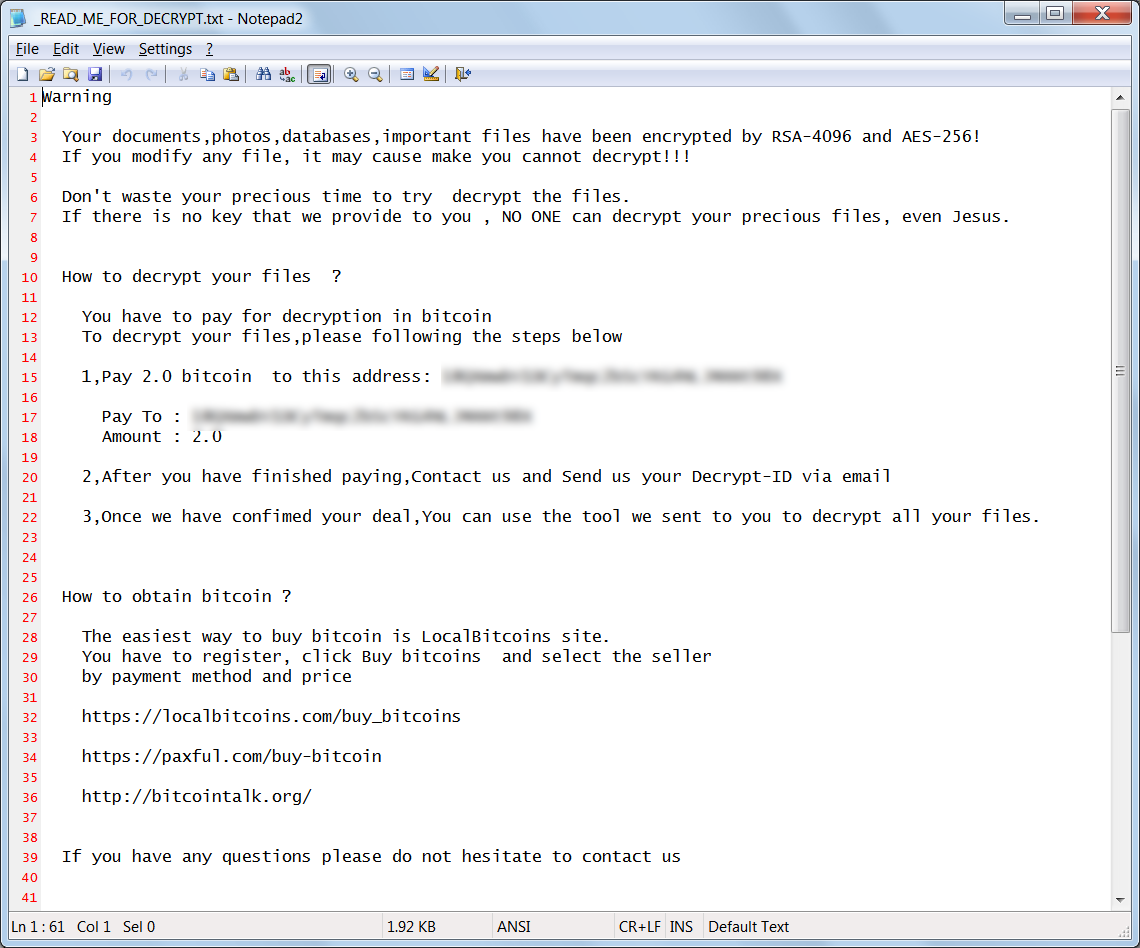
Ultimately, StorageCrypt will be installed and all the files on the NAS will be encrypted. When a file is encrypted it will be renamed so that the .locked extension is appended to the filename. The ransomware will also drop a ransom note named _READ_ME_FOR_DECRYPT.txt that contains the ransom amount, the bitcoin address to send payment to, and the email address JeanRenoAParis@protonmail.com to contact after payment.
As previously stated, the infection will also add Autorun.inf and 美女与野兽.exe files to each folder on the NAS. This is an attempt to infect other computers that open these folders with an infection.
At the time of this writing, one of the bitcoin addresses used in the ransom notes has received an incoming transfer of 1 bitcoin. It is unknown if this is a ransom payment or not.
As this ransomware is still being analyzed, if new information is discovered BleepingComputer will update this article.
How to protect yourself from SambaCry
As SambaCry targets vulnerabilities in the Samba protocol, it is important to not have any of the your NAS devices connected directly to the Internet. If a device is connected to the Internet, while you will be able to stream and access your files, it will also be wide open for attackers to exploit.
Instead you should place your NAS behind a firewall and configure a VPN into your network. This allows you to access your NAS and the files stored on it in a secure manner.
To read the original article :