Exploit broker Zerodium is offering rewards of up to $500,000 for zero-days in UNIX-based operating systems like OpenBSD, FreeBSD, NetBSD, but also for Linux distros such as Ubuntu, CentOS, Debian, and Tails.
The offer, first advertised via Twitter earlier this week, is available as part of the company’s latest zero-day acquisition drive. Zerodium is known for buying zero-days and selling them to government agencies and law enforcement.
The company runs a regular zero-day acquisition program through its website, but it often holds special drives with more substantial rewards when it needs zero-days of a specific category.
BSD zero-day rewards will be on par with Linux payouts
The US-based company held a previous drive with increased rewards for Linux zero-days in February, with rewards going as high as $45,000.
In another zero-day acquisition drive announced on Twitter this week, the company said it was looking again for Linux zero-days, but also for exploits targeting BSD systems. This time around, rewards can go up to $500,000, for the right exploit.
Zerodium told Bleeping Computer they’ll be aligning the temporary rewards for BSD systems with their usual payouts for Linux distros.
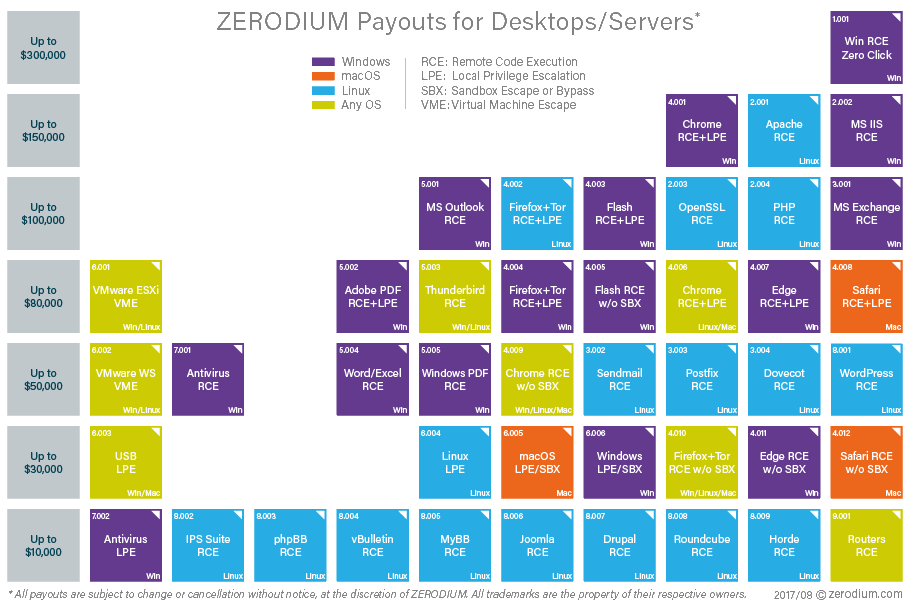
The company’s usual payouts for Linux privilege escalation exploits can range from $10,000 to $30,000. Local privilege escalation (LPE) rewards can even reach $100,000 for « an exploit with an exceptional quality and coverage, » such as, for example, a Linux kernel exploit affecting all major distributions.
Payouts for Linux remote code execution (RCE) exploits can bring in from $50,000 to $500,000 depending on the targeted software/service and its market share. The highest rewards are usually awarded for LPEs and RCEs affecting CentOS and Ubuntu distros.
Zero-day price varies based on exploitation chain
The acquisition price of a submitted zero-day is directly tied to its requirements in terms of user interaction (no click, one click, two clicks, etc.), Zerodium said.
Other factors include the exploit reliability, its success rate, the number of vulnerabilities chained together for the final exploit to work (more chained bugs means more chances for the exploit to break unexpectedly), and the OS configuration needed for the exploit to work (exploits are valued more if they work against default OS configs).
Prior to the recent acquisition drive targeting BSD systems, Zerodium has held other drives for zero-day exploits targeting iOS 9, iOS 10, Adobe Flash Player, mobile IM apps, the Tor Browser, web-hosting software, Microsoft Outlook, Android, and Linux.
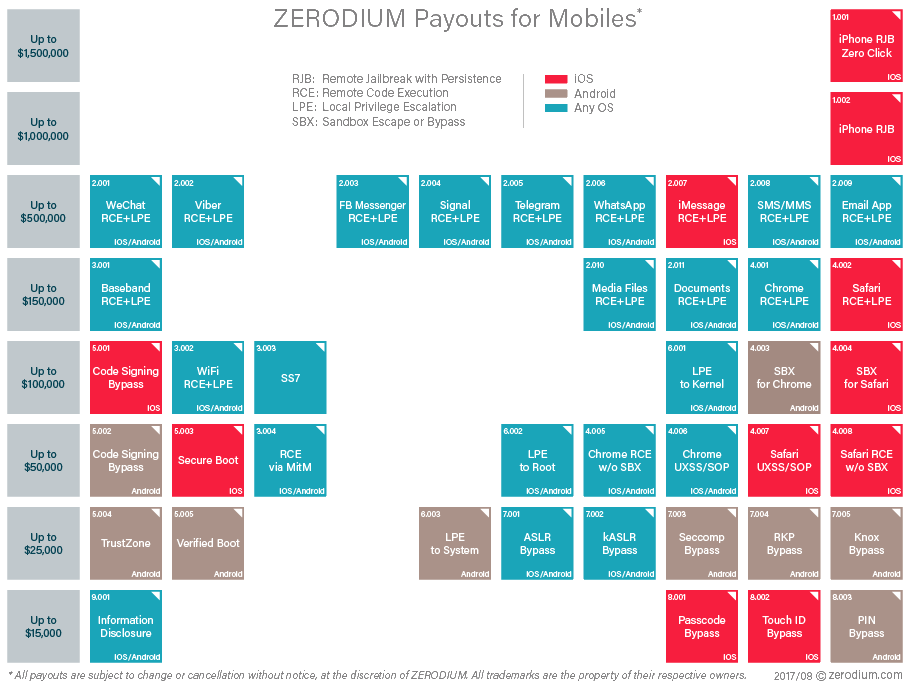
The company made a name for itself in 2015 when it held acquisition drives offering exorbitant prizes for iOS zero-days of up to $1.5 million. Those rewards are now part of the company’s standard price chart, with a remote jailbreak with persistence exploit targeting iPhone devices being valued at the same $1.5 million.
 |
 |
Zero-days in servers « can reach exceptional amounts »
« Price difference between systems is mostly driven by market shares, » Zerodium founder Chaouki Bekrar told Bleeping Computer via email.
« For Desktop environments, as Windows leads the market, exploits for Windows are usually more valuable than Linux, » he says, « however for Server environments, Linux attracts more interest from customers and the rewards can reach exceptional amounts. »
« Obviously, mobile exploits remain the most expensive and most valuable assets in our industry, due to their market penetration and usefulness from an operational perspective, » Bekrar added.
Asked about the logic behind these acquisition drives that pay increased rewards, Bekrar told Bleeping Computer the following.
« Our aim is to always have, at any time, two or more fully functional exploits for every major software, hardware, or operating systems, meaning that from time to time we would promote a specific software/system on our social media to acquire new codes and strengthen our existing capabilities or extend them.
« We may also react to customers’ requests and their operational needs, » Bekrar said.
It’s becoming a crowded market
Since Zerodium drew everyone’s attention to the exploit brokerage market in 2015, the market has gotten more and more crowded, but also more sleazy, with some companies being accused of selling zero-days to government agencies in countries with oppressive or dictatorial regimes, where they are often used against political oponents, journalists, and dissidents, instead of going after real criminals.
The latest company who broke into the zero-day brokerage market is Crowdfense, who recently launched an acquisition program with prizes of $10 million, of which it already paid $4.5 million to researchers.
To read the original article:
