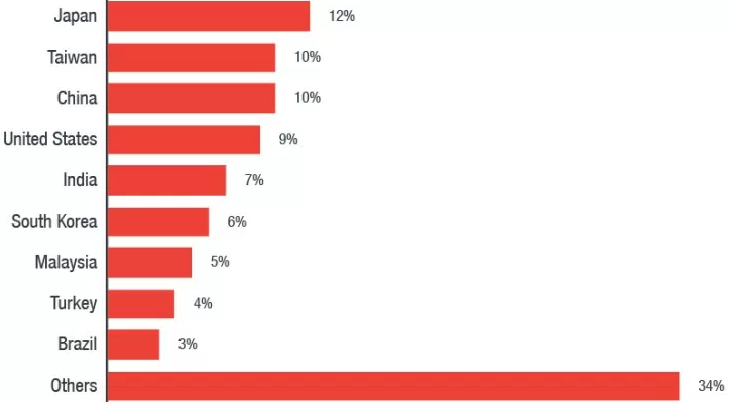
Security experts at Cisco Talos discovered a new piece of malware dubbed GoScanSSH that was being used to compromise SSH servers exposed online. Security researchers at Cisco Talos have discovered a new piece of malware dubbed GoScanSSH that was being used to compromise SSH servers exposed online. The malicious code was written in […]
Britain Backs US Hacking Allegations Against Iranians
The British government says it concurs with charges contained in an indictment announced Friday by the U.S. Department of Justice against multiple Iranians. The indictment, unsealed Friday, charges nine Iranian nationals with stealing more than 31 terabytes of data from 320 universities in 22 countries – including 144 U.S. institutions […]
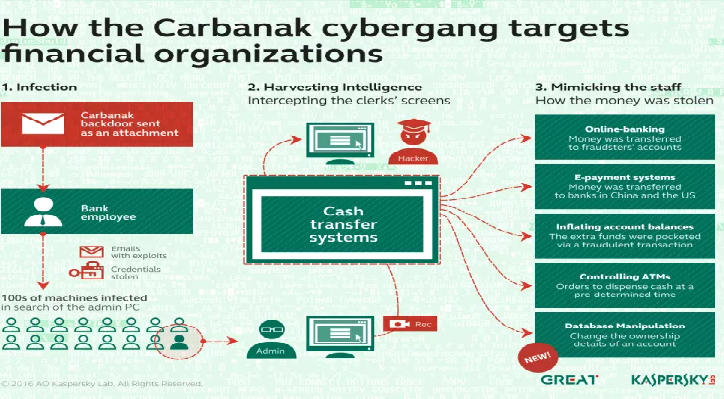
Law enforcement arrested the head of the Carbanak gang that stole 1 billion from banks
The head of the crime ring behind the Carbanak gang that since 2013 targeted banks worldwide has been arrested in Spain. The mastermind suspected of stealing about £870m (€1bn) in a bank cyber heist has been arrested in Spain. The man is suspected to be the kingpin of the crime ring behind the Carbanak […]
MOZILLA TESTS DNS OVER HTTPS: MEETS SOME PRIVACY PUSHBACK
The Mozilla Foundation is testing a new mechanism for securing domain name server traffic that uses the encrypted HTTPS channel. It is an attempt to speed up the internet, reduce the threat of man-in-the-middle attacks and keep prying eyes from monitoring what users do online. Starting in the next several […]
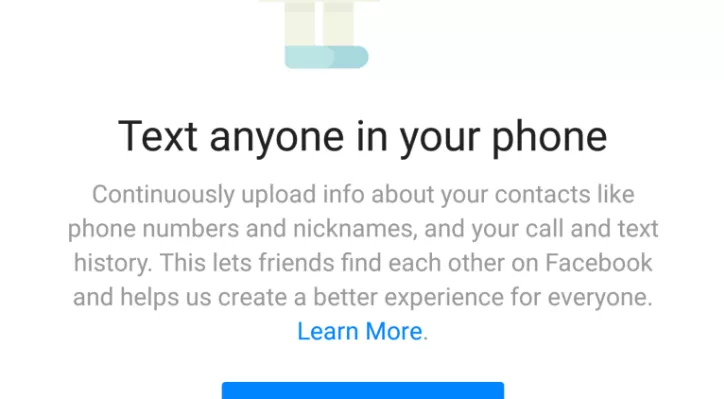
Facebook collected call and SMS data from Android users if not explicitly forbidden
After the Cambridge Analytica scandal, Facebook made the headlines again, the company collected users’ Android call and SMS metadata for years. The Cambridge Analytica case it raised the discussion about the power of social networks and the possibility of their abuse for the conditioning of political activities. The non-professionals have discovered how important their […]
Do you have what it takes to withstand modern DDoS attacks?
As the latest record DDoS attack hit GitHub and threatened to overwhelm its edge network, the popular Git-repository hosting service quickly switched to routing the attack traffic to their DDoS mitigation service. In the end, GitHub ended up completely unavailable for five minutes and intermittently unavailable for four. But […]
Emails de phishing Apple : des faux messages cencés provenir d’iTunes et de l’App Store
Récemment, l’apparition d’une nouvelle attaque de phishing a fait son apparition. Elle se présentait sous la forme de faux messages de renouvellement d’abonnement à l’App Store, qui s’avéraient être des emails de phishing imitant les emails officiels d’Apple. Vous avez déjà reçu un email qui ressemble à s’y méprendre à […]
IETF Approves TLS 1.3 as Internet Standard
IETF Approves TLS 1.3 as Internet Standard The Internet Engineering Task Force (IETF) —the organization that approves proposed Internet standards and protocols— has formally approved TLS 1.3 as the next major version of the Transport Layer Security (TLS) protocol. The decision comes after four years of discussions and 28 protocol drafts, with […]
A new massive cryptomining campaign target Linux servers exploiting old flaw
Trend Micro uncovered a new crypto mining campaign targeting Linux servers that exploit the CVE-2013-2618 flaw in Cacti’s Network Weathermap plug-in, which system administrators use to visualize network activity. Security firm Trend Micro uncovered new crypto mining campaign, a cybercriminal gang has made nearly $75,000 by installing a Monero miner […]
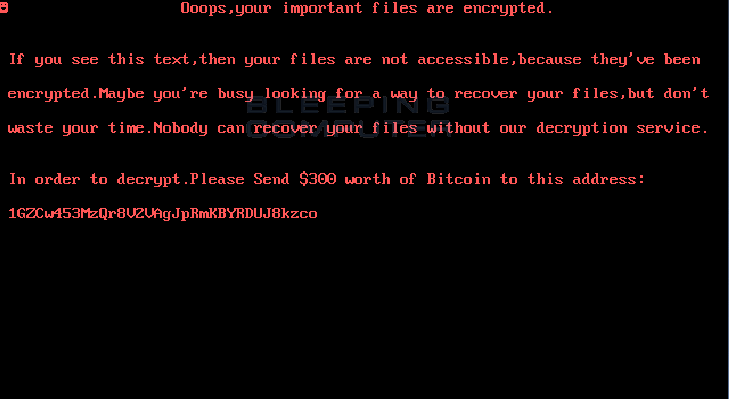
The DiskWriter or UselessDisk BootLocker May Be A Wiper
A new MBR bootlocker called DiskWriter, or UselessDisk, has been discovered that overwrites the MBR of a victim’s computer and then displays a ransom screen on reboot instead of booting into Windows. This ransom note asks for $300 in bitcoins in order to gain access to Windows again. Ransom Screen First […]